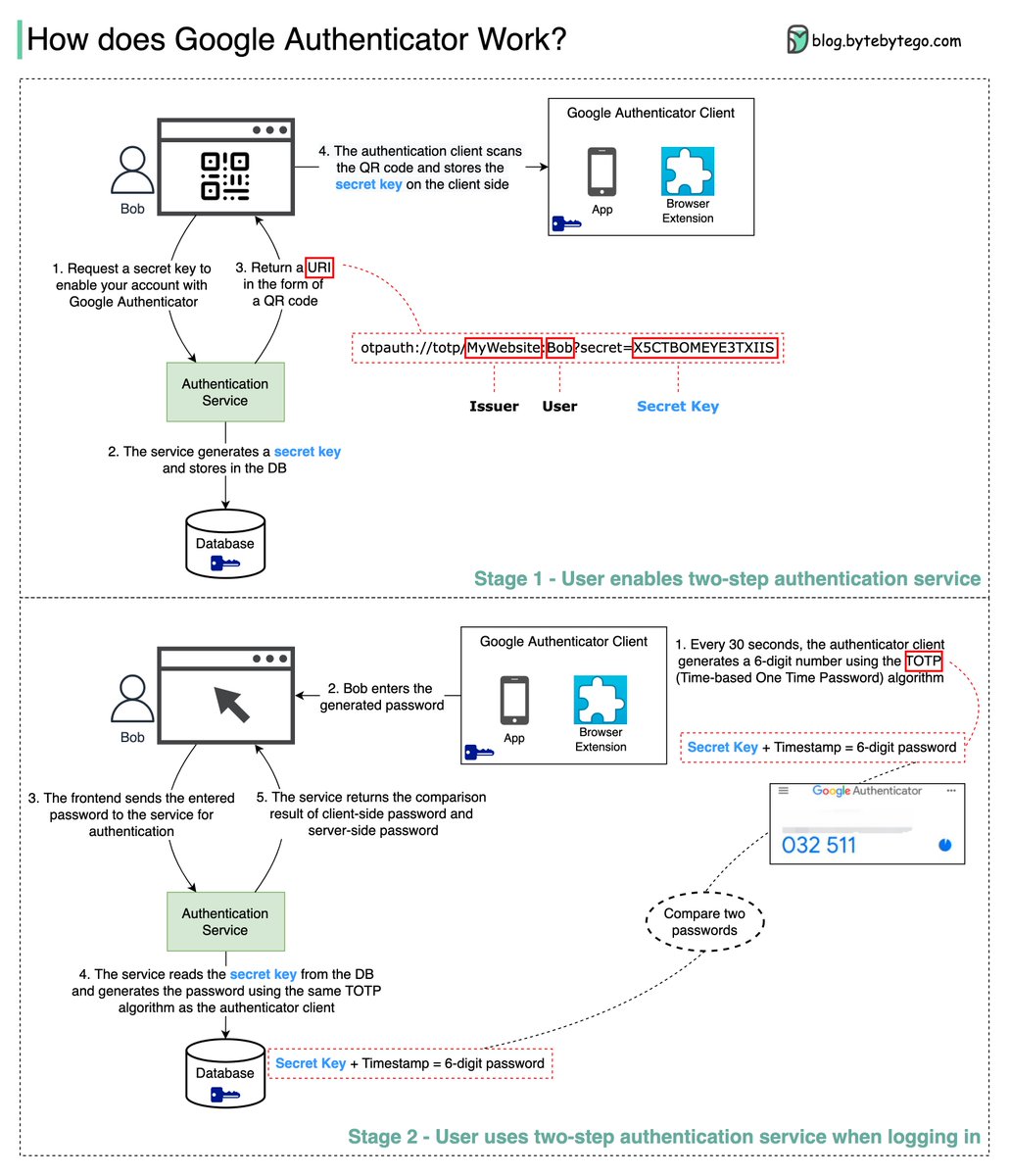
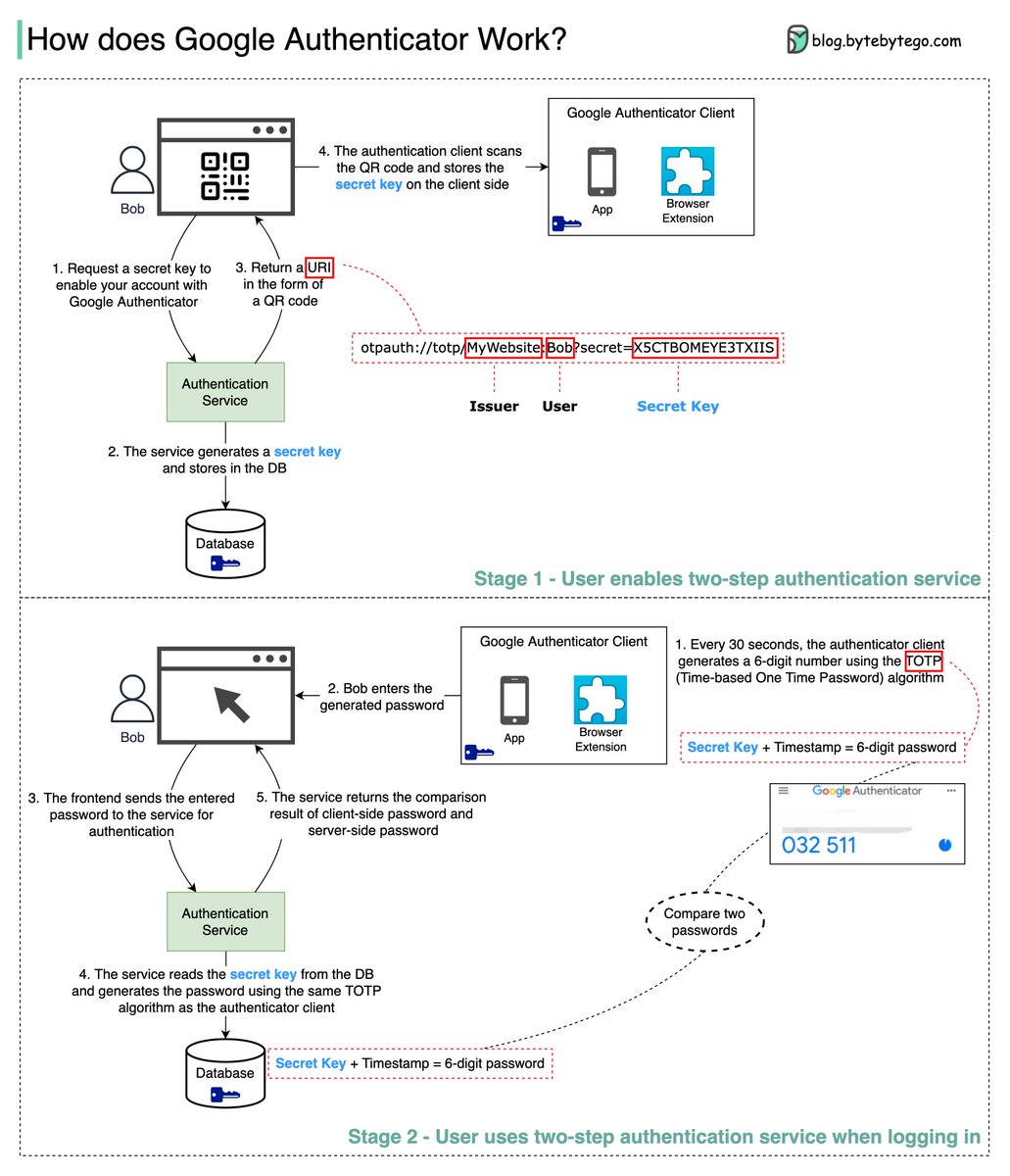
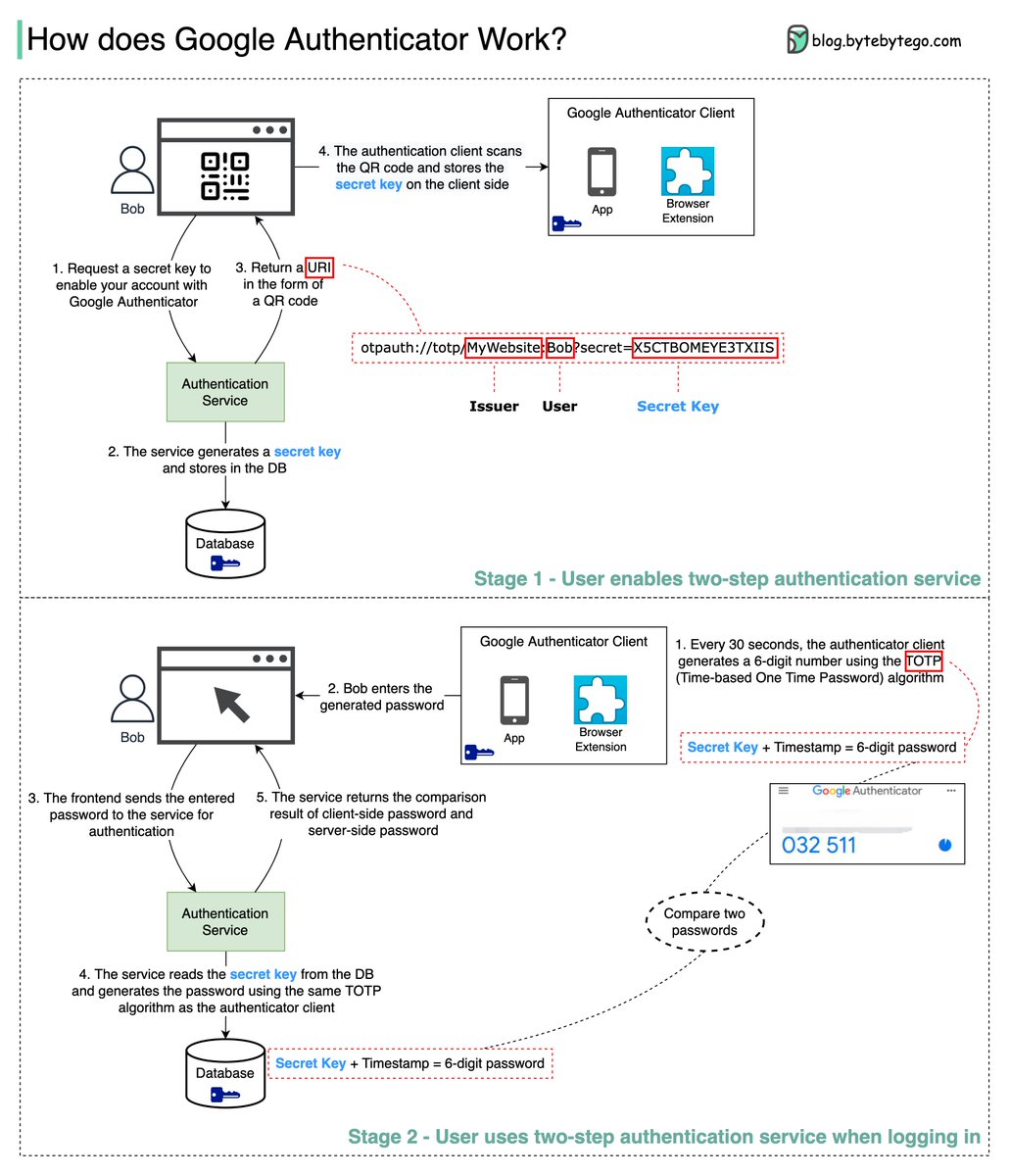
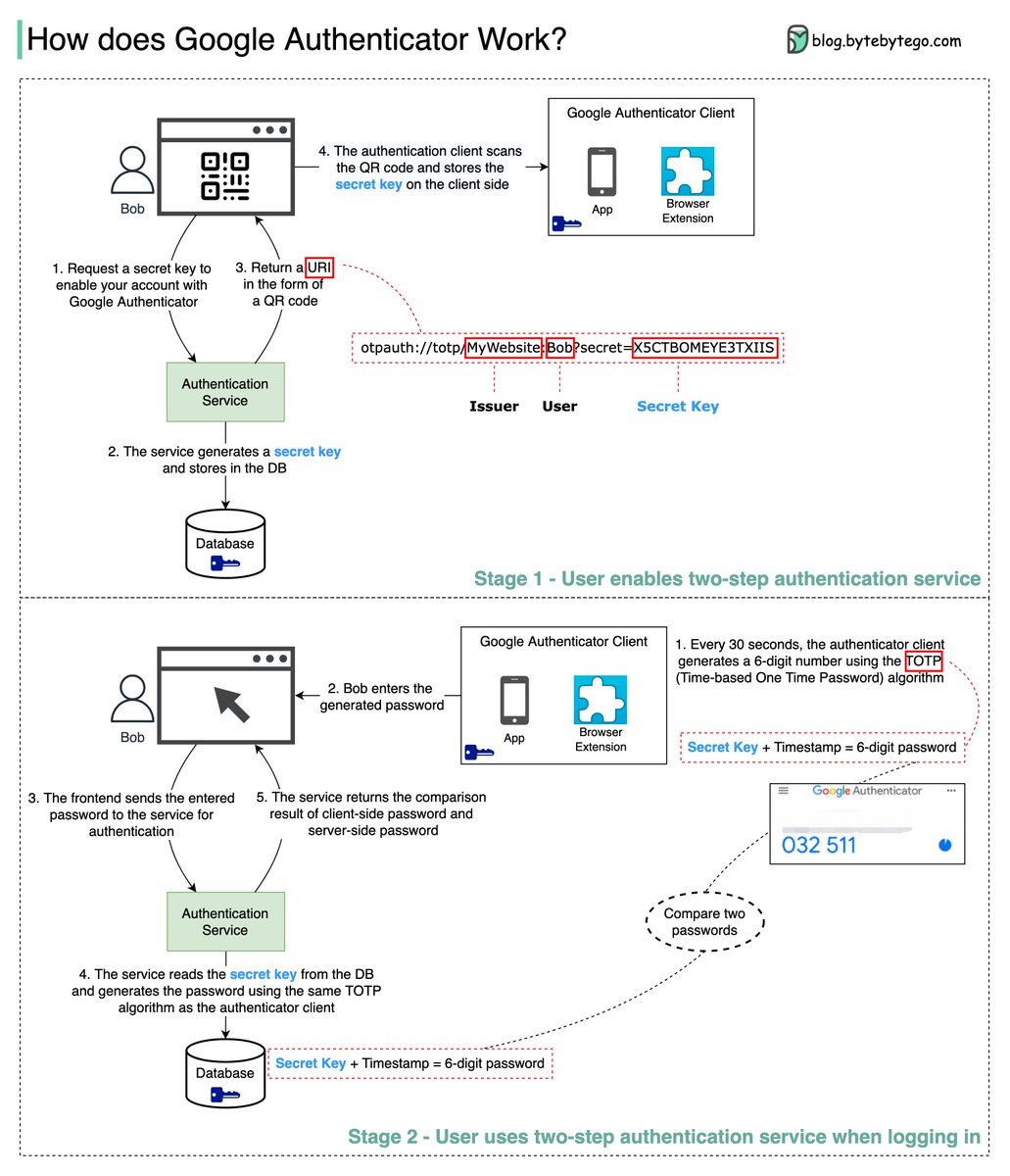
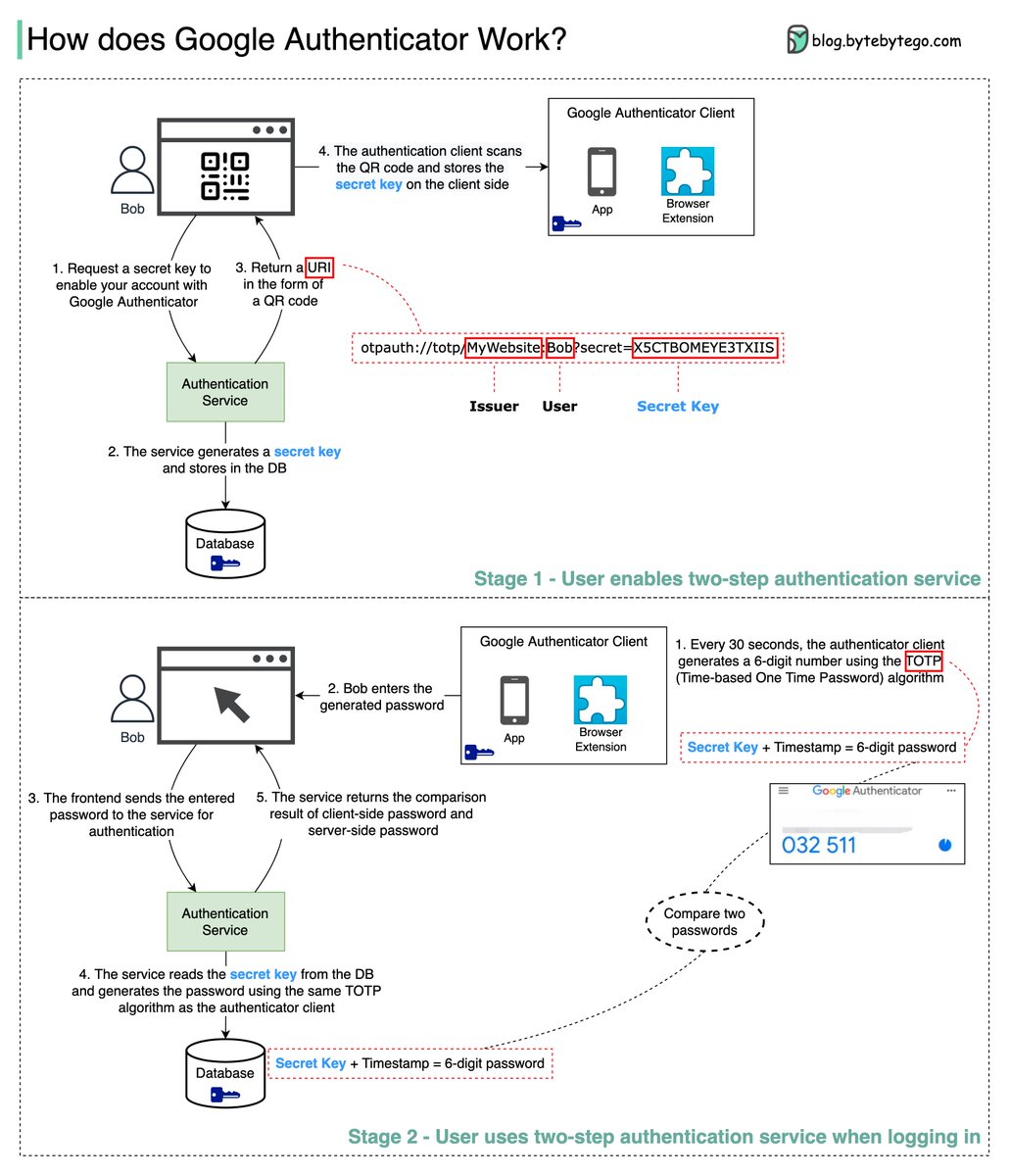
Google Authenticator is a software-based authenticator that implements a two-step verification service. The diagram below provides detail.
Is this authentication mechanism 𝐬𝐚𝐟𝐞?
🔹 Can the secret key be obtained by others?
We need to make sure the secret key is transmitted using HTTPS. The authenticator client and the database store the secret key, and we need to make sure the secret keys are encrypted.
🔹 Can the secret key be obtained by others?
We need to make sure the secret key is transmitted using HTTPS. The authenticator client and the database store the secret key, and we need to make sure the secret keys are encrypted.
🔹 Can the 6-digit password be guessed by hackers?
No. The password has 6 digits, so the generated password has 1 million combinations. Plus, the password changes every 30s. If hackers want to guess the password in 30 seconds, they need to enter 30,000 combinations per second.
No. The password has 6 digits, so the generated password has 1 million combinations. Plus, the password changes every 30s. If hackers want to guess the password in 30 seconds, they need to enter 30,000 combinations per second.
Over to you: What are some of the other 2-factor authentication devices you used?
Loading suggestions...