☑️ In this lab, VirtualBox will be used for virtualization
and network isolation of all virtual machines from internet & and real network.
and network isolation of all virtual machines from internet & and real network.
Requirements :
1⃣ A decent laptop or desktop with preferably 16 GB RAM or more.
2⃣Min 40 GB of free disk space .
1⃣ A decent laptop or desktop with preferably 16 GB RAM or more.
2⃣Min 40 GB of free disk space .
1. Download And Install VirtualBox
👉 Open a browser and navigate to the official VirtualBox download page.
👉 Click to download the VirtualBox installation package according to your operating system.
virtualbox.org
👉 Open a browser and navigate to the official VirtualBox download page.
👉 Click to download the VirtualBox installation package according to your operating system.
virtualbox.org
Step-2. Install Kali Linux in VirtualBox
👉 Download the Kali Linux installation image and do a manual install in VirtualBox like you would do on a physical machine.
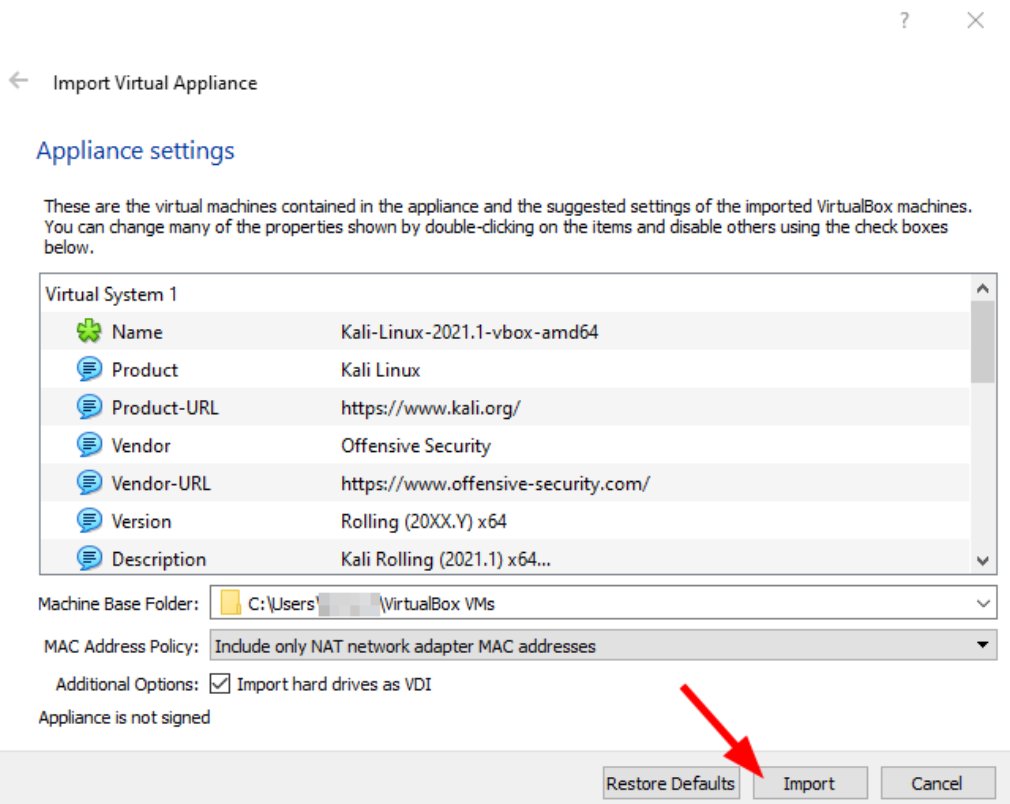
👉 Download Kali Linux pre-made VM and import it into VirtualBox.
👉 Download the Kali Linux installation image and do a manual install in VirtualBox like you would do on a physical machine.
👉 Download Kali Linux pre-made VM and import it into VirtualBox.
Step 3: Install Windows 10 on VirtualBox
If you own a license copy of Windows 10, you can
install it on VirtualBox very much the same way you
would install it on your physical machine.
If you don't have
Microsoft provides a Windows 10 VM for development purposes.
If you own a license copy of Windows 10, you can
install it on VirtualBox very much the same way you
would install it on your physical machine.
If you don't have
Microsoft provides a Windows 10 VM for development purposes.
