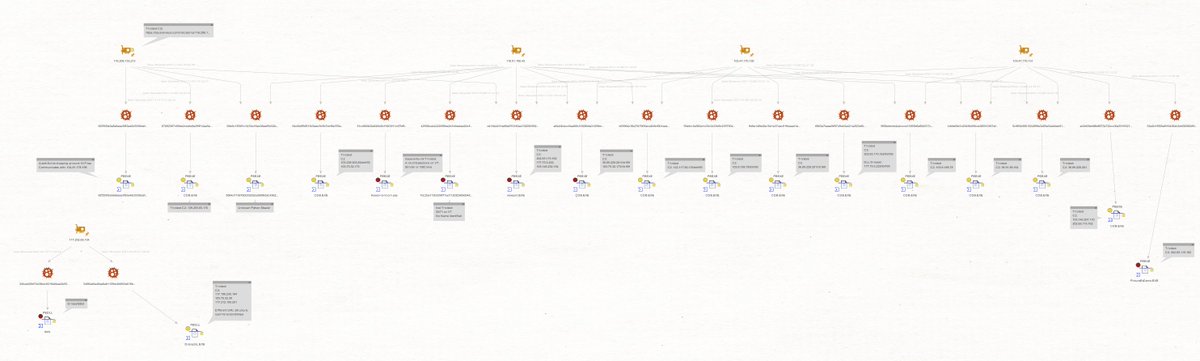
The #ContiLeaks contained some messages consisting of IP:Username:pass combinations for #Conti infrastructure.
This allows us to connect certain #Trickbot activcity with the #Conti group:
1/x
This allows us to connect certain #Trickbot activcity with the #Conti group:
1/x
The IP's in the image are the following:
117.252.69[.]134
117.252.68[.]15
116.206.153[.]212
103.78.13[.]150
103.47.170[.]131
103.47.170[.]130
118.91.190[.]42
117.197.41[.]36
117.222.63[.]77
117.252.69[.]210
2/x
117.252.69[.]134
117.252.68[.]15
116.206.153[.]212
103.78.13[.]150
103.47.170[.]131
103.47.170[.]130
118.91.190[.]42
117.197.41[.]36
117.222.63[.]77
117.252.69[.]210
2/x
Using @MaltegoHQ together with OTX/Alienvault and
@virustotal integration, we are able to connect several of these IP's to #Trickbot activity:
3/x
@virustotal integration, we are able to connect several of these IP's to #Trickbot activity:
3/x
Would love to know if these have any relation to #Conti.
Maybe someone with better RE Skills can have a look ?
@malwrhunterteam @herrcore @aaqeel87 @TheDFIRReport @VK_Intel @executemalware
Maybe someone with better RE Skills can have a look ?
@malwrhunterteam @herrcore @aaqeel87 @TheDFIRReport @VK_Intel @executemalware
Loading suggestions...