What happens when you combine hackers and phones?
Phreaking?
Social Engineering?
Sure! Valid answers.
What you didn't think of is web vulnerabilities.
XXE.
I found an XXE by phone call in a bug bounty program.
Here's the story:
Phreaking?
Social Engineering?
Sure! Valid answers.
What you didn't think of is web vulnerabilities.
XXE.
I found an XXE by phone call in a bug bounty program.
Here's the story:
1/ This company provided phone services.
Specifically for Interactive Voice Response (IVR) systems.
Corben. What the heck is IVR?
Have you ever called customer support and got a pre-recorded message prompting you to do something?
That's IVR.
Automated phone systems.
So,
Specifically for Interactive Voice Response (IVR) systems.
Corben. What the heck is IVR?
Have you ever called customer support and got a pre-recorded message prompting you to do something?
That's IVR.
Automated phone systems.
So,
2/ In this application, you could:
- Buy a phone number
- Forward incoming calls to an IVR (powered by VoiceXML)
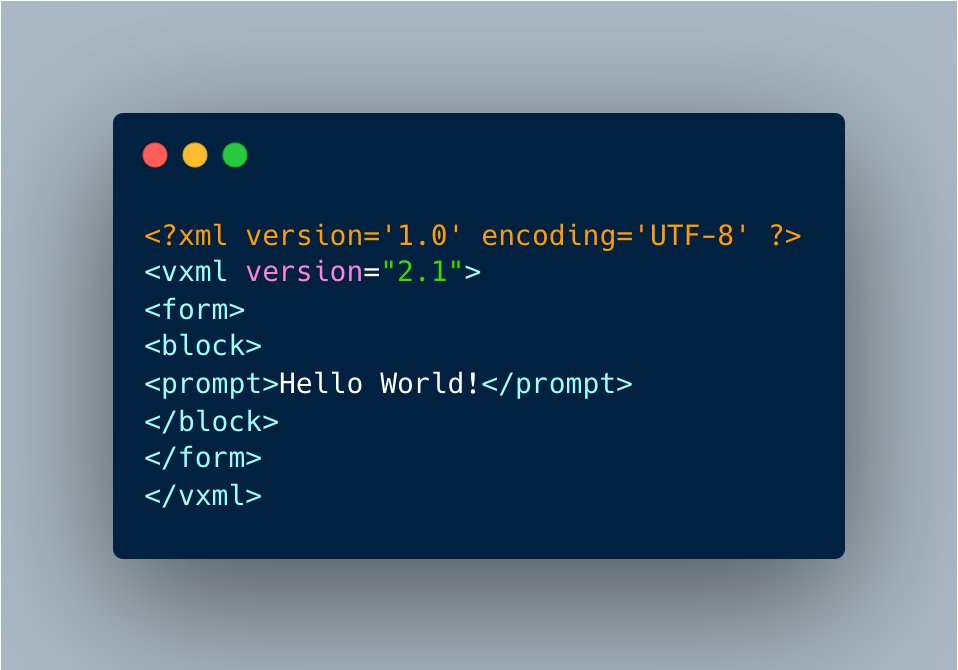
What's VoiceXML?
VoiceXML is a (XML-based) markup language.
Developers use VoiceXML to build IVR systems (again, which automate interactions over the phone).
So,
- Buy a phone number
- Forward incoming calls to an IVR (powered by VoiceXML)
What's VoiceXML?
VoiceXML is a (XML-based) markup language.
Developers use VoiceXML to build IVR systems (again, which automate interactions over the phone).
So,
4/ How do you attack XML processors?
XML External Entities (XXE)!
If you don't know what it is, Google it :)
Basically, XXE let you read local files, perform SSRF attacks, DoS, and occasionally execute code.
Anyways,
XML External Entities (XXE)!
If you don't know what it is, Google it :)
Basically, XXE let you read local files, perform SSRF attacks, DoS, and occasionally execute code.
Anyways,
6/
1. I visited the site: https://dashboard.█████\.com/
2. I bought a phone number
3. Setup the number to forward inbound calls to the VoiceXML script.
4. Set the script to the VoiceXML file containing the XXE payload.
So I called the number.
Ringing.
Ringing...
And
1. I visited the site: https://dashboard.█████\.com/
2. I bought a phone number
3. Setup the number to forward inbound calls to the VoiceXML script.
4. Set the script to the VoiceXML file containing the XXE payload.
So I called the number.
Ringing.
Ringing...
And
7/ The system answered.
A voice said "hacked".
Then it hung up...
I checked the logs to my server..
It worked!
I had the contents of /etc/passwd!
Eventually,
A voice said "hacked".
Then it hung up...
I checked the logs to my server..
It worked!
I had the contents of /etc/passwd!
Eventually,
8/ The company fixed the vulnerability by moving from VoiceXML to JSON Text-To-Speech.
Here's a proof-of-concept if you want to see it in action:
youtu.be
Here's a proof-of-concept if you want to see it in action:
youtu.be
9/ TLDR:
- Company offered Interactive Voice Response systems
- IVR systems were customizable with VoiceXML.
- Bought a phone number
- Configured the IVR system to use VoiceXML that contained an XXE payload.
- Called the phone number.
- XXE worked :)
- Company offered Interactive Voice Response systems
- IVR systems were customizable with VoiceXML.
- Bought a phone number
- Configured the IVR system to use VoiceXML that contained an XXE payload.
- Called the phone number.
- XXE worked :)
If you want more hacker stories, make sure to:
• sign up for my newsletter: newsletter.threat.dev
• follow: @hacker_
• sign up for my newsletter: newsletter.threat.dev
• follow: @hacker_
Loading suggestions...