(2/25) The internet is a very public place. It basically works by blasting information at anyone listening, hoping it’ll get to its intended recipient.
Need to send a private message? Someone else WILL get a copy of the data; you’re going to need a cryptographic algorithm.
Need to send a private message? Someone else WILL get a copy of the data; you’re going to need a cryptographic algorithm.
(3/25) A cryptographic algorithm receives a message and an encryption key.
If the message is not encrypted, the algorithm will transform it into illegible nonsense, securing the data.
If the message is encrypted (and the key matches the encoding), the algorithm will decode it.
If the message is not encrypted, the algorithm will transform it into illegible nonsense, securing the data.
If the message is encrypted (and the key matches the encoding), the algorithm will decode it.
(4/25) Just treat encryption algorithms like a black box, let’s focus on the encryption keys.
Anyone that has a copy has access to your messages, so we need to ensure it stays secret between you and whoever you’re talking to.
So… how do we create a shared secret in public?
Anyone that has a copy has access to your messages, so we need to ensure it stays secret between you and whoever you’re talking to.
So… how do we create a shared secret in public?
(5/25) The first answer is Diffie-Hellman Key Exchange, a process that allows two entities to privately generate a shared secret by sharing public information.
(From here on there’s math, but it’s easy. You do need to know modular arithmetic, covered in the linked thread).
(From here on there’s math, but it’s easy. You do need to know modular arithmetic, covered in the linked thread).
(7/25) Let’s say you are listening to a Diffie-Hellman exchange. You are able to learn:
n = 23
g = 5
g^a mod n = 4
We know g^a has a remainder of 4… that’s not enough info. Does g^a = 27? 50? 73? There are literally infinite options.
n = 23
g = 5
g^a mod n = 4
We know g^a has a remainder of 4… that’s not enough info. Does g^a = 27? 50? 73? There are literally infinite options.
