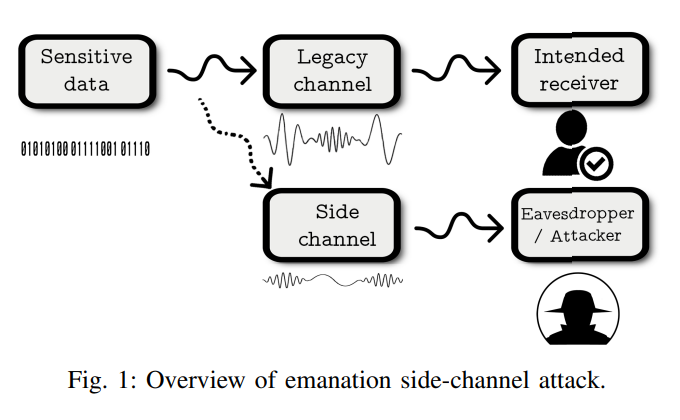
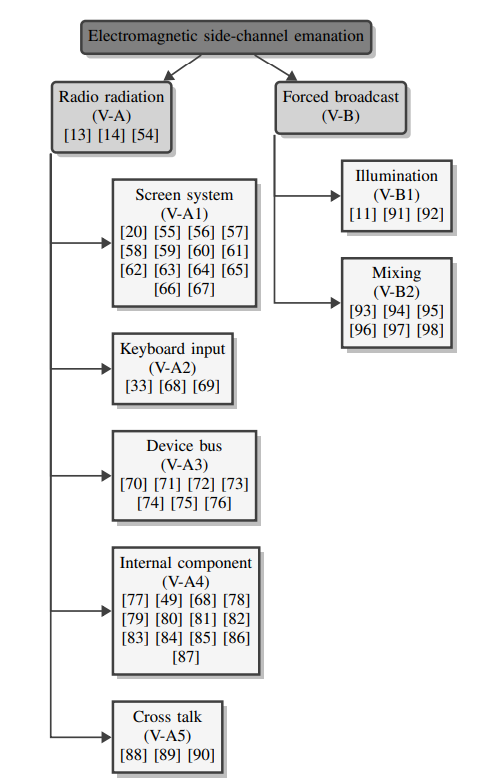
2. Video Tutorial 1
youtube.com
youtube.com
3. Video Tutorial 2
How to Spy on Computer Monitors | TempestSDR Tutorial (with an Airspy)
youtube.com
How to Spy on Computer Monitors | TempestSDR Tutorial (with an Airspy)
youtube.com
4. Paper 1
Analysing Security-related Signals Using Software defined Radio by Thomas Rudolph
informatik.rub.de
Analysing Security-related Signals Using Software defined Radio by Thomas Rudolph
informatik.rub.de
7. Demo Video
securityonline.info
securityonline.info
8. Applications - Mobile Devices
Screen Gleaning: A Screen Reading TEMPEST Attack on Mobile Devices Exploiting an Electromagnetic Side Channel
ndss-symposium.org
Screen Gleaning: A Screen Reading TEMPEST Attack on Mobile Devices Exploiting an Electromagnetic Side Channel
ndss-symposium.org
9. Applications - Computer Monitors
Accuracy Enhancement of Electromagnetic
Side-Channel Attacks on Computer Monitors
forensicsandsecurity.com
Accuracy Enhancement of Electromagnetic
Side-Channel Attacks on Computer Monitors
forensicsandsecurity.com
10. Side Channels (Useful Appendix of Papers)
Whispering devices: A survey on how side-channels lead to compromised information
hal.archives-ouvertes.fr
Whispering devices: A survey on how side-channels lead to compromised information
hal.archives-ouvertes.fr
11. HDMI Cables
You can recover "noisy" information from radiated emissions of an HDMI cable
hardwear.io
VGA or HDMI cables produce unintended emanations which can be received & processed to reconstruct the external monitor video frames
researchgate.net
You can recover "noisy" information from radiated emissions of an HDMI cable
hardwear.io
VGA or HDMI cables produce unintended emanations which can be received & processed to reconstruct the external monitor video frames
researchgate.net
16. Last but not Least - Countermeasures
Likely Non-state Actor Countermeasures to SIGINT Monitoring Efforts on and off the Battlefield
1. Bury fiber optic cables from safehouse to safehouse to create a clandestine communications system
researchgate.net
Likely Non-state Actor Countermeasures to SIGINT Monitoring Efforts on and off the Battlefield
1. Bury fiber optic cables from safehouse to safehouse to create a clandestine communications system
researchgate.net
17. Countermeasures (continued)
2. communications room inside a safehouse
3. RF absorbing paints, fabrics & commercially available faraday tents can prevent TEMPEST attacks
2. communications room inside a safehouse
3. RF absorbing paints, fabrics & commercially available faraday tents can prevent TEMPEST attacks
18. Other Countermeasures
4. Tor and VPN hardware routers & laptops without hard disks to boot the TAILS OS via DVD
