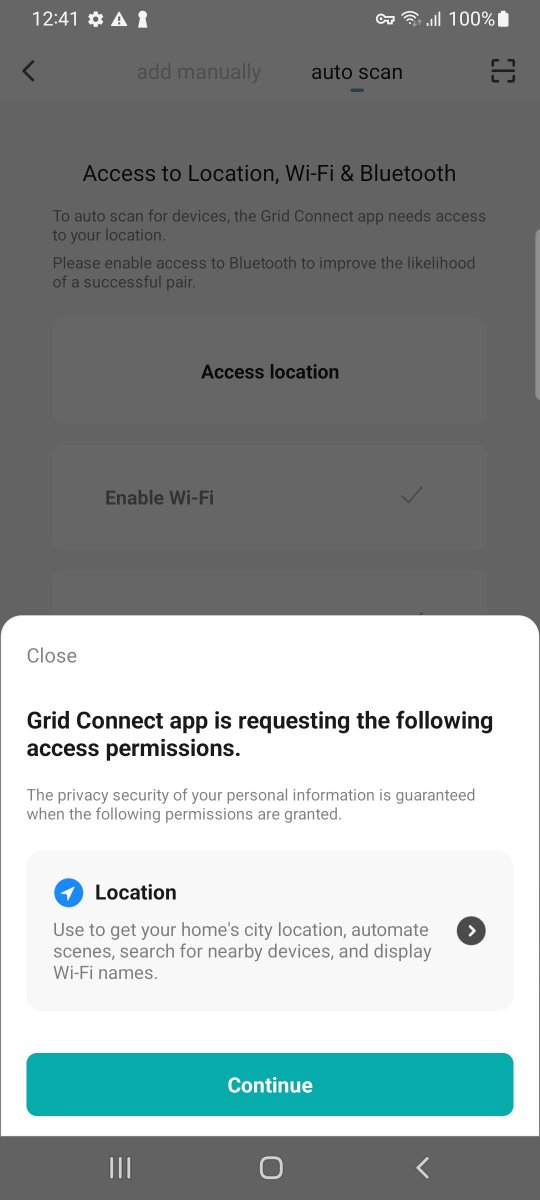
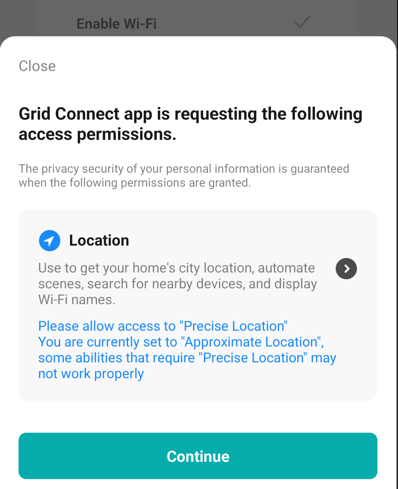
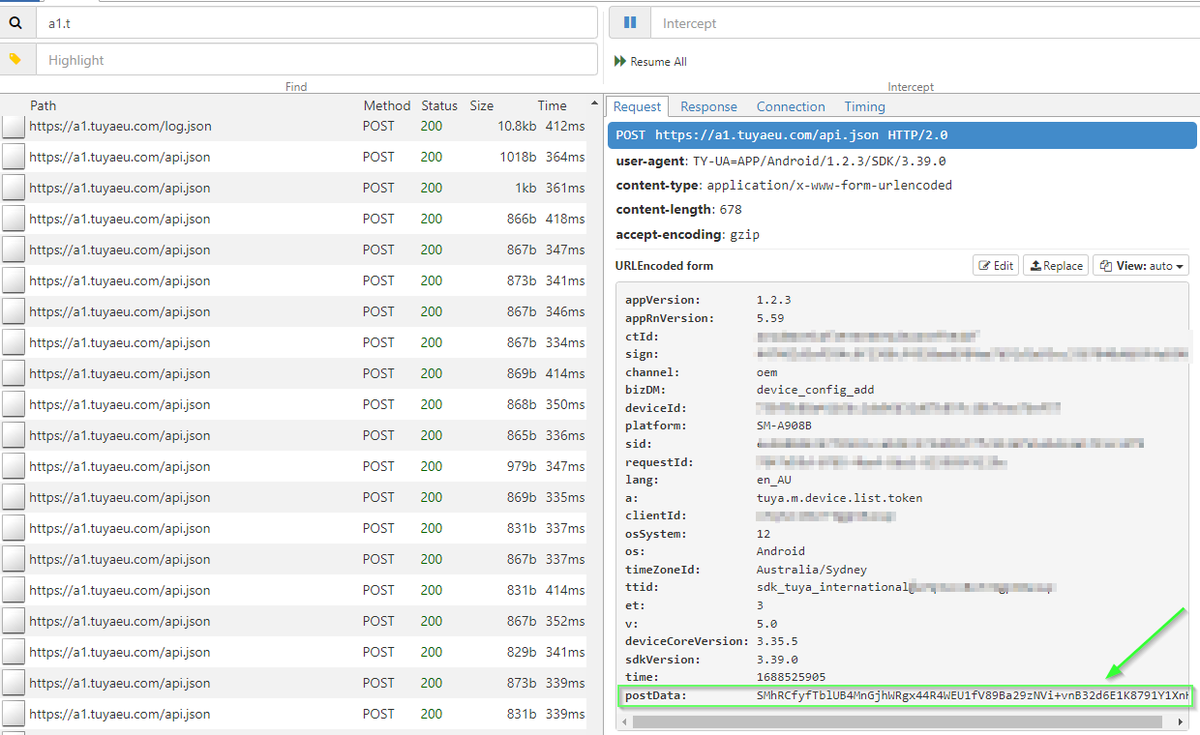
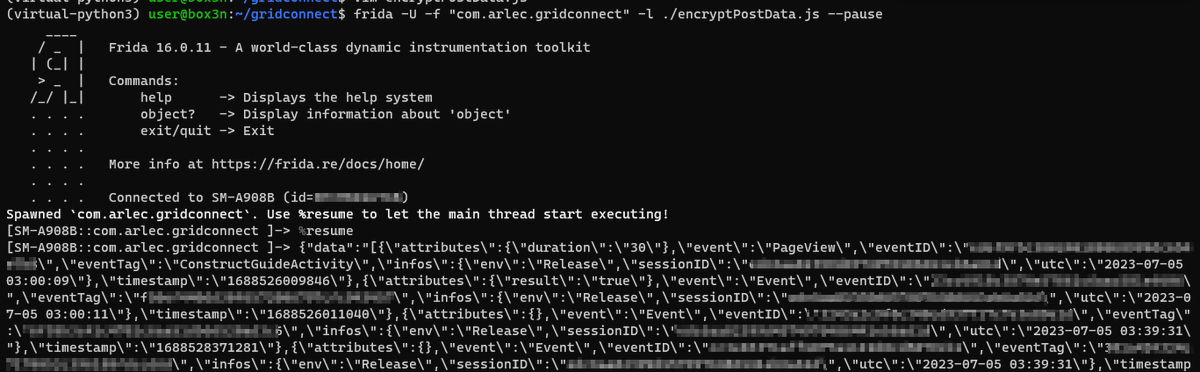
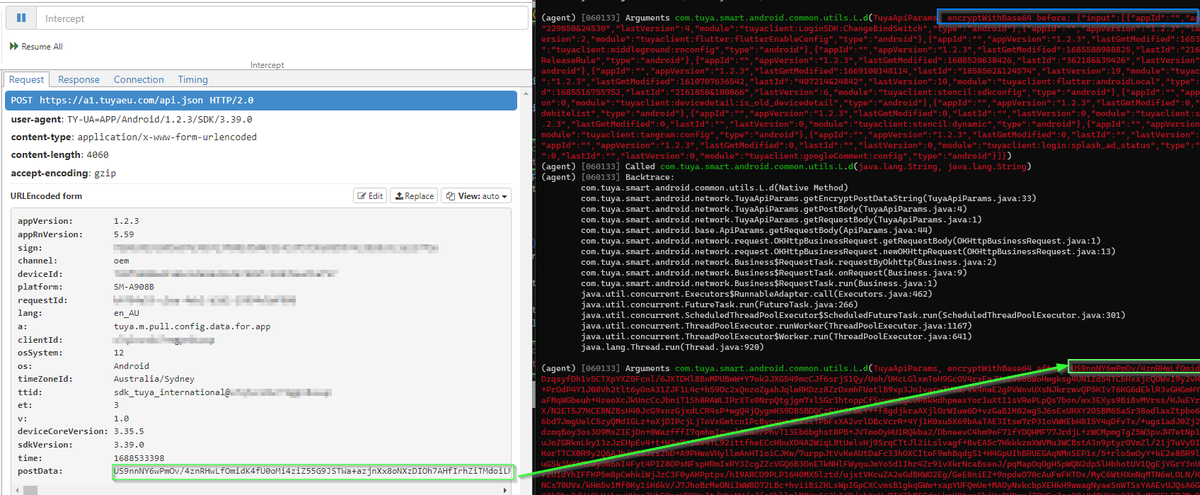
Time to fire up trusty #mitmproxy to look at the network traffic. Traffic is going to tuyaeu.com. Familiar domain. I came across Tuya used in a Mirabella Genio Smart light I got at a supermarket.
