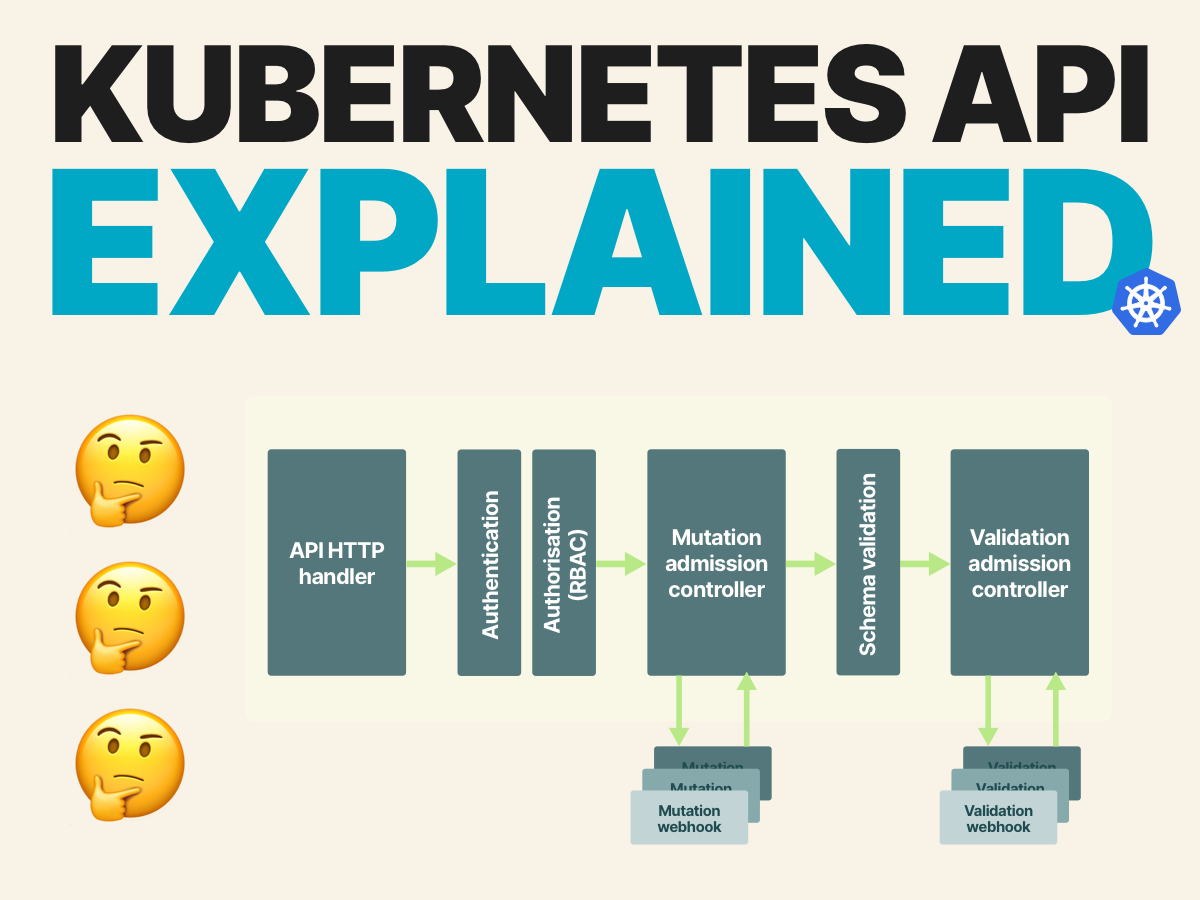
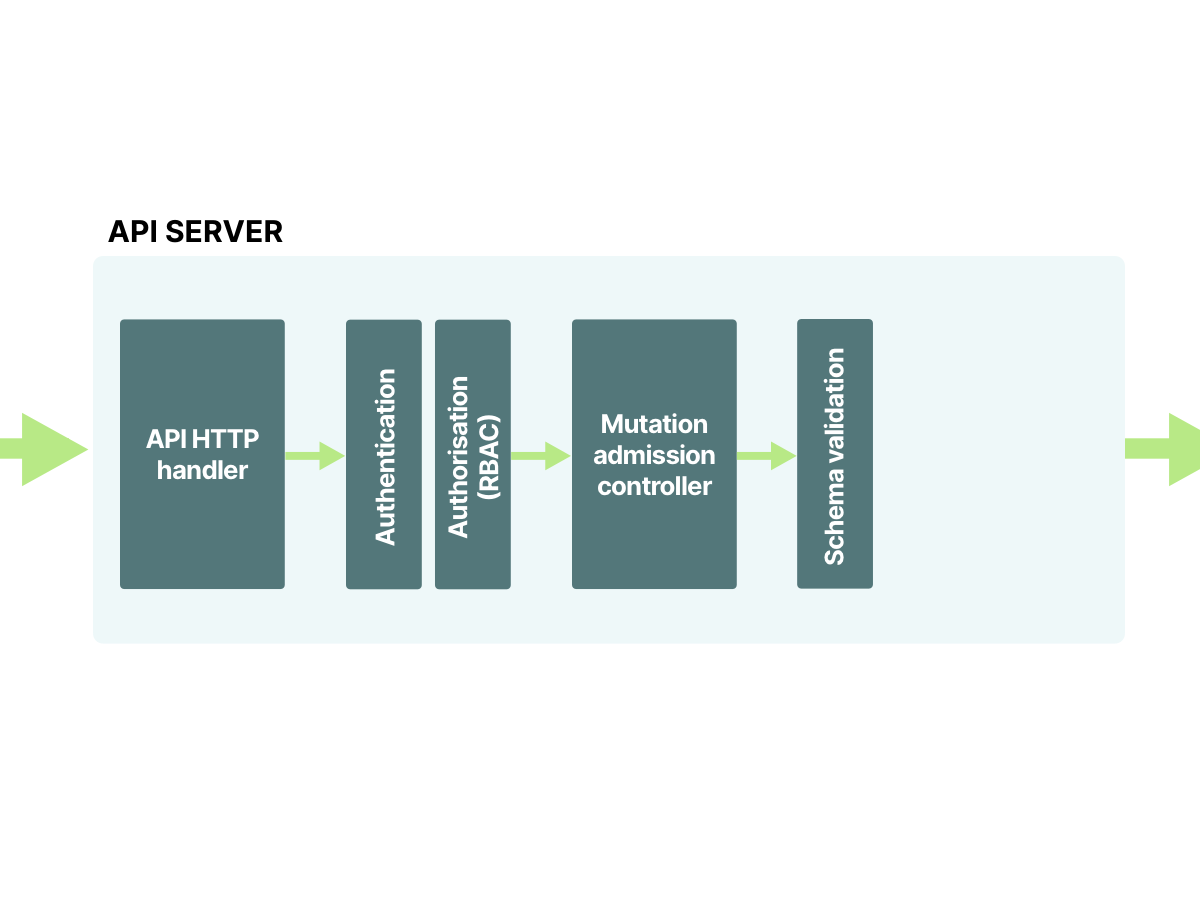
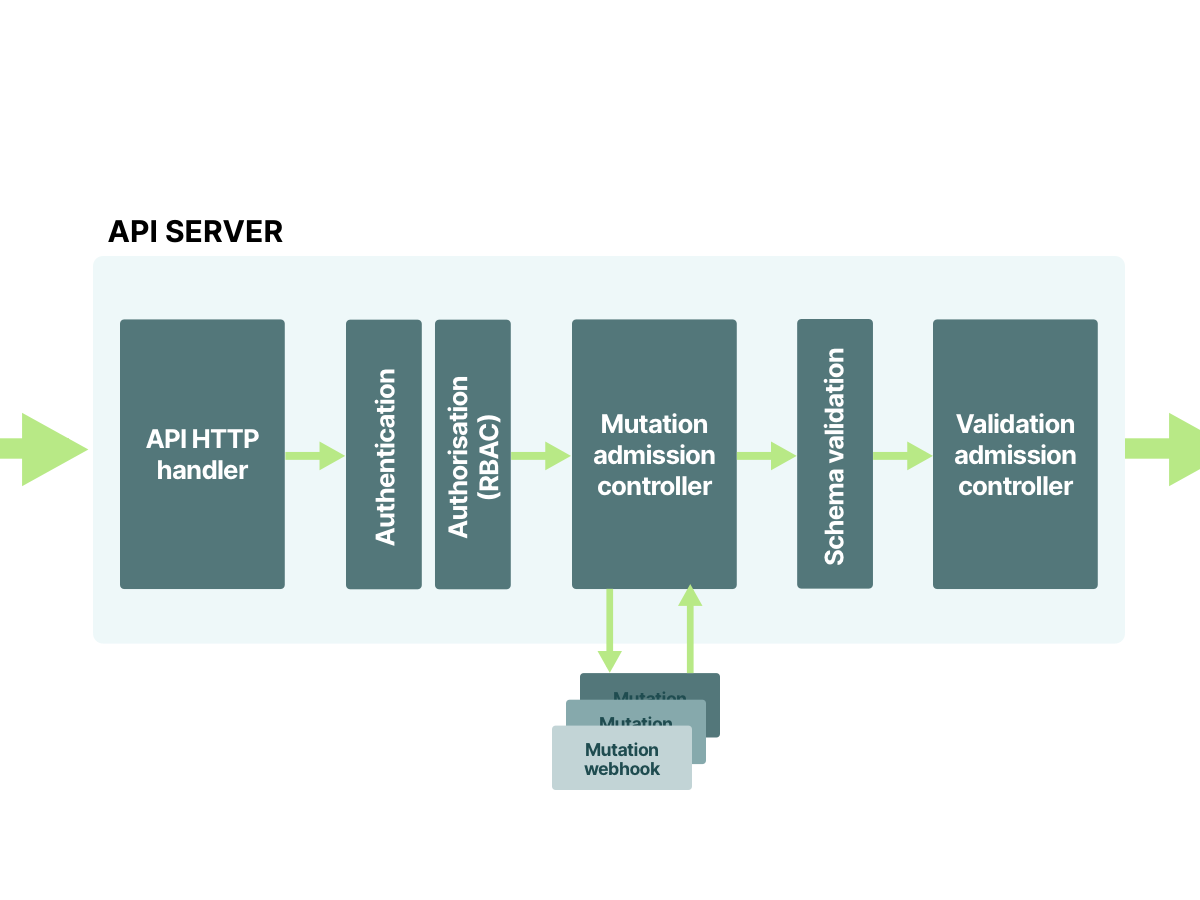
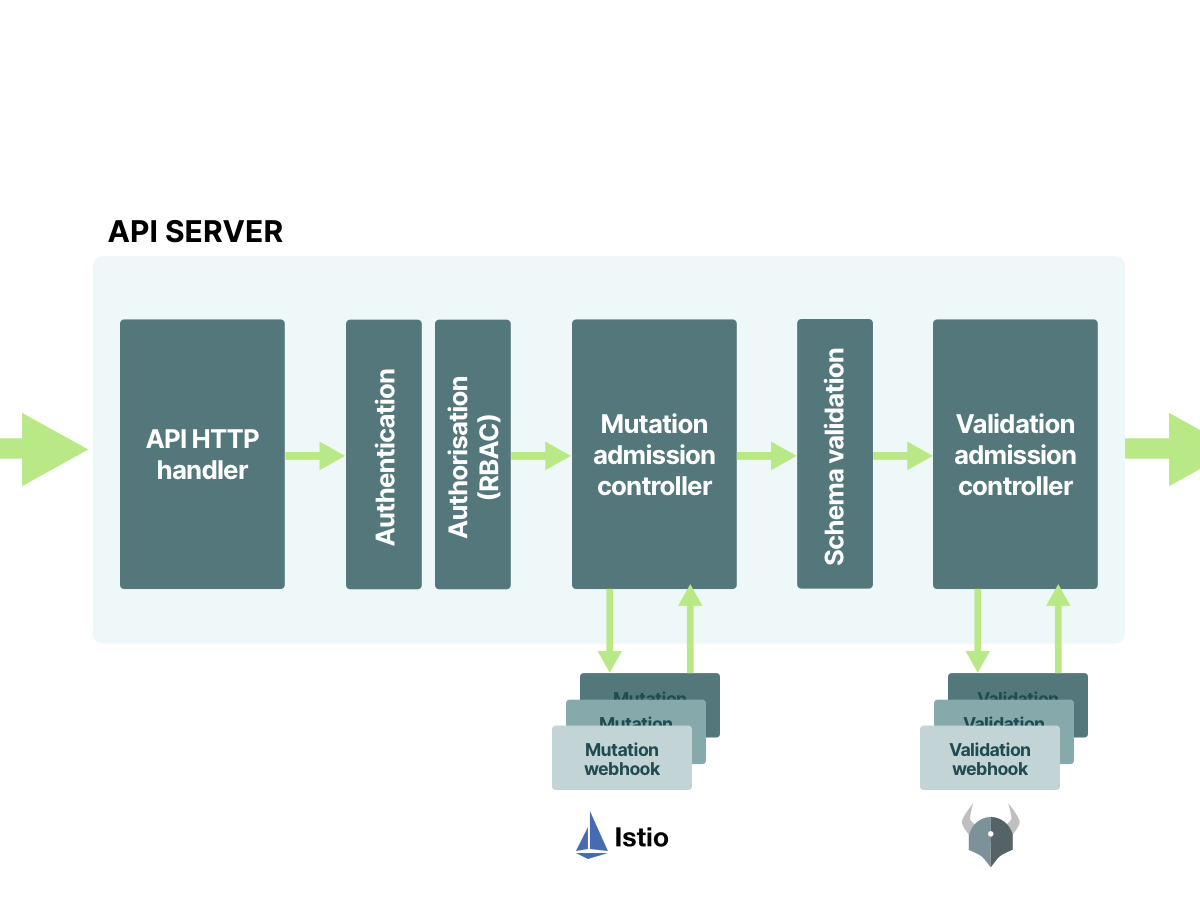
10/10
If you wish to explore more, check out this article on custom admission controllers banzaicloud.com
Also @echorand is about to publish an article on the Learnk8s blog about custom validation checks. Subscribe to the Learnk8s newsletter here learnk8s.io
If you wish to explore more, check out this article on custom admission controllers banzaicloud.com
Also @echorand is about to publish an article on the Learnk8s blog about custom validation checks. Subscribe to the Learnk8s newsletter here learnk8s.io
Loading suggestions...