Yes, an old #Sigma rule that detect Office programs spawning processes in user folders would have detected #APT28's recent campaign agains Kazakhstan
Tweet by @MeltX0R
Dropper in Sandbox
app.any.run
Rule
github.com
Tweet by @MeltX0R
Dropper in Sandbox
app.any.run
Rule
github.com
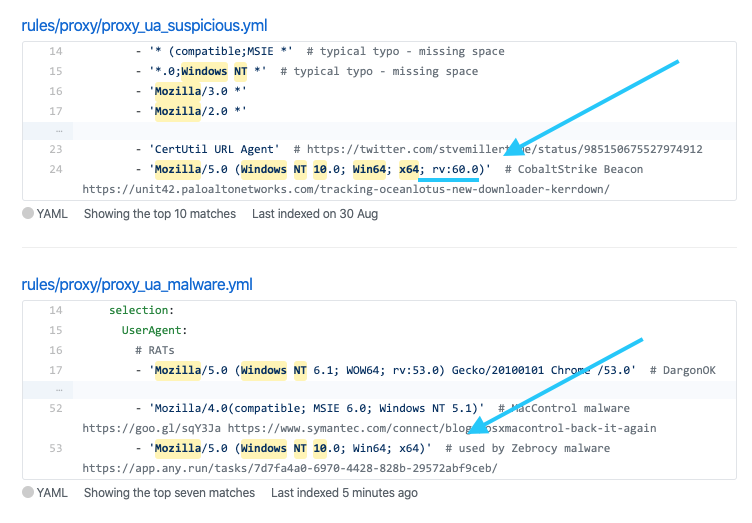
@MeltX0R Also check that User-Agent without 'AppleWebKit ..' used by the malware.
Netscape Navigator 5 (or alike) on Windows 10 shouldn't be that common.
Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Netscape Navigator 5 (or alike) on Windows 10 shouldn't be that common.
Mozilla/5.0 (Windows NT 10.0; Win64; x64)
Loading suggestions...