Tuya is an IoT OEM found everywhere.
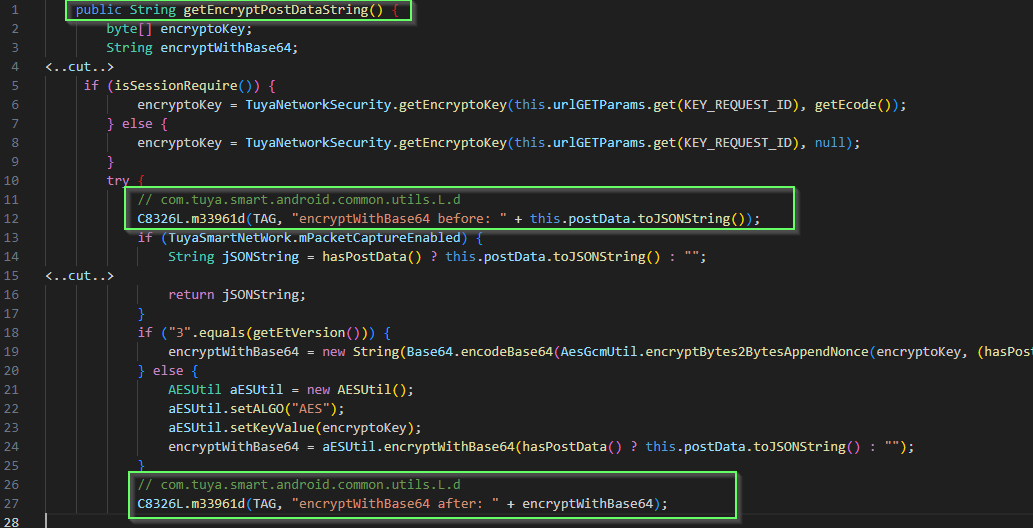
postData is encrypted.
(4/n)
Tuya is an IoT OEM found everywhere.
postData is encrypted.
(4/n)
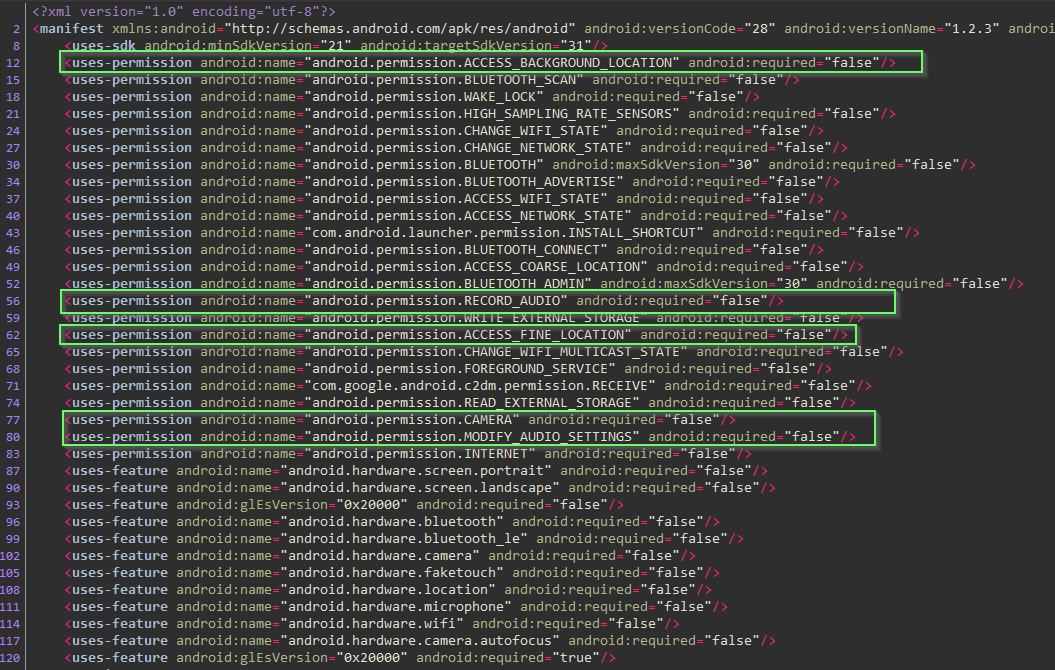
Let's pull the .apk from the device and take a look at the manifest. We could of course grab it from APK Pure.