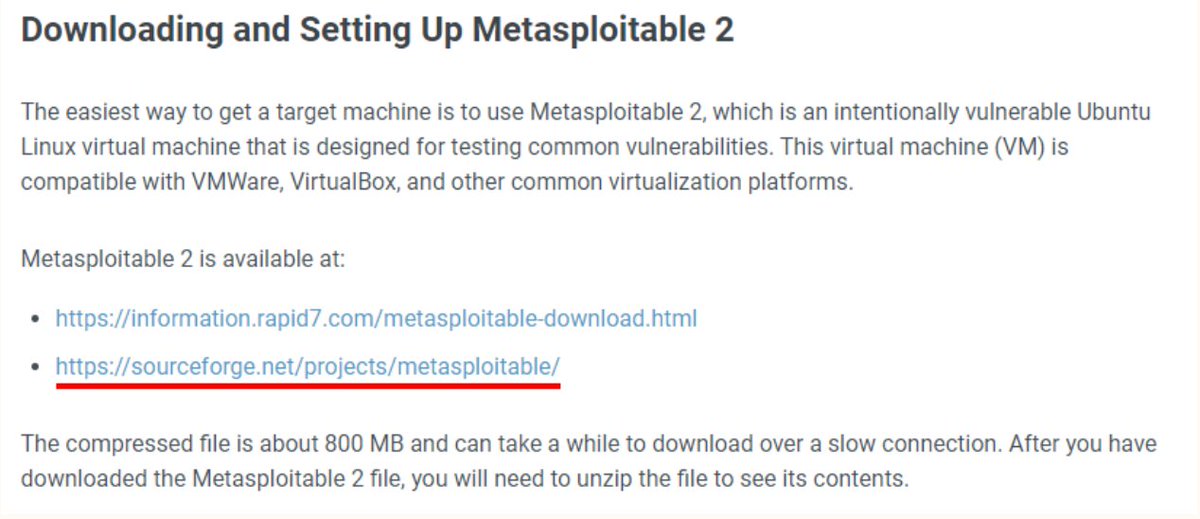
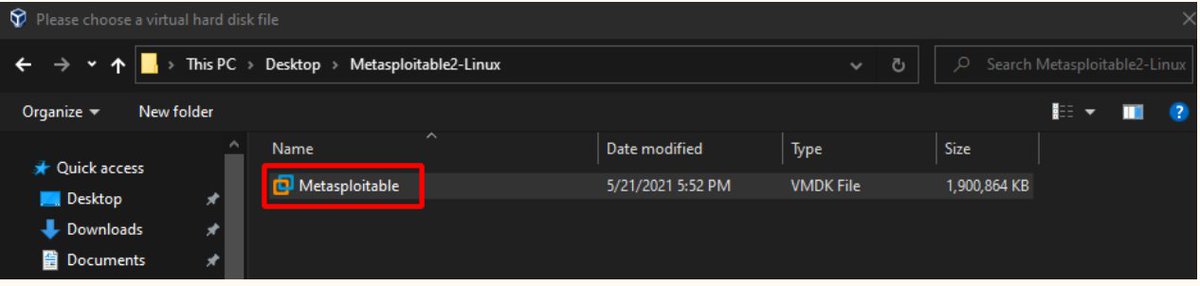
Step -3 Install Metasploitable 2 VM in VirtualBox
Metasploitable is a Ubuntu-based virtual machine
specially designed to contain vulnerabilities to help
ethical hackers and penetration testers safely
perform vulnerability tests for learning and research purposes.
Metasploitable is a Ubuntu-based virtual machine
specially designed to contain vulnerabilities to help
ethical hackers and penetration testers safely
perform vulnerability tests for learning and research purposes.
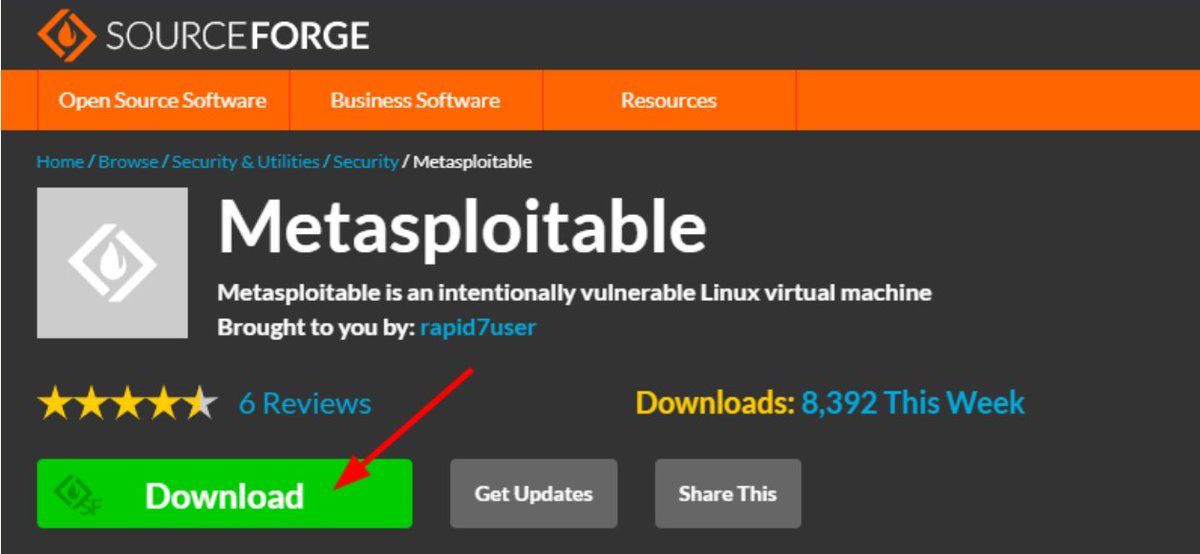
Step - 3 Download Metasploitable 2
Download Metasploitable 2 virtualbox image from here
docs.rapid7.com
Download Metasploitable 2 virtualbox image from here
docs.rapid7.com
If you managed to follow this virtual hacking lab tutorial
till the end.
You just made your first serious step in becoming a cybersecurity expert.
I’m proud of you!
till the end.
You just made your first serious step in becoming a cybersecurity expert.
I’m proud of you!
Launch Metasploitable 2 VM
On the Oracle VirtualBox Manager, select the Metasploitable 2 VM and click the Start button on top.
Login on Metasploitable 2 VM using the following credentials for both username and password:
msfadmin
msfadmin
On the Oracle VirtualBox Manager, select the Metasploitable 2 VM and click the Start button on top.
Login on Metasploitable 2 VM using the following credentials for both username and password:
msfadmin
msfadmin
Loading suggestions...