Crypto folks are targetted more and more by spear phishing campaings.
Some of them are clever, some of them are just working on human greed.
Here is the list of all phishing attempts that I saw, read or witnessed myself 🧵👇
Some of them are clever, some of them are just working on human greed.
Here is the list of all phishing attempts that I saw, read or witnessed myself 🧵👇
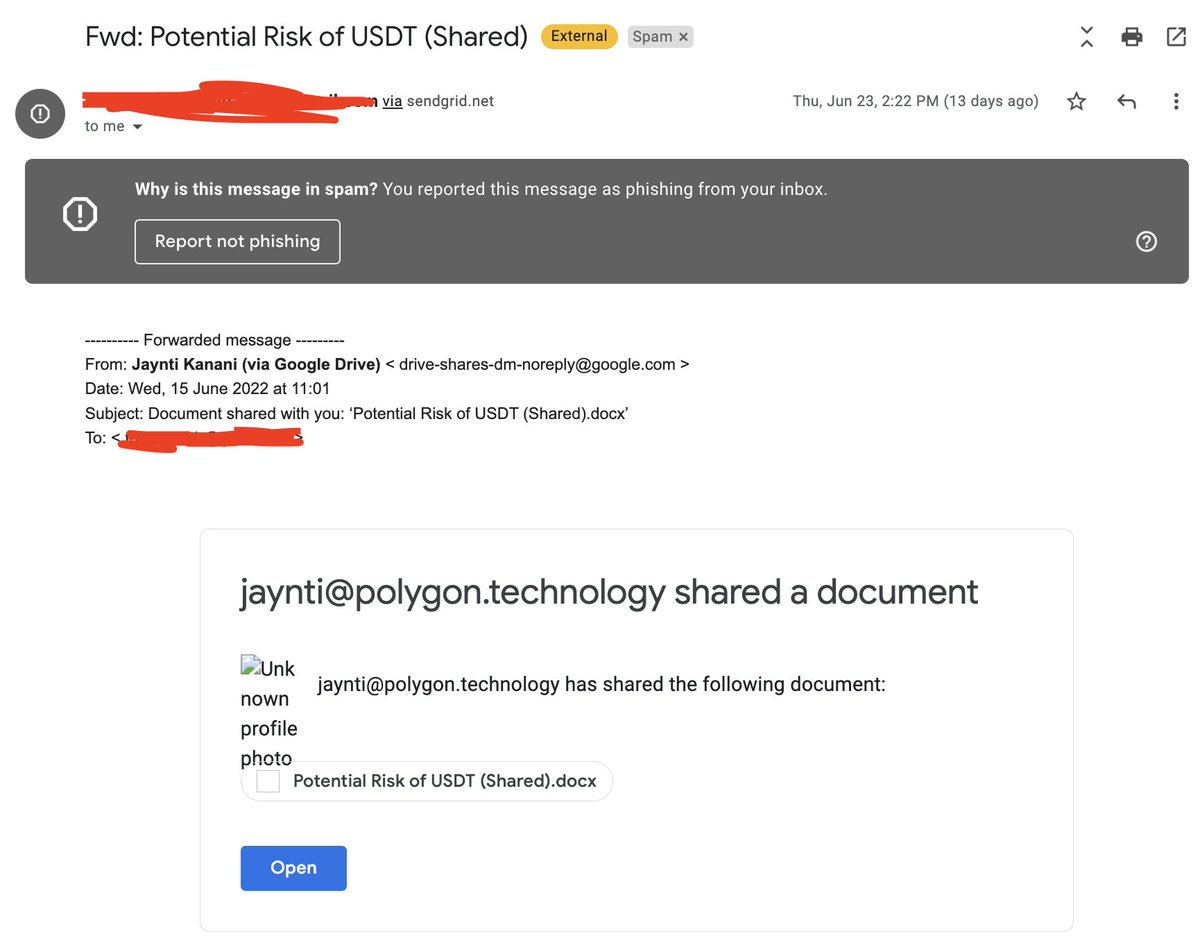
The most famous phishing campaign happen to Ronin Network thanks to a targeted job offer to one of the Axie developers.
The job offered a quite generous compensation package. To learn more the offer and the company, the employee was deceived into downloading and opening a PDF
The job offered a quite generous compensation package. To learn more the offer and the company, the employee was deceived into downloading and opening a PDF
PDF document, which the engineer downloaded -- allowed spyware to infiltrate Ronin’s systems.
You can learn more about this case here: theblock.co
You can learn more about this case here: theblock.co
The attack was also performed on me but due to my paranoid nature, I didn't open the PDF and deleted convo
The situation was similar, I was asked to join the board of X company as an advisor and I was offered quite generous pay for that. To learn more, I was sent a PDF document.
The situation was similar, I was asked to join the board of X company as an advisor and I was offered quite generous pay for that. To learn more, I was sent a PDF document.
This was done not on LinkedIn, but on Telegram, as LinkedIn does run some basic malware analysis on the shared documents in the chat.
Lesson: Don't download and open any file sent to you by unknown person. If you need to open them, use this tool
Lesson: Don't download and open any file sent to you by unknown person. If you need to open them, use this tool
Don't trust anyone who wants to talk about a job outside of LinkedIn and is asking you to join an XYZ chat.
You can be sure they try to scam you and hack you.