m.apkpure.com
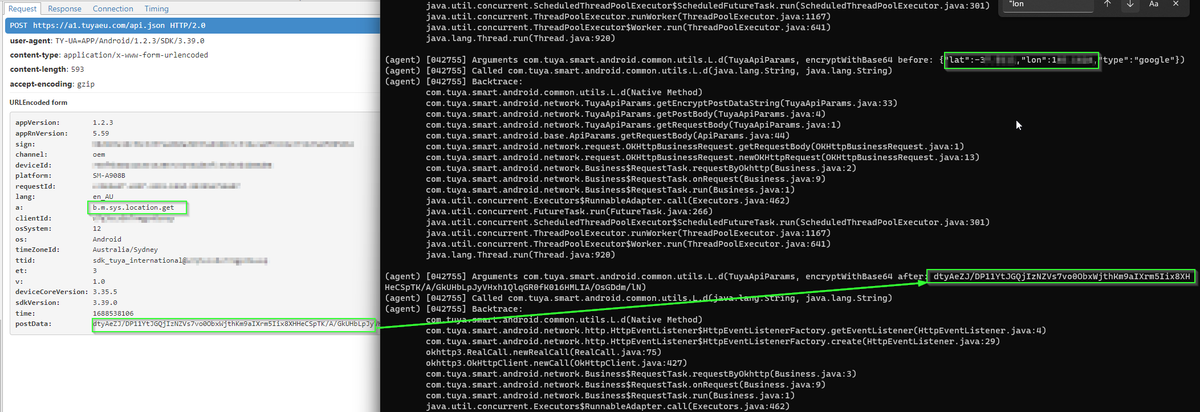
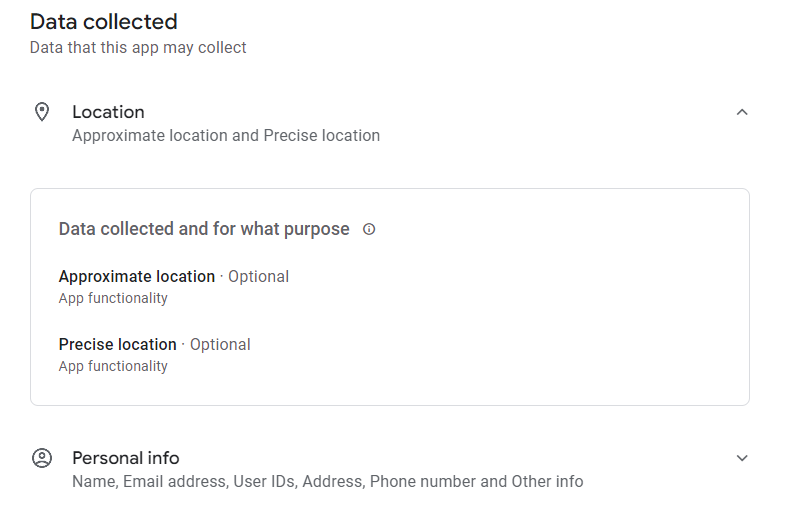
Yikes! recording audio, access to camera, location..
Assume there is a legitimate functional use for all of this. Trust but verify?
(5/n)
m.apkpure.com
Yikes! recording audio, access to camera, location..