(8/25) One way to do it is to just start guessing. Quickly you’ll realize that a = 4. But with sufficiently large numbers, this can take forever.
Computation in one direction is easy, but undoing it is super difficult. We call these types of functions Trapdoor Functions.
Computation in one direction is easy, but undoing it is super difficult. We call these types of functions Trapdoor Functions.
(9/25) Trapdoor functions form the basis of strong encryption.
First Diffie-Hellman built a protocol around modular arithmetic.
Next, RSA extended on these ideas to build around factoring large numbers.
Unfortunately, we are starting to get better and better at solving both.
First Diffie-Hellman built a protocol around modular arithmetic.
Next, RSA extended on these ideas to build around factoring large numbers.
Unfortunately, we are starting to get better and better at solving both.
(10/25) In summary, this is the world we find ourselves in:
1) cryptography is about creating shared secrets using public channels
2) a trapdoor function provides the foundation for cryptographic security
3) we are getting to good at solving the old trapdoor functions
1) cryptography is about creating shared secrets using public channels
2) a trapdoor function provides the foundation for cryptographic security
3) we are getting to good at solving the old trapdoor functions
(13/25) If you’re paying close enough attention, you can already see the trapdoor function begin to form
Need a hint? Modular arithmetic was difficult to undo because you can’t tell how many times the value looped over the maximum (n). 1 iteration is indistinguishable from 1000
Need a hint? Modular arithmetic was difficult to undo because you can’t tell how many times the value looped over the maximum (n). 1 iteration is indistinguishable from 1000
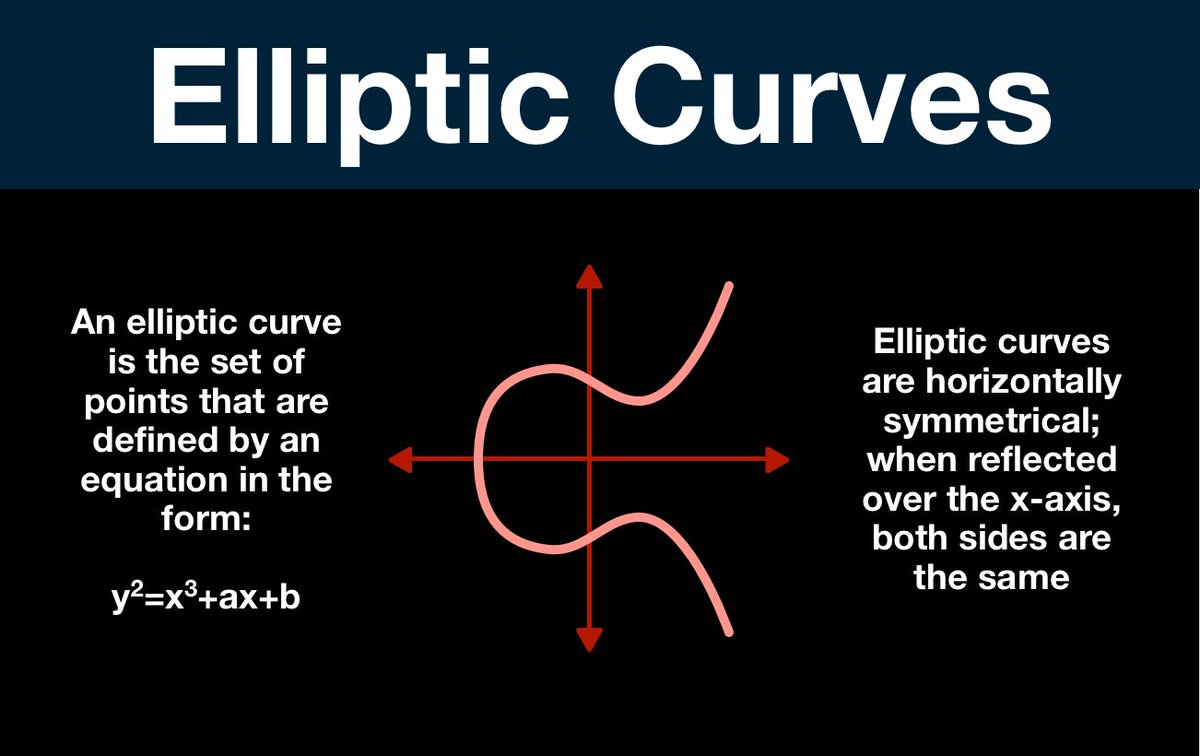
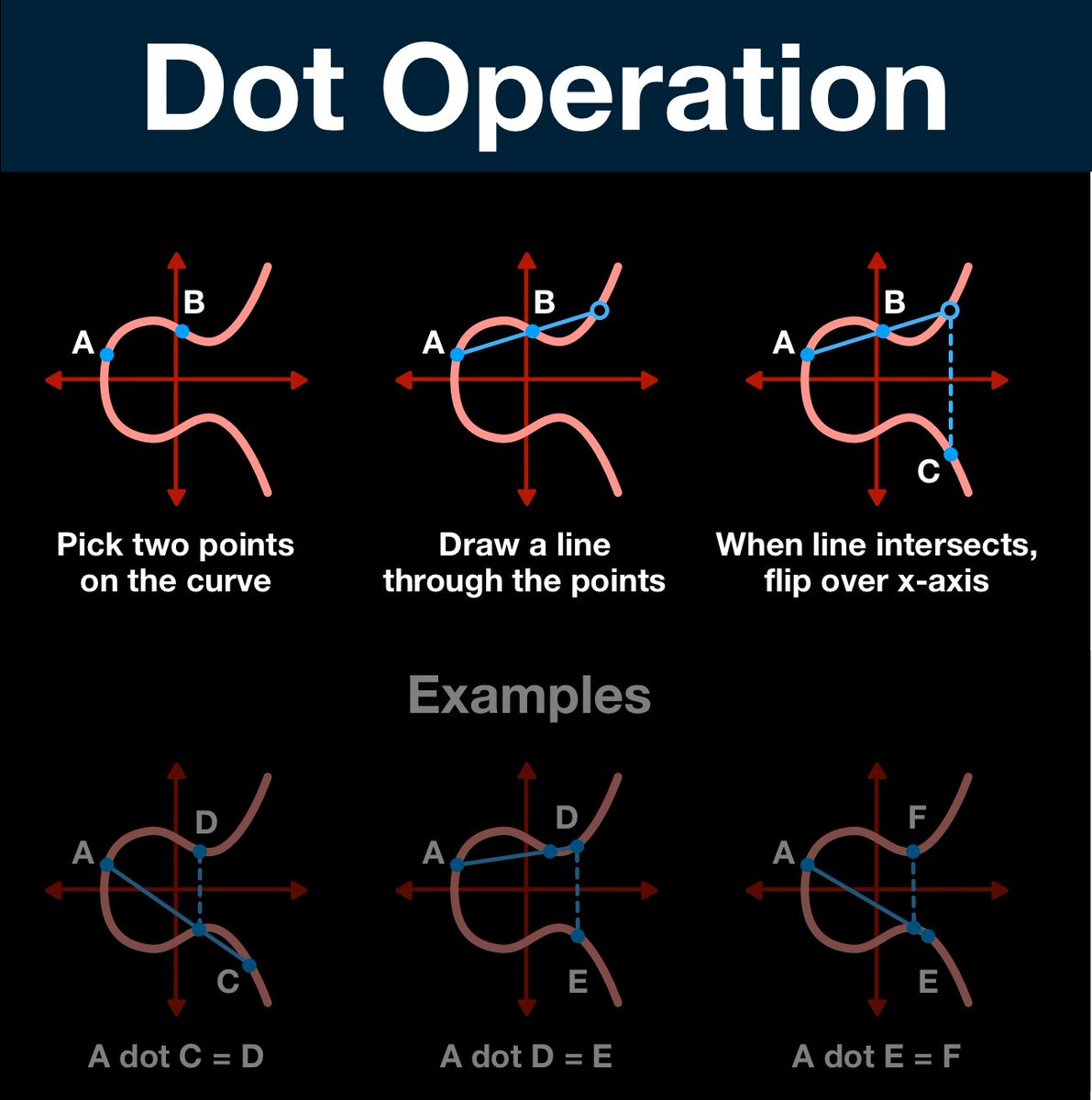
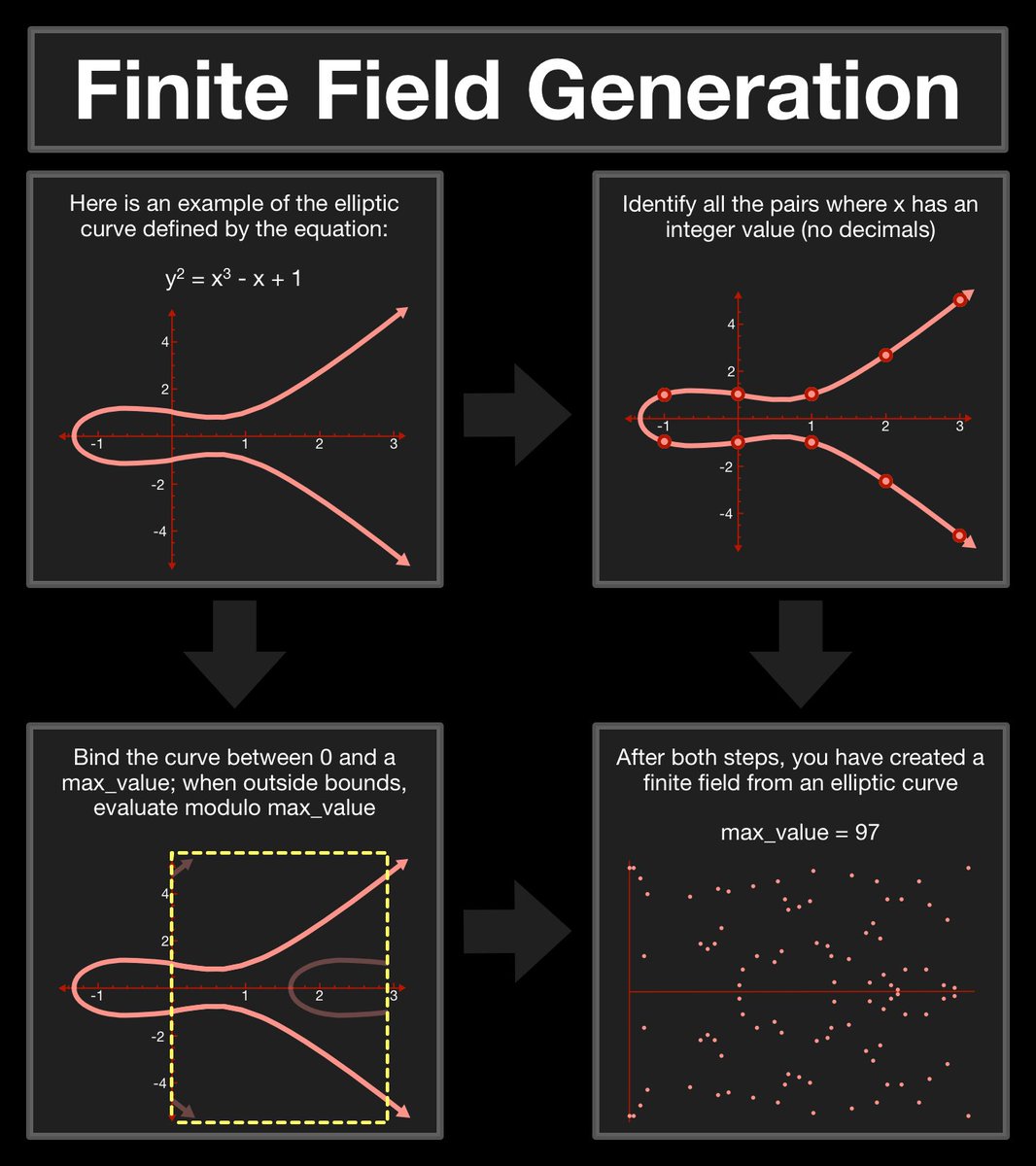
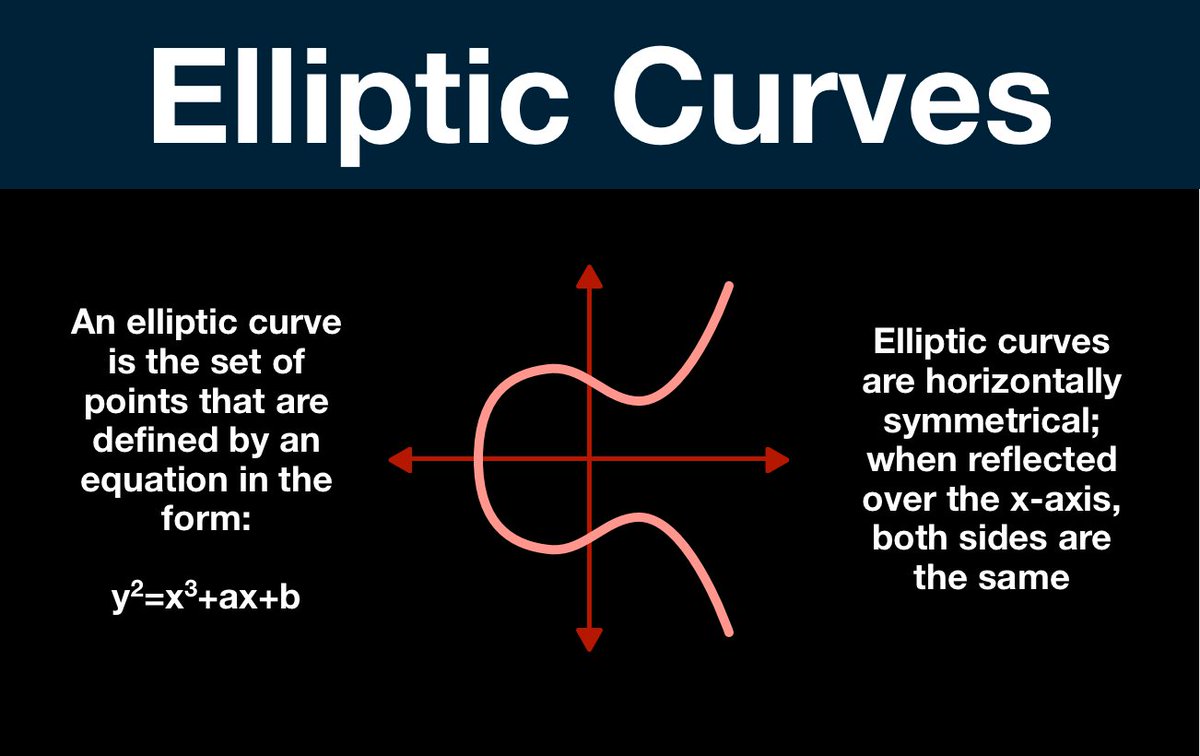
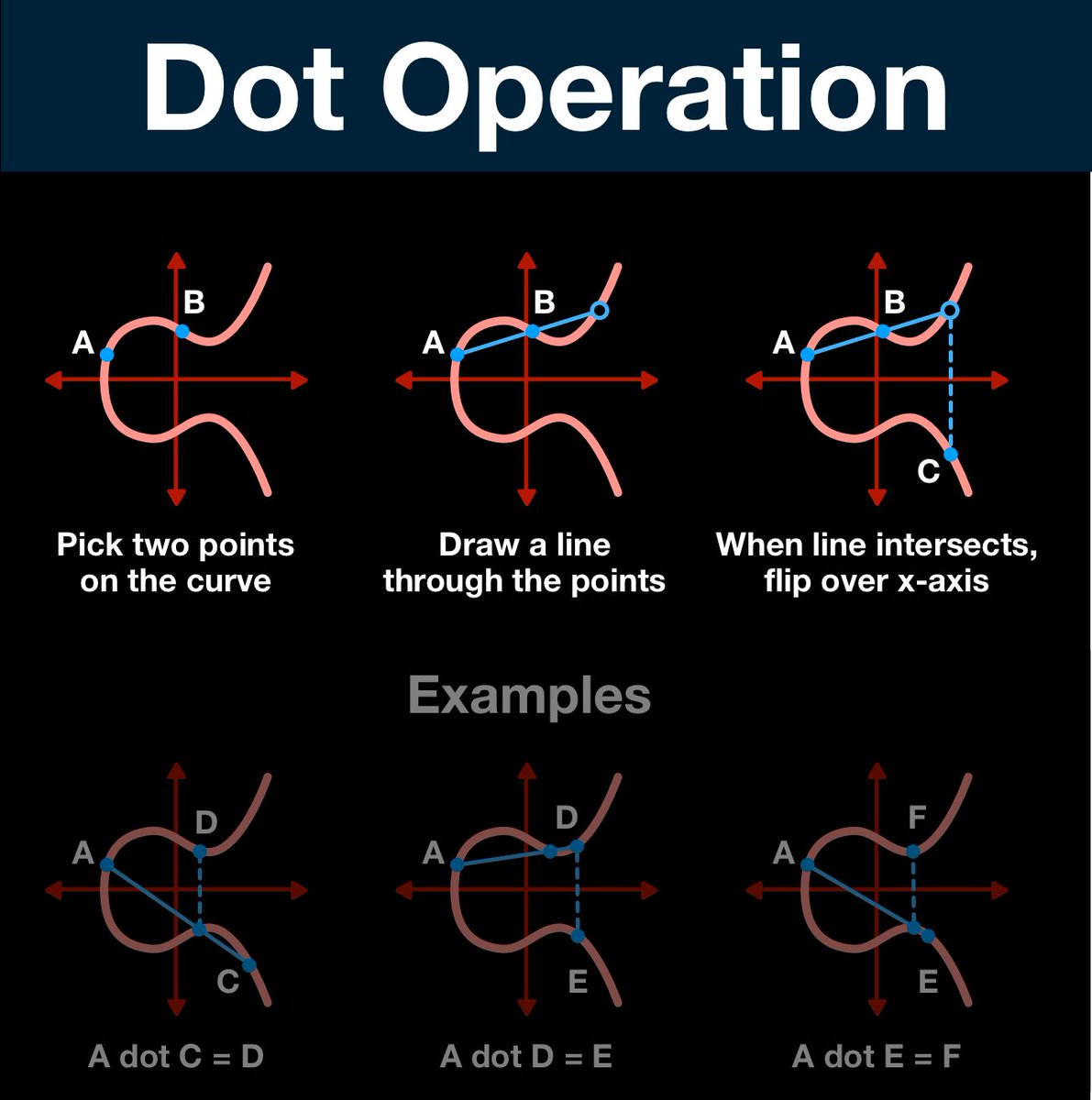
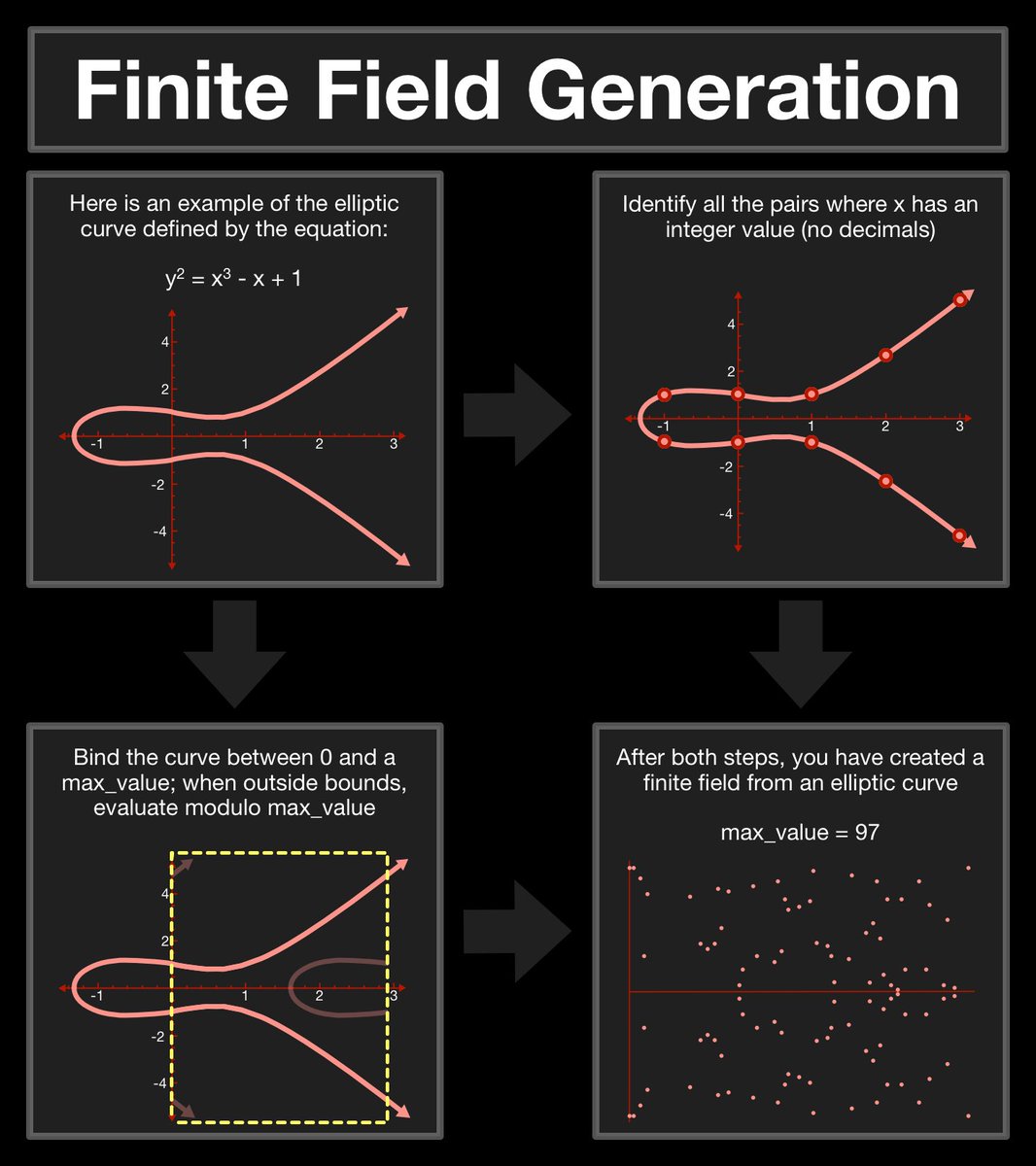
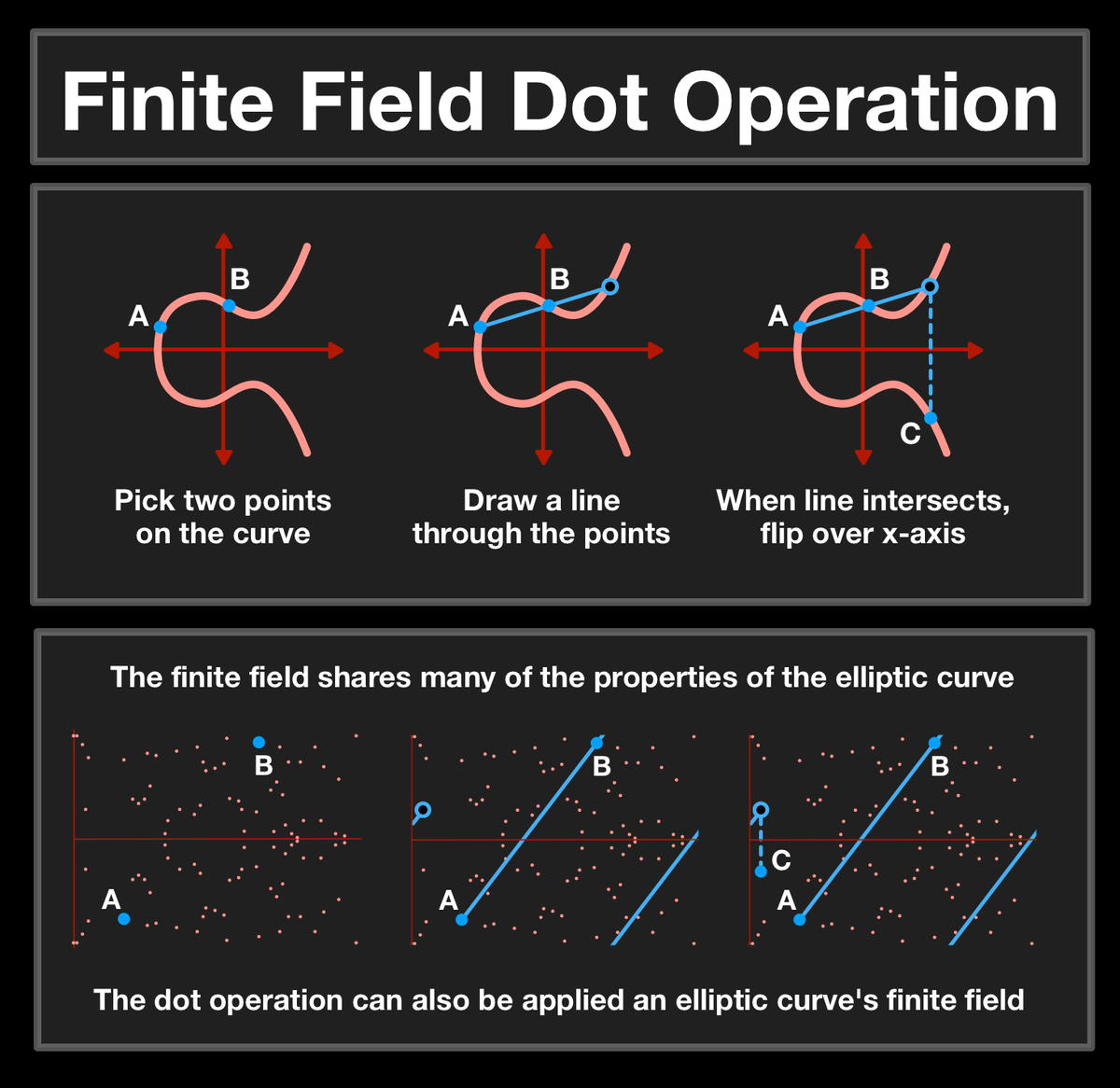
(14/25) This is what we are going to build out of the dot operation, but first we need to prepare our workspace.
