1. Welcome to the world of surveillance contractors, telecom access brokers, and an industry of grey actors with seemingly legitimate businesses. Some are regulated, some are procured by state clients - and some are sold to private actors, providing hackers and criminals alike state-like capabilities. Where Snowden’s revelations focused on a few government-run mass surveillance hubs like the American NSA and Britain’s GCHQ, the emerging picture a decade later is of an increasingly diverse, outsourced private industry a globalized start-up economy of location trackers, password crackers, and data extractors. Among its clients and their victims States and their common citizens.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
2. At the center of this global telecom surveillance web is a tech expert and telecom entrepreneur, a former ally of Julian Assange and vocal critic of the security state, now turned surveillance industry enabler.
His name is Andreas Fink.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
His name is Andreas Fink.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
3. Andreas Fink has built a surveillance apparatus that he has put at the disposal of governments and companies around the world including Israel’s Rayzone Group, a top-tier cyber intelligence company. Fink’s set-up is capable of exploiting loopholes in mobile phone connection protocols to track the location of phone users and even redirect their SMS messages to crack internet accounts.
#Assange #Snowden #surveillance #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
4. A computer and telecommunications engineer, Fink is a former payment processor for Wikileaks, an entrepreneur who supports the libertarian Pirate Party but masterminds a global surveillance infrastructure that he has placed at the disposal of governments and companies, including top Israeli commercial spy firms. It allows his customers to pinpoint the location of mobile phones the world over to the level of the cell tower. It has also facilitated the interception of messages and the takeover of internet accounts.
#Assange #Snowden #surveillance #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #USA #UK #spying #TechSurveillance #China #Russia
5. Andreas Fink offers his customers the ability to use a highly customizable interface, called Venotex, to send tracking requests via a roster of phone network access points that he maintains. Venotex was the system seemingly linked to the software used by Team Jorge. Fink always denied working with Team Jorge but confirmed to underground reporters that a “customer” had once wanted to pay him through a company owned by them.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
6. One of Fink’s systems was seen in the system used by the Israeli hacker-for-hire and disinformation group Team Jorge as part of their operations, which required access to the global cellular network. An international investigation led by underground journalists revealed that Team Jorge offered mass-social-media manipulation, election interference, and even hijacking email, Telegram, and web accounts. In the past, over 20 members of the Israeli crypto community had their Telegram accounts hacked in a similar manner by someone using Fink’s infrastructure.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
(Team Jorge Founder Tal Hanan)
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
(Team Jorge Founder Tal Hanan)
7. When underground reporters asked about his role as an access broker exploiting telecom networks, Fink said: “I’m by far not the only kid on the block”. He cited “bigger companies with fewer scruples” including NSO Group, FinFisher, and Hacking Team, and said that “Israel, Russia, China, India have plenty of them.”
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
mediapart.fr
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
mediapart.fr
8. Andreas Fink has offered location tracking services to multiple governments and companies, directly and through intermediaries. In Africa, he pitched projects in Mali and the Democratic Republic of Congo and provided technical assistance to a service provider for a government agency in Tanzania. Leaked online communications reveal that he also offered location tracking services to undisclosed customers of another company, in one case providing the latitude and longitude of someone in Sub-Saharan Africa.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
9. Among his current customers is Rayzone Group, a high-end Israeli surveillance company that sells a “remote and undetectable” location tracking tool called Geomatrix. The firm was implicated in the operation to recapture fleeing Emirati princess Latifa al-Maktoum as she attempted to escape from her father in Dubai in 2018. Rayzone denied the claim.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
10. Fink has also in the past worked with two other Israeli surveillance firms, Verint and Septier, both of which offer location-tracking services to government agencies. These companies tested his systems “but it never came to a viable long-term business."