Assume there is a legitimate functional use for all of this. Trust but verify?
(5/n)
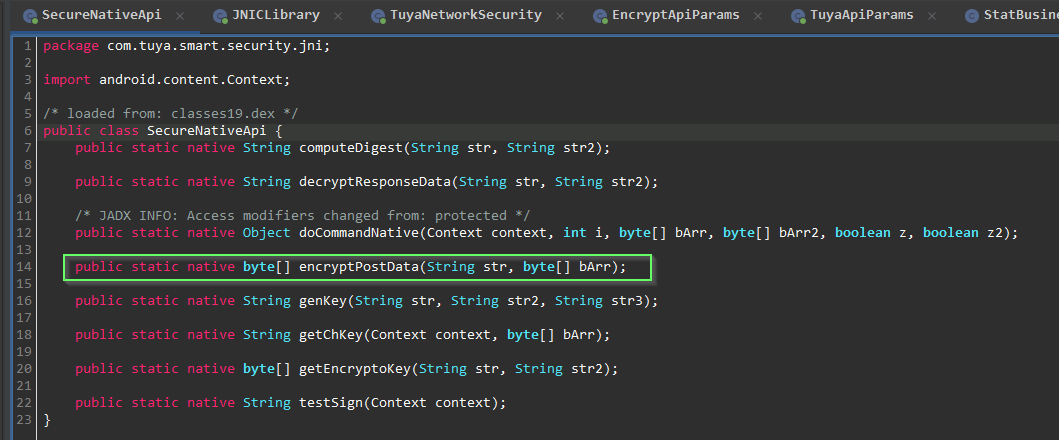
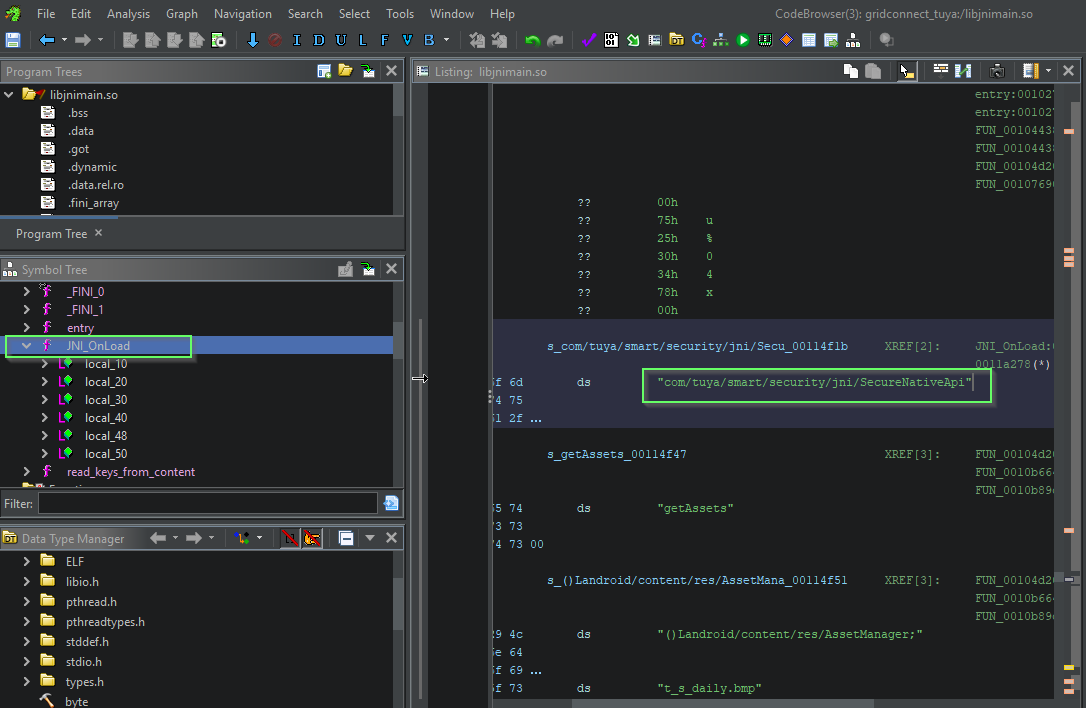
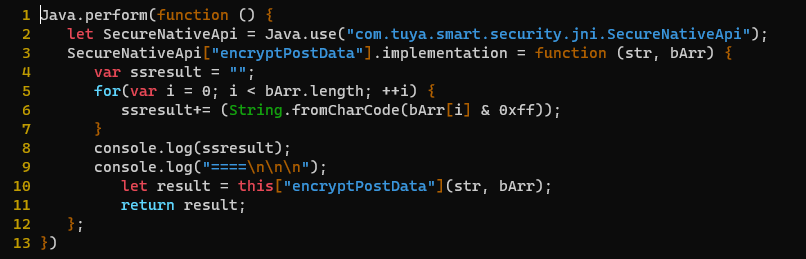
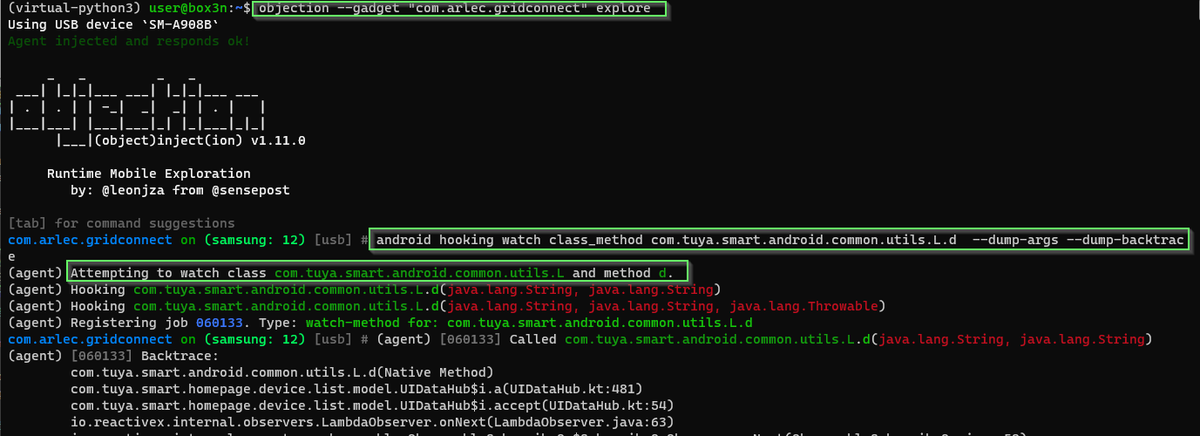
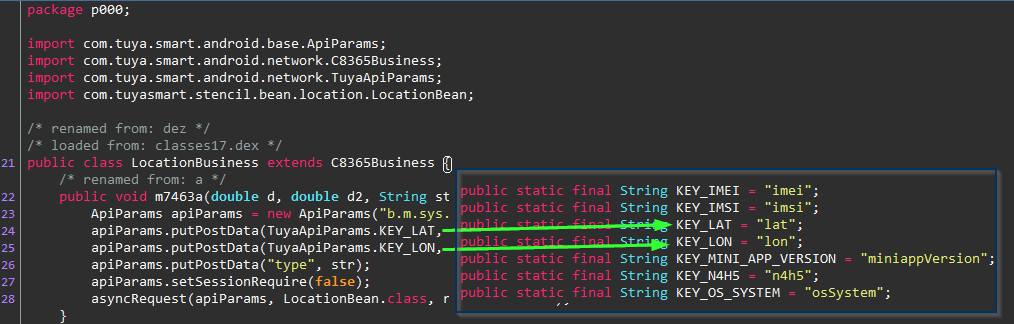
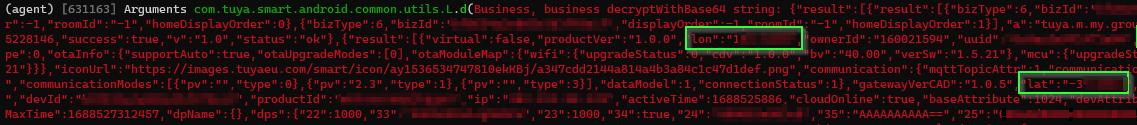
Dynamic instrumentation with #frida will really speed things up. JADX can emit a boiler plate hooking .js snippet to use in Frida. We just need to modify to to convert the plaintext byte array passed into encryptPostData from signed integers into a readable string.
