I promised to walk someone through our Truth&Trust Online #TTOCon (thanks @TTOConference!) poster on "left-of-boom misinfosec" yesterday, but we missed the slot. I hate to disappoint, so here's your online version...
First, the people. It's taken a lot of skills and specialisations to create misinfosec. @grayspective and myself are listed on this poster, but this is work from @Ngree_H0bit @TheLoki47 and community across @credcoalition @misinfosec and beyond.
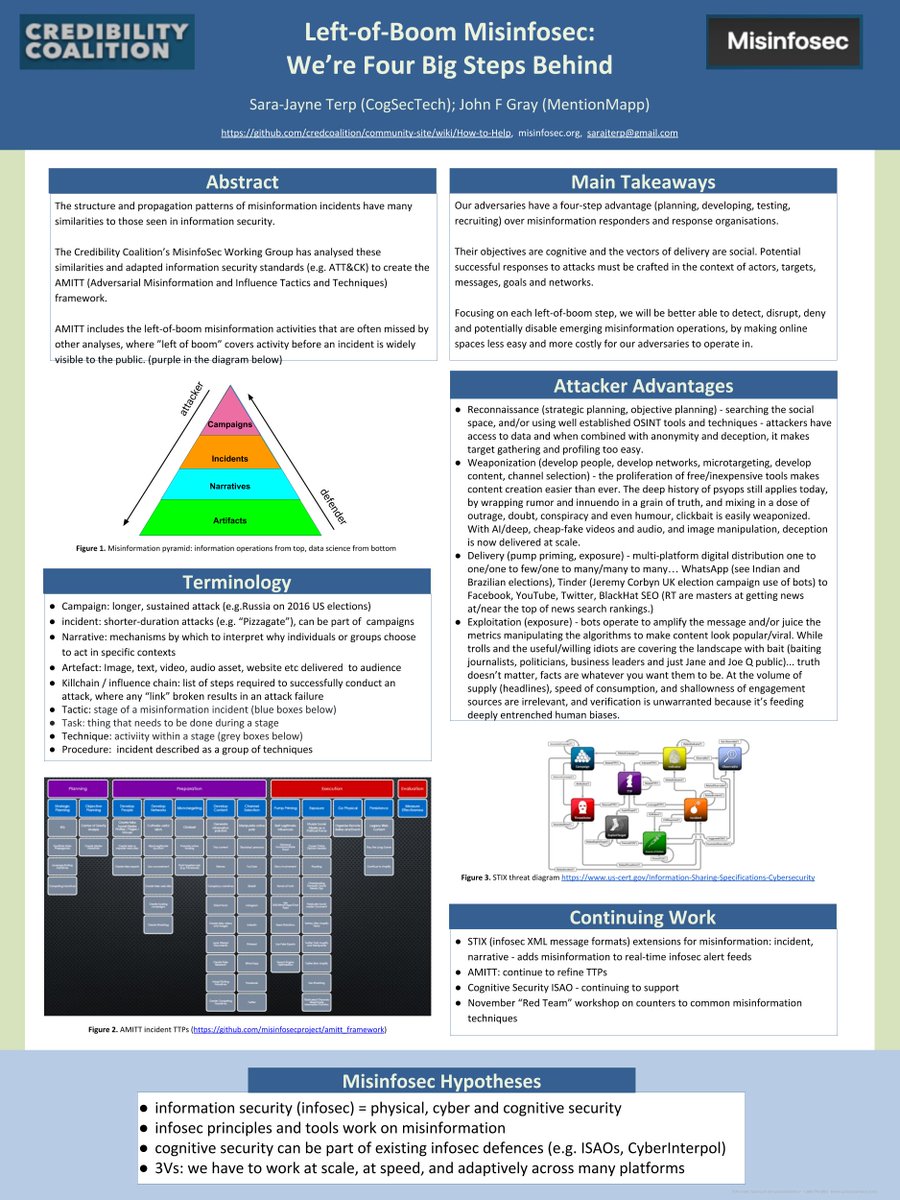
Misinfosec hypotheses: infosec = physical, cyber + cognitive security; infosec principles & tools work on misinformation; cognitive security can be part of existing infosec defences (ISAOs, CyberInterpol);
3Vs: has to work at scale, at speed, and adaptively across many platforms
3Vs: has to work at scale, at speed, and adaptively across many platforms
The structure and propagation patterns of misinformation incidents have many similarities to those seen in information security. @credcoalition MisinfoSec Working Group analysed these similarities and adapted information security standards (e.g. ATT&CK) to create AMITT framework
We open-sourced the AMITT misinfosec framework. You can find it, and the white papers we wrote on its creation, at github.com - we'll keep putting new work there too
Terminology.
* Campaign: longer, sustained attack (eg 2016 US elections)
* incident: shorter-duration attacks (eg Pizzagate), can be part of campaigns
* Narrative: mechanism to interpret why individuals/ groups choose to act in specific context
* Artifact: Image, text, site etc
* Campaign: longer, sustained attack (eg 2016 US elections)
* incident: shorter-duration attacks (eg Pizzagate), can be part of campaigns
* Narrative: mechanism to interpret why individuals/ groups choose to act in specific context
* Artifact: Image, text, site etc
Terminology: TTPs
* Tactic: stage of a misinformation incident (blue boxes)
* (Task: thing that needs to be done during a stage)
* Technique: activity within a stage (grey boxes)
* Procedure: incident described as a group of techniques
We can disrupt any of these
* Tactic: stage of a misinformation incident (blue boxes)
* (Task: thing that needs to be done during a stage)
* Technique: activity within a stage (grey boxes)
* Procedure: incident described as a group of techniques
We can disrupt any of these
@grayspective's notes: Attackers have advantages across the 4 big steps before misinformation is visible to the public (these are the 4 left-of-boom steps in the Cyber Killchain), which is when most analysis and defence starts
The point of building tools like AMITT is being able to talk about techniques, artefacts, counters etc across the *whole* disinformation production cycle, not just after the 'boom'. It also lets us add disinformation to existing infosec alert feeds and coordinate response
Main takeaways from @grayspective. Thank you for coming to our online poster!
Loading suggestions...