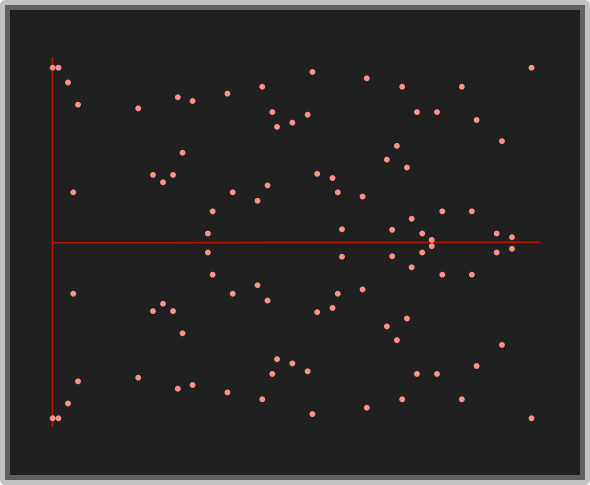
In its current state, an elliptic curve is much to infinite. How many values exist between x = 1 and x = 2? How big can the values get?
In its current state, an elliptic curve is much to infinite. How many values exist between x = 1 and x = 2? How big can the values get?
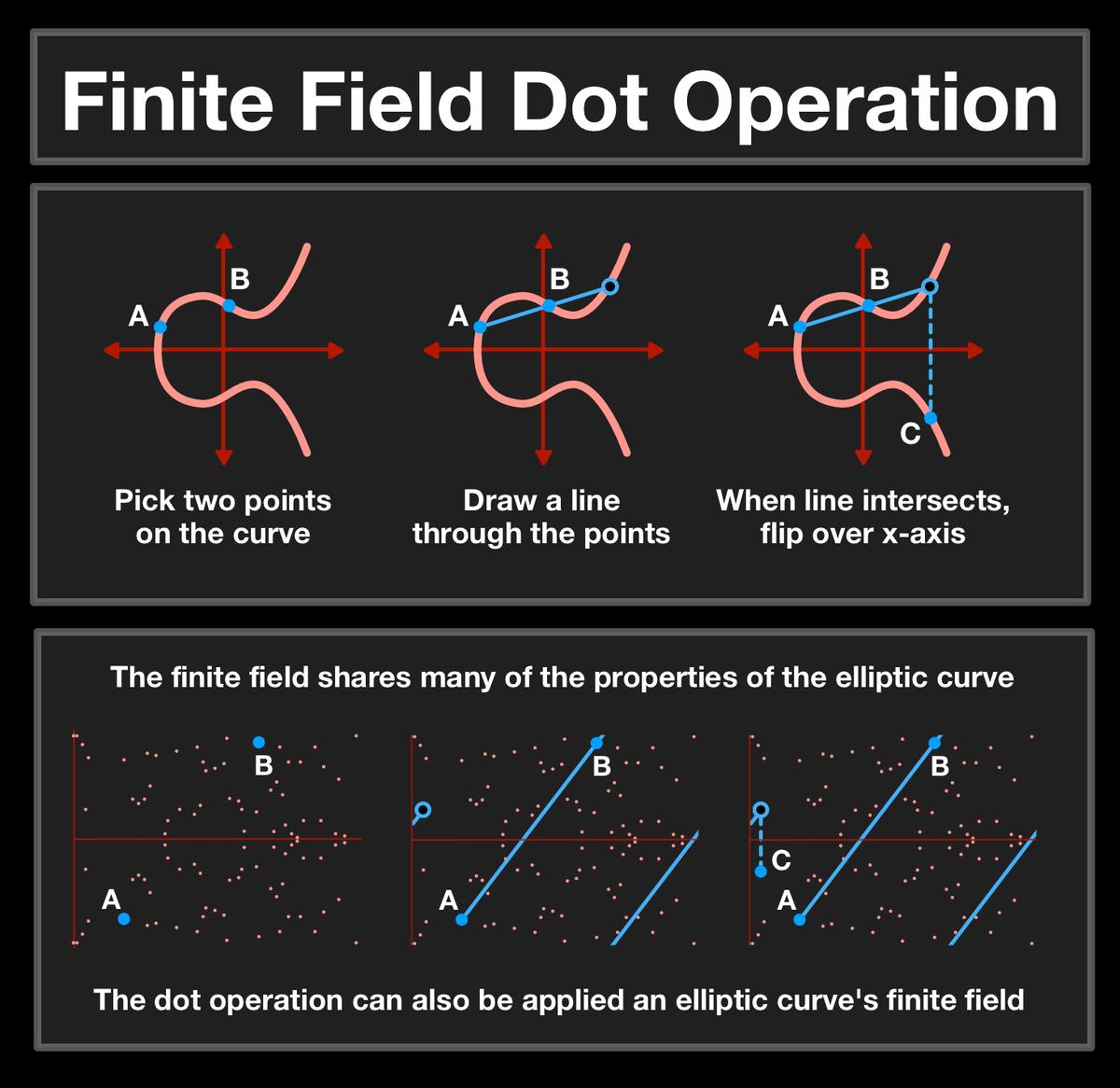
(19/25) Computing the number of times a point was dotted is a process called the elliptic curve discrete logarithm function; turns out that the function is INCREDIBLY hard to solve.
In fact, there isn't a better method than just guessing and checking.
In fact, there isn't a better method than just guessing and checking.
(20/25) Just like a Diffie-Hellman system, we can build a system based on the elliptic curve that uses this one-way function to create a shared secret.
Diffie-Hellman uses a prime maximum (n), a base public base (g) and a private key (a or b) to generate a shared secret.
Diffie-Hellman uses a prime maximum (n), a base public base (g) and a private key (a or b) to generate a shared secret.
(21/25) An elliptic curve system is (can be) defined by picking a prime number as a max, a curve equation and a public point on the curve.
A private key is a number PRIV, and a public key is the public point dotted with itself PRIV times.
A private key is a number PRIV, and a public key is the public point dotted with itself PRIV times.
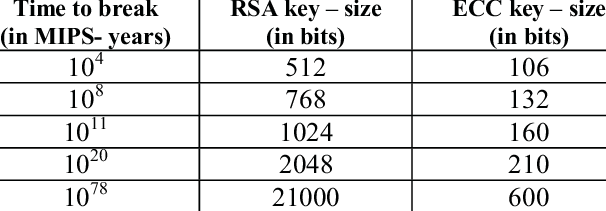
(22/25) When comparing elliptic curve and Diffie-Hellman (and RSA) cryptography, we must compare trapdoor functions.
We've made progress on factoring, improving our solving process and increasing computing power. Diffie-Hellman (and RSA) are becoming less and less secure.
