There has never been a better time than right now to get involved with Azure security research.
Not convinced yet? Let's compare where we are with Azure versus where we are with on-prem AD: 🧵
Not convinced yet? Let's compare where we are with Azure versus where we are with on-prem AD: 🧵
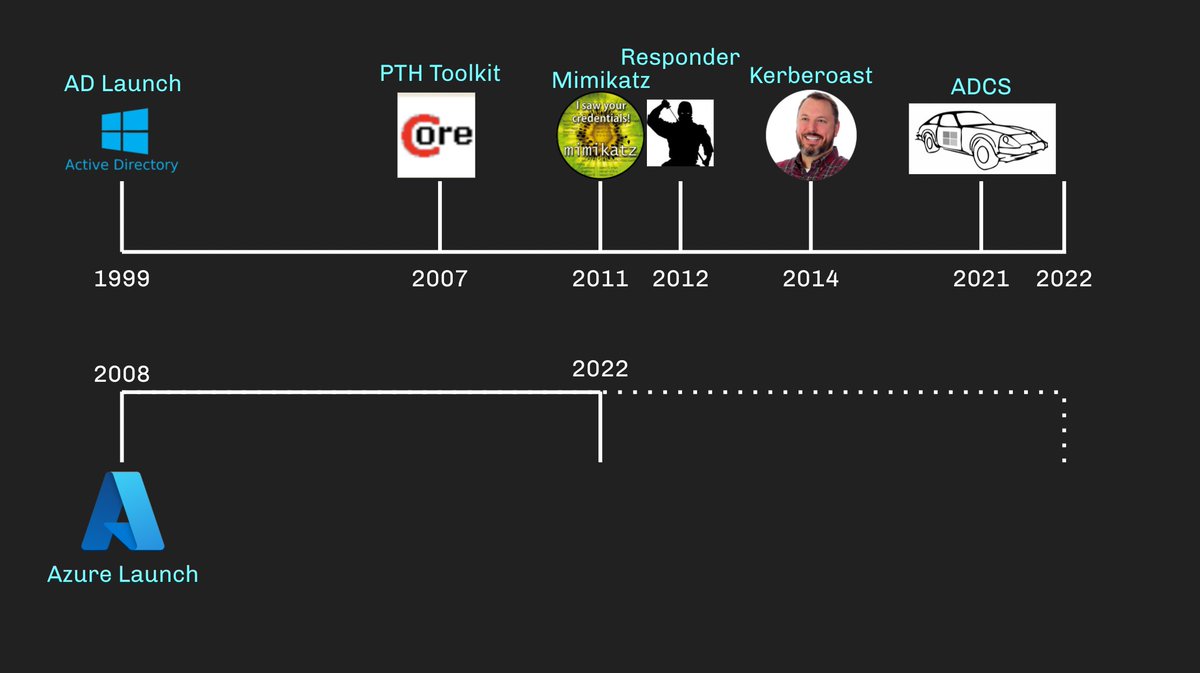
We actually had pass-the-hash before AD came out, but it wasn't really made practical until @hernano released the PTH Toolkit in 2007, nearly 8 years after AD's release:
2011 gave us Mimikatz by Benjamin Delpy (@gentilkiwi), 2012 gave us Responder by Laurent Gaffié (@PythonResponder). Two tools that are still used every day by every pentest shop a full decade after they came out:
What do these tools and techniques all have in common?
✅ - They all came out several years after AD's initial release
✅ - They have all stood the test of time and are all still used on a daily basis
✅ - NONE of them are "exploits" - they are abuses and abuse tooling
✅ - They all came out several years after AD's initial release
✅ - They have all stood the test of time and are all still used on a daily basis
✅ - NONE of them are "exploits" - they are abuses and abuse tooling
In 2018, a full ten years after Azure's initial release, Karl Fosaaen (@kfosaaen) gave us Microburst:
There are OCEANS of attack research opportunity in Azure. We are not even CLOSE to done. Who knows what the next 10 years might bring?
This isn't a controversial opinion - quite the opposite, as the results of this poll show:
Ok. So you want to get involved. What do you do?
First, read this blog post by @JohnLaTwC: @johnlatwc/defenders-mindset-319854d10aaa" target="_blank" rel="noopener" onclick="event.stopPropagation()">medium.com
John's post, for me, argues very effectively for the value attack research provides for defense:
First, read this blog post by @JohnLaTwC: @johnlatwc/defenders-mindset-319854d10aaa" target="_blank" rel="noopener" onclick="event.stopPropagation()">medium.com
John's post, for me, argues very effectively for the value attack research provides for defense:
Second, catch up by reading everything written by these people:
@kfosaaen, @asegunlolu, @inversecos, @_dirkjan, @olafhartong, @DrAzureAD, @joslieben, @DebugPrivilege, @mariussmellum, @PyroTek3, @Haus3c
@kfosaaen, @asegunlolu, @inversecos, @_dirkjan, @olafhartong, @DrAzureAD, @joslieben, @DebugPrivilege, @mariussmellum, @PyroTek3, @Haus3c
Third, consider watching my talk at @1ns0mn1h4ck next month, where I will try to give you my best walk-through of my own abuse research methodology that you can use and improve: insomnihack.ch
Loading suggestions...