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
12. Global span of Hire for pay Mobile Surveillance
In the Democratic Republic of the Congo, he demonstrated his surveillance system to intelligence officials. The demo involved him pinpointing the location of an individual who, the officials said, operated an anonymous defamatory anti-government Facebook account. Approaching a phone company employee via social media, he offered $1000 per month for access to the employee’s West African phone network – access which he intended to use to track suspects in war-torn Mali. In Southeast Asia and Israel, his systems were used to take over Telegram and other accounts by redirecting SMSs used to secure them. In Guerrero, Mexico, a trace shows an effort to extract personal data, including location data, from a journalist’s phone. The next day, the journalist was shot dead. The trace goes back to a global title leased by Fink, although he says he was not using it at that time.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
In the Democratic Republic of the Congo, he demonstrated his surveillance system to intelligence officials. The demo involved him pinpointing the location of an individual who, the officials said, operated an anonymous defamatory anti-government Facebook account. Approaching a phone company employee via social media, he offered $1000 per month for access to the employee’s West African phone network – access which he intended to use to track suspects in war-torn Mali. In Southeast Asia and Israel, his systems were used to take over Telegram and other accounts by redirecting SMSs used to secure them. In Guerrero, Mexico, a trace shows an effort to extract personal data, including location data, from a journalist’s phone. The next day, the journalist was shot dead. The trace goes back to a global title leased by Fink, although he says he was not using it at that time.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
13. So how this web of mobile spying works?
Central to understanding the Adreas Fink's operation is a list of network access points, called “global titles”. These GTs are not only operated by telephone service providers but also leased by private companies from SMS vendors to surveillance actors. GTs look like phone numbers. They send and receive data allowing phones to communicate with each other. Traffic through phone networks such as requesting location info on a device can be observed as coming from a particular GT. Who owns or uses a particular GT is not always obvious, however, even to insiders.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
Central to understanding the Adreas Fink's operation is a list of network access points, called “global titles”. These GTs are not only operated by telephone service providers but also leased by private companies from SMS vendors to surveillance actors. GTs look like phone numbers. They send and receive data allowing phones to communicate with each other. Traffic through phone networks such as requesting location info on a device can be observed as coming from a particular GT. Who owns or uses a particular GT is not always obvious, however, even to insiders.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
14. SS7 and hacking the locations and SMSs details on behalf of espionage clients
There's also evidence of successful SMS interceptions conducted over Finks infrastructure. Fink's systems carried out frequent and sustained attempts to extract information, including location information, from phones in Africa, Asia, and the EU using SS7 Mobile network loopholes. Fink attributed the activity to legally entitled government agencies.
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
There's also evidence of successful SMS interceptions conducted over Finks infrastructure. Fink's systems carried out frequent and sustained attempts to extract information, including location information, from phones in Africa, Asia, and the EU using SS7 Mobile network loopholes. Fink attributed the activity to legally entitled government agencies.
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
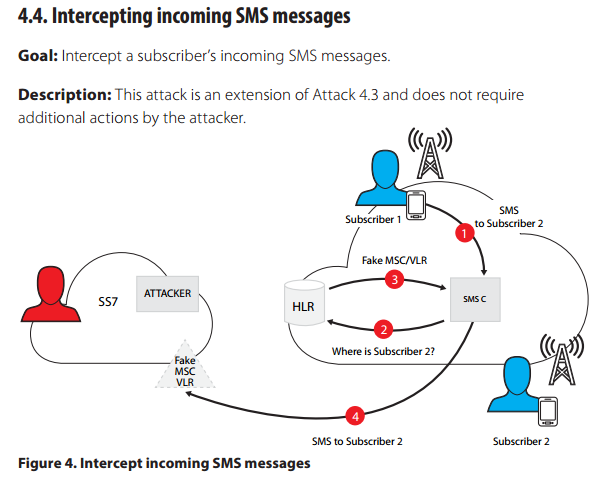
15. How SS7 Attack works to hack SMSs and geolocation:
SS7 attacks are mobile cyber attacks that exploit security vulnerabilities in the SS7 protocol to compromise and intercept voice and SMS communications on a cellular network. Similar to a Man In the Middle attack, SS7 attacks target mobile phone communications rather than wifi transmissions.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
SS7 attacks are mobile cyber attacks that exploit security vulnerabilities in the SS7 protocol to compromise and intercept voice and SMS communications on a cellular network. Similar to a Man In the Middle attack, SS7 attacks target mobile phone communications rather than wifi transmissions.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