We've made progress on factoring, improving our solving process and increasing computing power. Diffie-Hellman (and RSA) are becoming less and less secure.
(23/25) Elliptic curve discrete logarithm function? It's been ~30 years and STILL no one has anything better than guessing.
The result: for numbers of the same size, solving elliptic curve discrete logarithms is significantly harder than factoring.
The result: for numbers of the same size, solving elliptic curve discrete logarithms is significantly harder than factoring.
(24/25) Arjen Lenstra framed it best in Universal Security
Tl;dr breaking a 228-bit RSA key requires less energy to than it takes to boil a teaspoon of water. Breaking a 228-bit elliptic curve key requires enough energy to boil all the water on earth.
eprint.iacr.org
Tl;dr breaking a 228-bit RSA key requires less energy to than it takes to boil a teaspoon of water. Breaking a 228-bit elliptic curve key requires enough energy to boil all the water on earth.
eprint.iacr.org
(25/25) Cryptography is the quest to transfer private data through public channels. Alas, we live in a human world; humans inevitably try to break into secrets
First, Diffie and Hellman (& Merkle) gave us a tool; one that's aging (quickly)
Fortunately, we have elliptic curves!
First, Diffie and Hellman (& Merkle) gave us a tool; one that's aging (quickly)
Fortunately, we have elliptic curves!
Like what you read? Help me spread the word by retweeting the thread (linked below).
Follow me for more explainers and as much alpha as I can possibly serve.
Follow me for more explainers and as much alpha as I can possibly serve.
Loading suggestions...