Another "crypto hack made simple" thread for ya. @BeanstalkFarms, a DeFi protocol, was just exploited for about $75m worth of Ether (~25k ETH). Here's how the heist went down.
Here's the transaction on Etherscan if you want to follow along with this thread: etherscan.io
Before I get started, you should know that at the core of this hack was something known as a "flash loan". It's an interesting mechanism unique to crypto that can be used to carry out exploits like this.
Quick note: this is my first time investigating a flash loan attack. There might be a few inaccuracies here, but I've done my best to make this as accessible as possible. I hope this is insightful and shines some light on how these sort of flash loan attacks work. ❤️
A flash loan is when someone takes out a loan on a blockchain and repays that loan within the same transaction. It's a no-risk loan for the lender because if the loan doesn't get paid back then the transaction is invalid and won't be included in the blockchain in the first place.
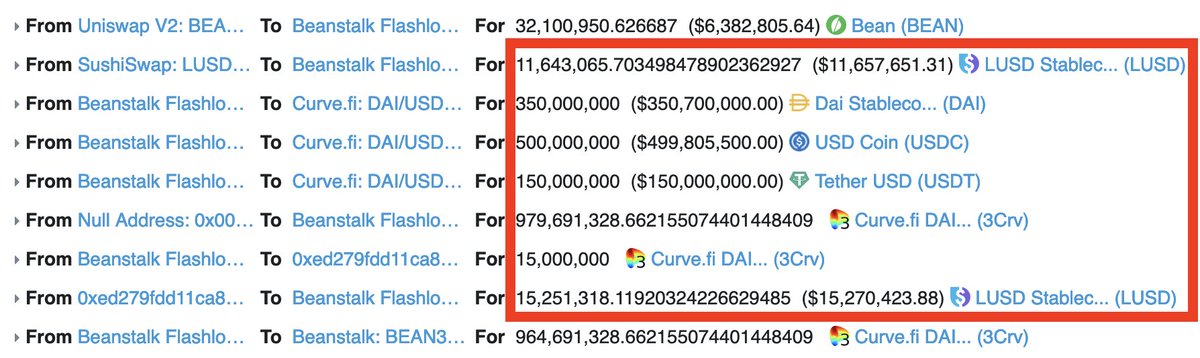
After buying all those $BEAN tokens, the attacker started making a $BEAN stew. It minted some $3Crv tokens by depositing the $DAI, $USDC, and $USDT into @CurveFinance. It also bought about $25m worth of the $LUSD stablecoin along the way.
Next the attacker deposited the $3Crv tokens into another contract in order to generate *another* token called BEAN3CRV-f.
This was followed by a deposit of the 32m $BEAN tokens and the 25m $LUSD into yet *another* contract to generate a different token called BEAN3LUSD-f (and yes, this is as batshit crazy as it sounds).
Alright, you're probably getting confused now, so let's reorganize. At this point, our attacker only really has two token stacks left: BEAN3CRV-f and BEAN3LUSD-f. Why does the attacker want these obscure tokens? Because they're the key to controlling $BEAN itself.
It turns out that $BEAN is designed to have a governing system on Ethereum. Users can get access to a special type of asset called "Seeds" which acts like voting power in the system. The more Seeds you have, the more voting power you have.
Users with Seeds can vote on proposals that do pretty much anything. This is intended to give the system a way to evolve. Users with the most invested in the system are supposed to get control over the way that the system can change.
Of course, someone malicious could use this to do very bad things. And that's exactly what we're seeing here.
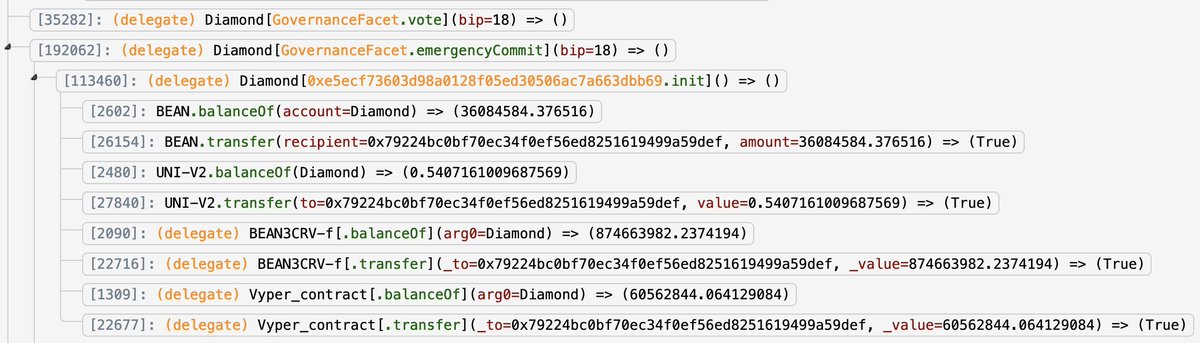
BEAN3CRV-f and BEAN3LUSD-f can be converted directly into Seeds, giving the attacker a *huge* amount of voting power. In fact, the flash loan and $BEAN stew allowed the attacker to control more than 70% of the total number of Seeds.