(7/n)
(7/n)
Going to wrap up the live tweeting on this one.
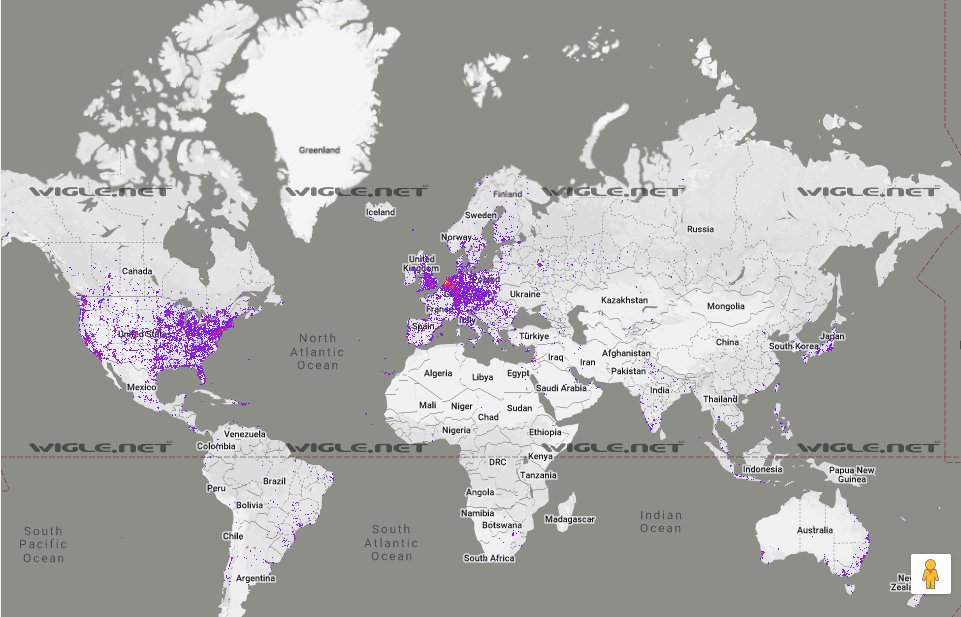
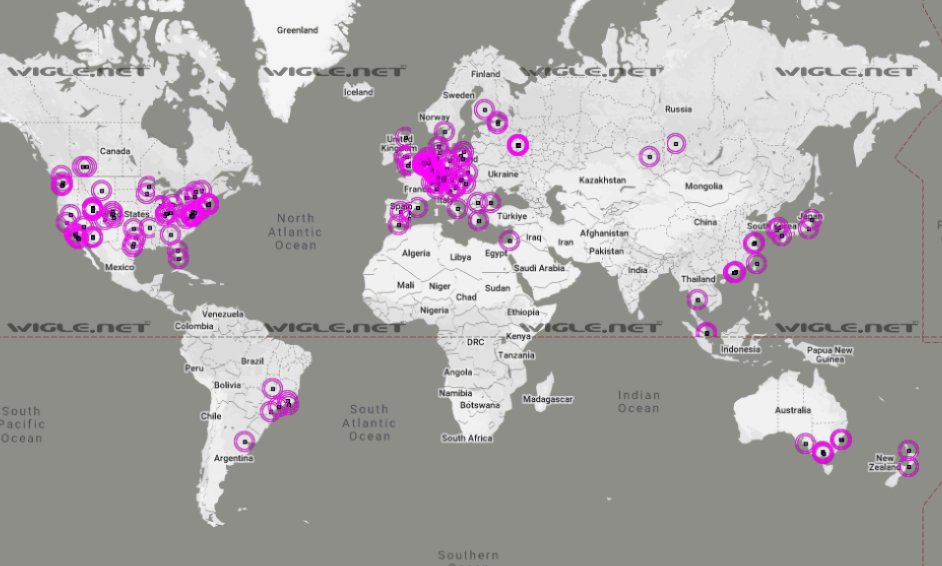
If you found this interesting/helpful, feel free to like/retweet. We need as many people as we can to be encouraged to discover and call out companies that harvest location data from their devices. 15/15
If you found this interesting/helpful, feel free to like/retweet. We need as many people as we can to be encouraged to discover and call out companies that harvest location data from their devices. 15/15
Loading suggestions...