Social Engineering is basically manipulating people that easily give confidential information. This comes in online interactions.
Its much more easier to trick a person at a platform where instinct aren't heightened. Criminals use this to access all types of info and set attacks
Its much more easier to trick a person at a platform where instinct aren't heightened. Criminals use this to access all types of info and set attacks
Most Social Engineering attacks actually happen with daily interaction between a hacker and a victim. It's never just forceful. It's built up over time and engagement.
Hackers give you relatable and reliable sources of content before the actual attack begins.
Hackers give you relatable and reliable sources of content before the actual attack begins.
There 5 types of Social Engineering Methods/Techniques that are used.
1.) Baiting - using false info/way to peak at your interest. This may look authentic but it's usually is covered in malware virus.
Competition on your favourite app, weekend getaways, Ads and whatsapp links
1.) Baiting - using false info/way to peak at your interest. This may look authentic but it's usually is covered in malware virus.
Competition on your favourite app, weekend getaways, Ads and whatsapp links
2.) Phishing - this carried out through email and texting campaigns. This carry a sense of urgency in them. Like notifying you of bank breach, taxes but the latest one is on insurance and claims. They'll notify you of a violation and causes a immediate reaction from you.
3. Spear Phishing - This more direct and intended at high networth individuals. This one can be directed at CEO and Executive but also social media influencers. This takes much more detail. Eg: Naak Musiq Twitter acc hack.
They could lure them through, close friends/work related
They could lure them through, close friends/work related
4.) PRETEXTING 🚩🚩🚩🚩
This is when hacker takes your information through a sequence of creative lies.
The scam starts off by the perpetrator pretending to need sensitive information from a victim so as to perform a critical task.
They first start off by establishing trust
This is when hacker takes your information through a sequence of creative lies.
The scam starts off by the perpetrator pretending to need sensitive information from a victim so as to perform a critical task.
They first start off by establishing trust
The classic case is impersonating bank and tax workers they ask personal questions that need you to divulge personal information.
Eg: ABSA had a data breach. How many who are ABSA clients gave away info without verifying. Even with cellphones. Call centres(R99 debit scandal)
Eg: ABSA had a data breach. How many who are ABSA clients gave away info without verifying. Even with cellphones. Call centres(R99 debit scandal)
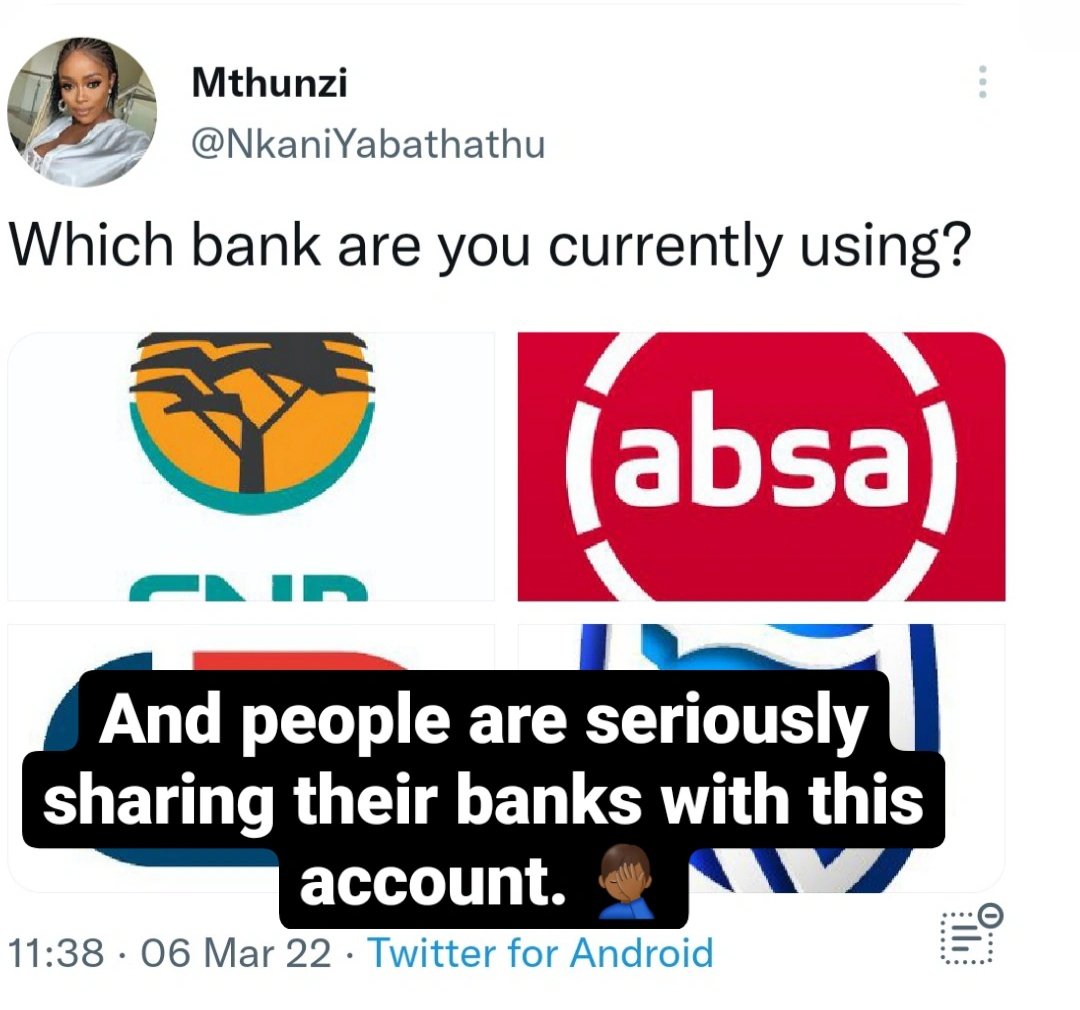
Pretexting can be applied through social media content on a daily.
That account that seems harmless because its all about retweets and likes. They only ask your age, your favourite bank and name? That's a Pretexting, they've created a scenario that compels you to answer
That account that seems harmless because its all about retweets and likes. They only ask your age, your favourite bank and name? That's a Pretexting, they've created a scenario that compels you to answer
5.) Tailgating and Piggybacking.
This is more a physical attack to a cyber crime. Gain unauthorized access . Simply put, it's how people steal your cellphones /devices at Mall of Africa. From retail shops, outside clubs or even bridging details of a flight and making them yours
This is more a physical attack to a cyber crime. Gain unauthorized access . Simply put, it's how people steal your cellphones /devices at Mall of Africa. From retail shops, outside clubs or even bridging details of a flight and making them yours
These are the 5 most common social engineering methods. There are alot but I took ones most common through social media and ones have been occurring alot. I simplified the meanings.
Please be vigilant. Cyber crimes are real and South Africa/Africa is experiencing alot of it.
Please be vigilant. Cyber crimes are real and South Africa/Africa is experiencing alot of it.
@iamandiva your aunts stokvel.
They are targeting funds. The stokvel group will be hit with a few of these. Most likely whatsapp links
They are targeting funds. The stokvel group will be hit with a few of these. Most likely whatsapp links
Loading suggestions...