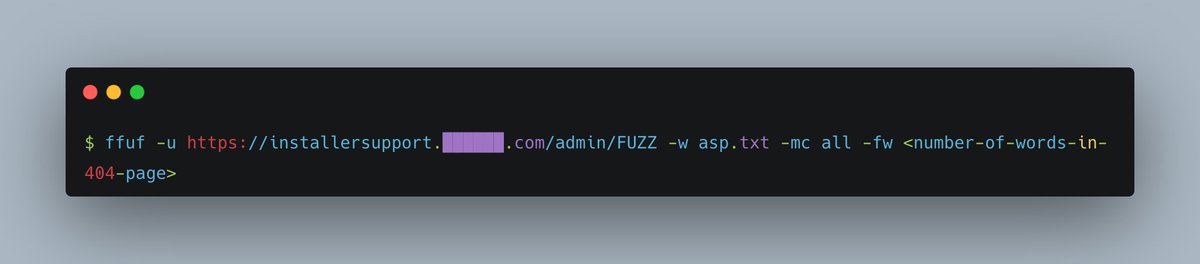
2. I wanted to know what files were on the host, without brute-forcing.
getallurls (gau) fetches known URLs from:
• AlienVault's Open Threat Exchange
• the Wayback Machine
• Common Crawl
• URLScan.
So I ran it against the domain:
$ gau installersupport.██████.com
getallurls (gau) fetches known URLs from:
• AlienVault's Open Threat Exchange
• the Wayback Machine
• Common Crawl
• URLScan.
So I ran it against the domain:
$ gau installersupport.██████.com
3. Pages of results!
After scrolling through them, one caught my eye:
hxxps://installersupport.██████.com/admin/admin_login.asp
The "admin" folder indicated there's likely interesting functionality on this host.
Something you'd want access to.
After scrolling through them, one caught my eye:
hxxps://installersupport.██████.com/admin/admin_login.asp
The "admin" folder indicated there's likely interesting functionality on this host.
Something you'd want access to.
4. So, I visited the URL.
It asked for a username and password.
Obviously I had to try entering default credentials like
• admin:admin
• admin:password
• admin:password123
• test:test
I had no luck.
Bummer. I had to try something else:
It asked for a username and password.
Obviously I had to try entering default credentials like
• admin:admin
• admin:password
• admin:password123
• test:test
I had no luck.
Bummer. I had to try something else:
6. I visited the first one:
/admin/userinfo.asp
The page didn't check for authentication.
It was just an iframe to another .aspx file:
/crd/installersupport/NewEditUserInfo.aspx
This responded with 500 Internal Server Error.
Hm...Why?
/admin/userinfo.asp
The page didn't check for authentication.
It was just an iframe to another .aspx file:
/crd/installersupport/NewEditUserInfo.aspx
This responded with 500 Internal Server Error.
Hm...Why?
7. So, I visited the second one:
/admin/searchresult.asp
It had the same response as the first one! Almost...
After looking closer, I realized the URL it iframe'd to had extra parameters!
/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=
/admin/searchresult.asp
It had the same response as the first one! Almost...
After looking closer, I realized the URL it iframe'd to had extra parameters!
/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=
8. I visited the endpoint, with the extra parameters.
hxxps://installersupport.██████.com/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=
The page responded with a title: “User Info”.
But there was an error: “User Name is missing”
hxxps://installersupport.██████.com/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=
The page responded with a title: “User Info”.
But there was an error: “User Name is missing”
9. Well, what's `UserID` expecting?
A numeric user ID?
So, I used Burp Suite Intruder to brute-force the UserId parameter.
After a minute, it found a valid id: 2000953
So I visited:
/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=2000953
It returned
A numeric user ID?
So, I used Burp Suite Intruder to brute-force the UserId parameter.
After a minute, it found a valid id: 2000953
So I visited:
/crd/installersupport/NewEditUserInfo.aspx?action=editaccountinfo&UserId=2000953
It returned
10. the users:
• Name
• Email address
• Phone number
• Address
Yikes...
Then randomly, I remembered that I registered an account in this company's mobile app. Using my email.
I hadn’t seen a numeric ID in the app before.
But, this web application also seemed unrelated...
• Name
• Email address
• Phone number
• Address
Yikes...
Then randomly, I remembered that I registered an account in this company's mobile app. Using my email.
I hadn’t seen a numeric ID in the app before.
But, this web application also seemed unrelated...
12. I wanted to verify that this data was fresh.
So, In the mobile app, I created another account.
I targeted the new account and it worked!!
I reported it to the company's bug bounty program on @Hacker0x01
They fixed it and I was eventually rewarded for it!
So, In the mobile app, I created another account.
I targeted the new account and it worked!!
I reported it to the company's bug bounty program on @Hacker0x01
They fixed it and I was eventually rewarded for it!
@Hacker0x01 Do your employees/coworkers struggle to catch phishing emails or texts?
If so, you should join the @BreachlessAI waitlist!
We're working on a better way to catch phishing.
We'd love your feedback.
breachless.ai
If so, you should join the @BreachlessAI waitlist!
We're working on a better way to catch phishing.
We'd love your feedback.
breachless.ai
Thanks for reading.
Here's the top:
Here's the top:
Loading suggestions...