This 70% number is important because it's higher than the 66% threshold required to execute an "emergency" governance action. With more than 2/3rds of the voting power, the attacker was able to siphon absolutely everything from the $BEAN contract, about $180m worth of assets.
Everything after this point was just cleanup. The attacker then unraveled all of its positions and used the proceeds of the attack to pay back the flash loan. At the end of the day, the attacker left with almost 25k ETH at a value of close to $75m.
As an interesting side-note, there's a ~1 day delay for *all* governance actions in the $BEAN contract. The attacker actually set this whole thing up yesterday when it made two governance proposals.
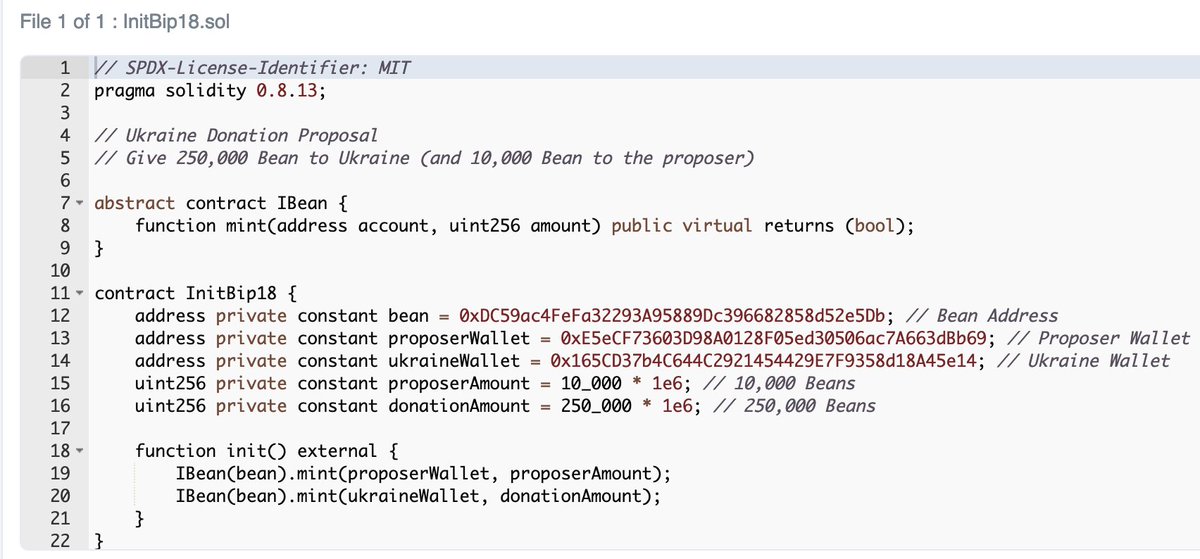
The first proposal (proposal #18) steals all the money in the contract. The next proposal (proposal #19) sends $250k worth of $BEAN to the Ukraine donation address. This Ukraine proposal is *named* Bip18 (instead of Bip19) and may have been used to avoid suspicion.
Still, the attacker executed both of these proposals. So the Ukraine is now sitting on $250k worth of stolen funds. Will be interesting to see what they do with it.
Anyway, that's the full thread. As I wrote before, this is my first time investigating a flash loan attack. There might be some inaccuracies here but I did my best. I hope you learned something new about how these attacks work.
I used the following tools for this analysis:
etherscan.io
tenderly.co
ethtx.info
These are usually my go-to tools, I highly recommend them to anyone looking to analyze hacks like this.
etherscan.io
tenderly.co
ethtx.info
These are usually my go-to tools, I highly recommend them to anyone looking to analyze hacks like this.
Images didn't upload properly (ugh Twitter y u do this 2 me). Will add images as replies to each of the tweets they were supposed to be attached to.
Loading suggestions...