Another type of an attack relies on human greed.
You can be sure they try to scam you and hack you.
Another type of an attack relies on human greed.
Here is another type of an attack that targets security professionals.
In this case, nobody was hacked but the attack vector is interesting. Attackers play on your emotions and trying to guilt you or scare you into opening a malicious link/PDF.
In this case, nobody was hacked but the attack vector is interesting. Attackers play on your emotions and trying to guilt you or scare you into opening a malicious link/PDF.
If you work in recruiting at Web3 company, you also need to watch out for North Korean hackers trying to get to the company through hiring process.
There is a wonderful and frighting story about one of such cases. Please read it.
There is a wonderful and frighting story about one of such cases. Please read it.
On the same subject, you should also be extra careful when on a call with anybody you not know as they may be using DeepFake technology to fool you.
Recent PSA from FBI details how that can look like: ic3.gov
Recent PSA from FBI details how that can look like: ic3.gov
If you think that MFA(2FA) can protect you, there is another type of an attack that can hack you even if you use MultiFactor Authenticator 👇
arstechnica.com
arstechnica.com
What can you do to protect yourself?
Here is awesome guide from @officer_cia that dives deep into this subject and lays down various steps and techniques how you can stay secure
github.com
Here is awesome guide from @officer_cia that dives deep into this subject and lays down various steps and techniques how you can stay secure
github.com
If you have a story or a link to a story of a crypto phishing campaign that targets specifically crypto/web3 folks, let me know in the comment below.
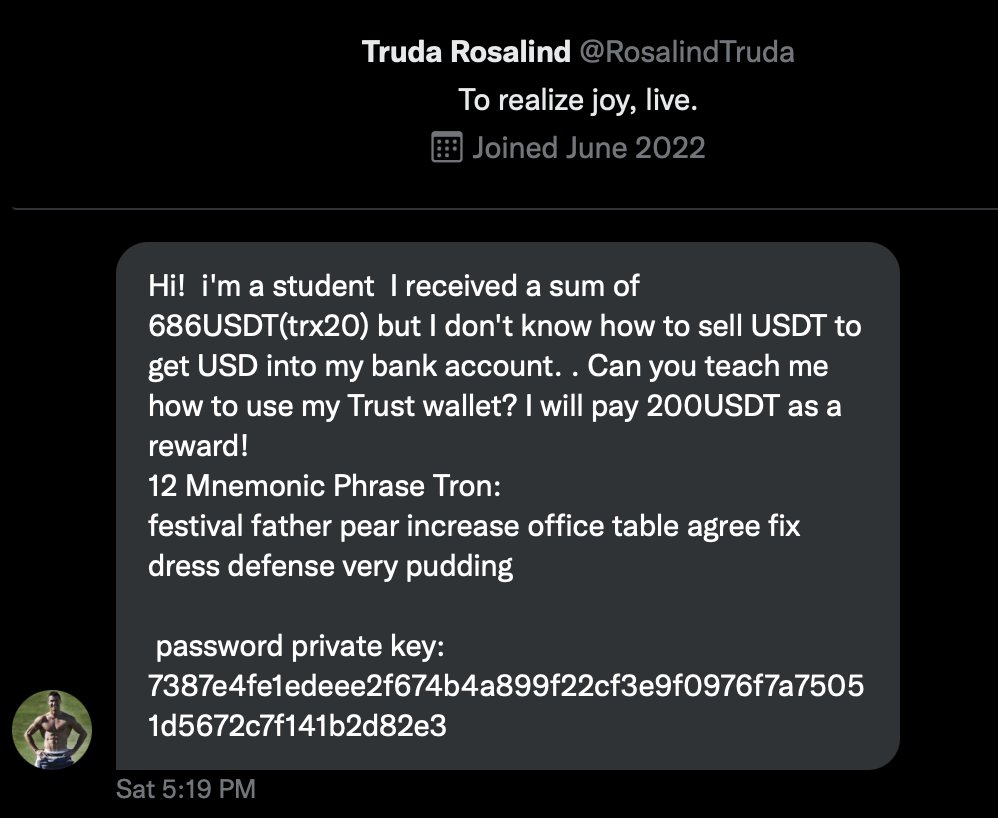
⚠️Update regarding the 12 mnemonic phrase / private key phishing DMs:
There is a reason they use BSC or Tron. Flashbots won't work on these network, neither private mempools like Taichi.
Only way to have an MEV is by higher pricing of Gas ⛽️
There is a reason they use BSC or Tron. Flashbots won't work on these network, neither private mempools like Taichi.
Only way to have an MEV is by higher pricing of Gas ⛽️
Many of these tokens "stuck" in the phishing accounts are either honeypot tokens or blacklisted USDT.
Scammers have access to the accounts with blacklisted USDT. They're using such accounts into tricking people of actually sending BNB/TRN to retrieve such tokens.
Scammers have access to the accounts with blacklisted USDT. They're using such accounts into tricking people of actually sending BNB/TRN to retrieve such tokens.
H/T to @officer_cia 🙏 for the discussion over the DMs and pointing out USDT tokens are actually blacklisted.
I wasn't aware of that and it makes this scam even more elaborate than I thought of it.
I wasn't aware of that and it makes this scam even more elaborate than I thought of it.
Another interesting variation of already discussed attack, but now with much more details.
Loading suggestions...