5. Thermite-based automated destruction systems
6. Magnetrons to create self-destructing computer systems (destroying RAM modules)
researchgate.net
4. Tor and VPN hardware routers & laptops without hard disks to boot the TAILS OS via DVD
5. Thermite-based automated destruction systems
6. Magnetrons to create self-destructing computer systems (destroying RAM modules)
researchgate.net
19. Drone Issues
Strategies to Harden & Neutralize UAVs using RF DEW
@LOPESSECURITY-at-hardwear.io-2018.pdf" target="_blank" rel="noopener" onclick="event.stopPropagation()">media.hardwear.io
Strategies to Harden & Neutralize UAVs using RF DEW
@LOPESSECURITY-at-hardwear.io-2018.pdf" target="_blank" rel="noopener" onclick="event.stopPropagation()">media.hardwear.io
20. Unroll Tempest - Citizen Spy @threadreaderapp
TEMPEST shows that, even if an organization’s systems don’t leave apparently secure physical spaces, or aren’t even connected, they are not necessarily totally safe.
Tickets to Wuhan?
TEMPEST shows that, even if an organization’s systems don’t leave apparently secure physical spaces, or aren’t even connected, they are not necessarily totally safe.
Tickets to Wuhan?
21. More Tempest Resources (1)
1. László Miklós Bíró - Tempest, the hidden source of data leakage
youtube.com
2. Electromagnetic Eavesdropping Risks of
Flat-Panel Displays
cl.cam.ac.uk
cl.cam.ac.uk
1. László Miklós Bíró - Tempest, the hidden source of data leakage
youtube.com
2. Electromagnetic Eavesdropping Risks of
Flat-Panel Displays
cl.cam.ac.uk
cl.cam.ac.uk
22. More Resources (2)
3. Stealing Keys from PCs using a Radio:
Cheap Electromagnetic Attacks
tau.ac.il
4. Soft Tempest: Hidden Data Transmission Using Electromagnetic Emanations,
cl.cam.ac.uk
5. Early NSA on Tempest
web.archive.org
3. Stealing Keys from PCs using a Radio:
Cheap Electromagnetic Attacks
tau.ac.il
4. Soft Tempest: Hidden Data Transmission Using Electromagnetic Emanations,
cl.cam.ac.uk
5. Early NSA on Tempest
web.archive.org
23. Yet More Resources
6. Complete, Unofficial TEMPEST Information Page
web.archive.org
7. Tempest: A tin foil hat for your electronics and their secrets
hackaday.com
6. Complete, Unofficial TEMPEST Information Page
web.archive.org
7. Tempest: A tin foil hat for your electronics and their secrets
hackaday.com
24. Marcus Kuhn's Dissertation
@rossjanderson @mgk25
cl.cam.ac.uk
(a detailed compendium on electromagnetic eavesdropping techniques for video displays)
Compromising emanations: eavesdropping risks of computer displays
cl.cam.ac.uk
@rossjanderson @mgk25
cl.cam.ac.uk
(a detailed compendium on electromagnetic eavesdropping techniques for video displays)
Compromising emanations: eavesdropping risks of computer displays
cl.cam.ac.uk
unroll TEMPEST again @threadreaderapp
Loading suggestions...