16. Step 1 of SS7 Mobile Network Hacking
S7 attacks exploit the authentication capability of communication protocols running atop the SS7 protocol to eavesdrop on voice and text communications. All a cybercriminal would need to successfully launch an SS7 attack are a computer running Linux and the SS7 SDK – both free to download from the Internet.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
S7 attacks exploit the authentication capability of communication protocols running atop the SS7 protocol to eavesdrop on voice and text communications. All a cybercriminal would need to successfully launch an SS7 attack are a computer running Linux and the SS7 SDK – both free to download from the Internet.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
17. Step 2 of SS7 Mobile Network Hacking
Once connected to an SS7 network, the hacker can target subscribers on the network while fooling the network into thinking the hacker device is actually an MSC/VLR node. When a hacker successfully performs a MitM phishing attack, they gain access to the same amounts and types of information that are usually reserved for the use of security services. Having the ability to eavesdrop on calls and text messages, as well as device locations empowers hackers to gain valuable information.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
Once connected to an SS7 network, the hacker can target subscribers on the network while fooling the network into thinking the hacker device is actually an MSC/VLR node. When a hacker successfully performs a MitM phishing attack, they gain access to the same amounts and types of information that are usually reserved for the use of security services. Having the ability to eavesdrop on calls and text messages, as well as device locations empowers hackers to gain valuable information.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
18. Two-factor authentication a common security precaution used by many is one of the targets of SS7 attacks. Two-factor authentication (also known as 2FA) via SMS using SS7 is inherently flawed as these SMS messages are unencrypted and hackers know how to intercept them. With the code from the SMS in their hand, a cyber-criminal can potentially reset your password to Google, Facebook, WhatsApp account, or even your bank account.
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
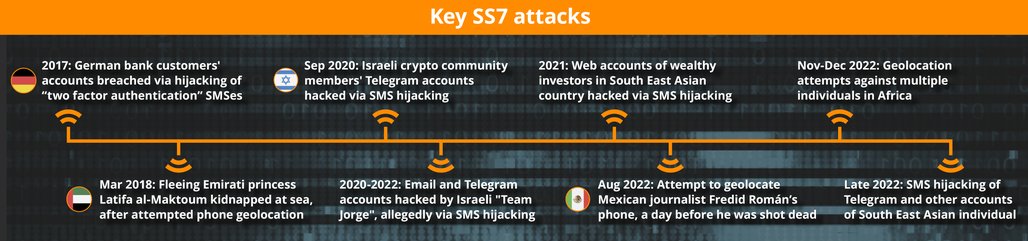
19. Major SS7 Attacks
In 2021 a security analyst saw some unusual activity in Southeast Asia. An attacker tried to access internet accounts belonging to wealthy investors in the country, using a technique to redirect security SMSs to the attacker. Some of these attacks succeeded, the analyst said, speaking on condition of anonymity. Incident logs show that although the attack came from a phone operator in the Pacific region, the messages were routing via that operator to Adreas Fink. Late in 2022, another analyst saw SMS authentications for a Telegram account and other internet accounts belonging to a single individual in another South-East Asian country being redirected to a global title in Sweden belonging to Fink. Minutes after the SS7 request was sent, the attackers received the key they needed to access the victim's Telegram account: the one-time log-in code used to register a second device. Such activity recurred early in 2023.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
In 2021 a security analyst saw some unusual activity in Southeast Asia. An attacker tried to access internet accounts belonging to wealthy investors in the country, using a technique to redirect security SMSs to the attacker. Some of these attacks succeeded, the analyst said, speaking on condition of anonymity. Incident logs show that although the attack came from a phone operator in the Pacific region, the messages were routing via that operator to Adreas Fink. Late in 2022, another analyst saw SMS authentications for a Telegram account and other internet accounts belonging to a single individual in another South-East Asian country being redirected to a global title in Sweden belonging to Fink. Minutes after the SS7 request was sent, the attackers received the key they needed to access the victim's Telegram account: the one-time log-in code used to register a second device. Such activity recurred early in 2023.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
20. Major SS7 Attacks
