2/ @twilio handles SMS registrations for @signalapp.
They got targeted w/a phishing attack.
Attackers then used their access against some @signalapp users.
...& a bunch of other Twilio customers (editorial: yikes, more disclosures likely inbound).
twilio.com
They got targeted w/a phishing attack.
Attackers then used their access against some @signalapp users.
...& a bunch of other Twilio customers (editorial: yikes, more disclosures likely inbound).
twilio.com
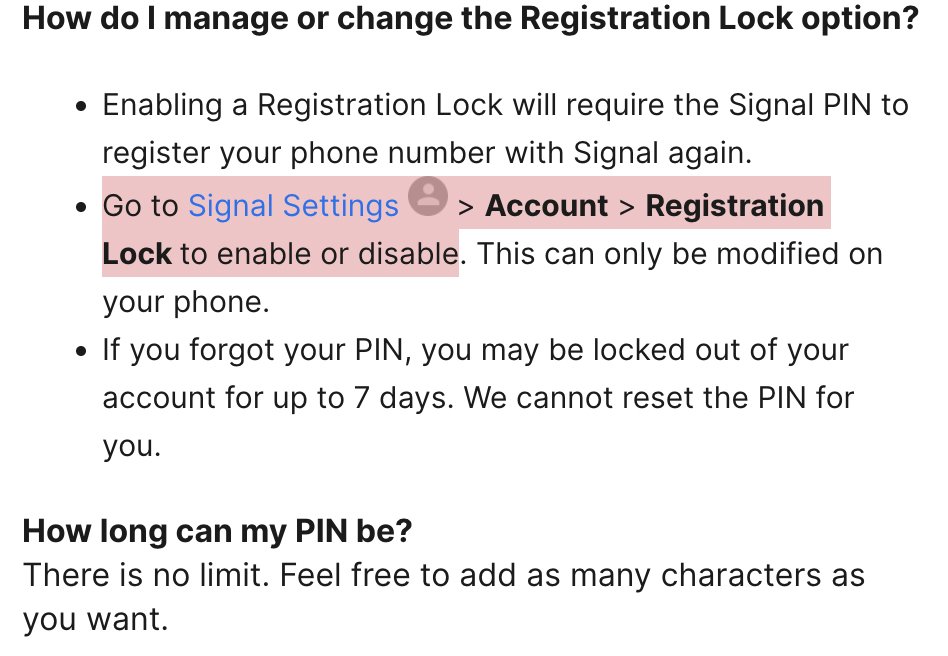
3/ If a targeted @signalapp user *hadn't enabled registration lock*, attackers could re-register their account on a new device.
They wouldn't get previous messages etc, but might be able to start sending & receiving messages intended for the victim.
support.signal.org
They wouldn't get previous messages etc, but might be able to start sending & receiving messages intended for the victim.
support.signal.org
4/ Lesson 1: This attack is Exhibit 2515 for why SMSes are a security weak point.
Accounts will keep being taken over.
Every app should have a version of registration lock / multi factor authentication that avoids SMS.
And they should be default-on.
Accounts will keep being taken over.
Every app should have a version of registration lock / multi factor authentication that avoids SMS.
And they should be default-on.
5/ Lesson 2: Companies like @twilio are lowkey critical internet infrastructure.
The registration & authentication SMSes they process make them a high-value target.
$TWLO et. al. must secure themselves accordingly.
The registration & authentication SMSes they process make them a high-value target.
$TWLO et. al. must secure themselves accordingly.
6/ I'm glad to see @signalapp is communicating around this.
I hope they have a path to move all their users to registration lock.
Ultimately, likelihood that their users will get targeted by sophisticated threats, including account takeovers, remains very high.
I hope they have a path to move all their users to registration lock.
Ultimately, likelihood that their users will get targeted by sophisticated threats, including account takeovers, remains very high.
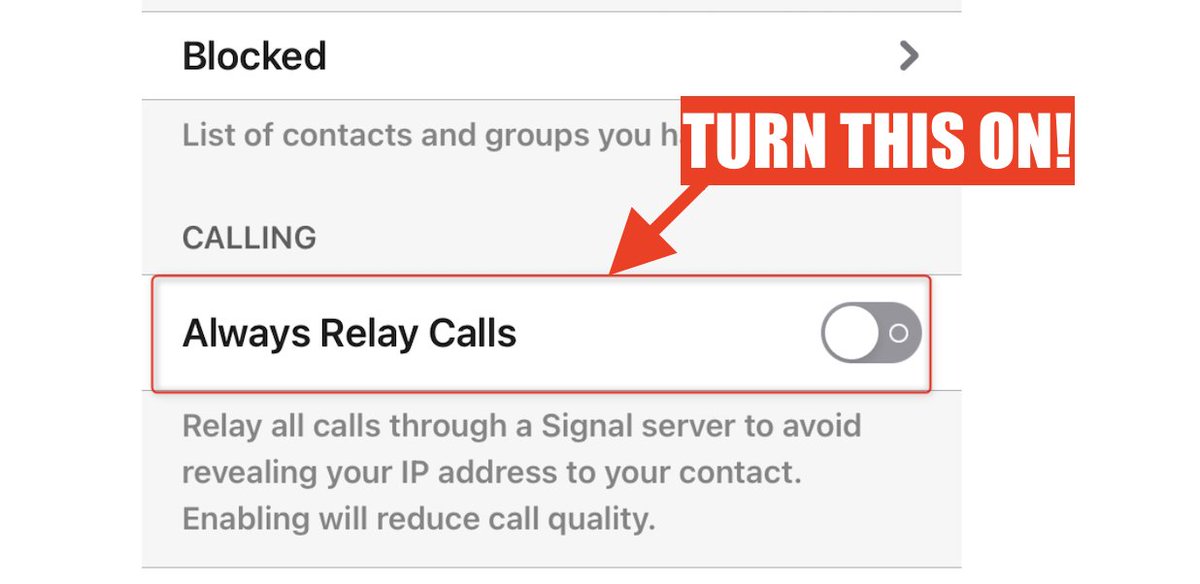
7/ Another tip: Always Relay Calls is another important @signalapp feature that I wish more people knew about.
By relaying your calls through servers run by Signal, it stops your Internet Service Provider (and others!) from seeing the IP addresses of the people you call.
By relaying your calls through servers run by Signal, it stops your Internet Service Provider (and others!) from seeing the IP addresses of the people you call.
Loading suggestions...