In two earlier cases, U.K. GTs registered to Adreas Fink’s bankrupt former company, SMSRelay, were also implicated in account takeover attacks, this time specifically aimed at financial assets of phone users. In 2017 a group of bank customers lost money following breaches of their accounts in Germany. In 2020, over twenty Israeli cryptocurrency investors were targeted for stealing digital currency. In each case a specific victim was targeted: the attackers used global titles from the U.K., allocated to SMSRelay, to hijack their Telegram accounts using a simple trick, registering a second device and intercepting its login verification messages.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
In two earlier cases, U.K. GTs registered to Adreas Fink’s bankrupt former company, SMSRelay, were also implicated in account takeover attacks, this time specifically aimed at financial assets of phone users. In 2017 a group of bank customers lost money following breaches of their accounts in Germany. In 2020, over twenty Israeli cryptocurrency investors were targeted for stealing digital currency. In each case a specific victim was targeted: the attackers used global titles from the U.K., allocated to SMSRelay, to hijack their Telegram accounts using a simple trick, registering a second device and intercepting its login verification messages.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
21. Death delivered at your doorstep through your mobile
in January 2021 Fink leased access to more than a dozen global titles from phone networks in the Pacific Ocean in Vanuatu, Samoa, Tonga, Papua New Guinea and Fiji. The following year, on 21 August, according to confidential network data, one of these was used to target a phone number linked to the Mexican journalist Fredid Román, hours before his murder. The request was an attempt to extract information from the network which could subsequently be used to pinpoint his location or other data about his device.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
in January 2021 Fink leased access to more than a dozen global titles from phone networks in the Pacific Ocean in Vanuatu, Samoa, Tonga, Papua New Guinea and Fiji. The following year, on 21 August, according to confidential network data, one of these was used to target a phone number linked to the Mexican journalist Fredid Román, hours before his murder. The request was an attempt to extract information from the network which could subsequently be used to pinpoint his location or other data about his device.
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
22. An example of "How Global surveillance and espionage work"
1. Jet linked to Israeli spyware tycoon brings spy tech from EU to notorious Sudanese militia
2. Israeli iPhones hacked with NSO’s Pegasus spyware twice in two years
3. The Israelis destabilizing democracy and disrupting elections worldwide
4. As Israel reins in its cyber arms industry, an ex-intel officer is building a new empire
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
1. Jet linked to Israeli spyware tycoon brings spy tech from EU to notorious Sudanese militia
2. Israeli iPhones hacked with NSO’s Pegasus spyware twice in two years
3. The Israelis destabilizing democracy and disrupting elections worldwide
4. As Israel reins in its cyber arms industry, an ex-intel officer is building a new empire
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
23. An example of "How Global surveillance and espionage work"
5. Pegasus spyware maker NSO has 22 clients in the European Union. And it's not alone.
6. Israeli spy tech sold to Bangladesh, despite dismal human rights record
7. Israel's Cyber-spy Industry Helps Dictators Hunt Dissidents and Gays
8. Circles, one of Israel’s first offensive cyber firms that were merged into NSO, provided geolocation services in a similar manner, and it was recently revealed that the U.S. purchased a geolocation system called landmark from the Israeli spyware maker.
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
5. Pegasus spyware maker NSO has 22 clients in the European Union. And it's not alone.
6. Israeli spy tech sold to Bangladesh, despite dismal human rights record
7. Israel's Cyber-spy Industry Helps Dictators Hunt Dissidents and Gays
8. Circles, one of Israel’s first offensive cyber firms that were merged into NSO, provided geolocation services in a similar manner, and it was recently revealed that the U.S. purchased a geolocation system called landmark from the Israeli spyware maker.
#Assange #Snowden #surveillance #CIA#MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
24. So if you think that your logins and passwords are secure and safe, double check and READ MY THREAD HERE😂 to understand that you might be HACKED...!!!
From anywhere, anytime, by anyone with a Linux system and internet connection!!!
Stay Alert
Stay Safe
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
From anywhere, anytime, by anyone with a Linux system and internet connection!!!
Stay Alert
Stay Safe
#Assange #Snowden #surveillance #CIA #MOSAD #MI6 #USA #UK #spying #TechSurveillance #China #Russia
Loading suggestions...