OMG LOL
someone tried to send me an email which spoofed....
MY OWN ADDRESS...
LULZ how stupid!
but also....
Let's take a look!
someone tried to send me an email which spoofed....
MY OWN ADDRESS...
LULZ how stupid!
but also....
Let's take a look!
#Sextortion #Cybercrime
Let's start by looking at the email they sent:
For starers no one writes:
Hi email address (LULZ) if they have intimate knowledge of you.
##############################
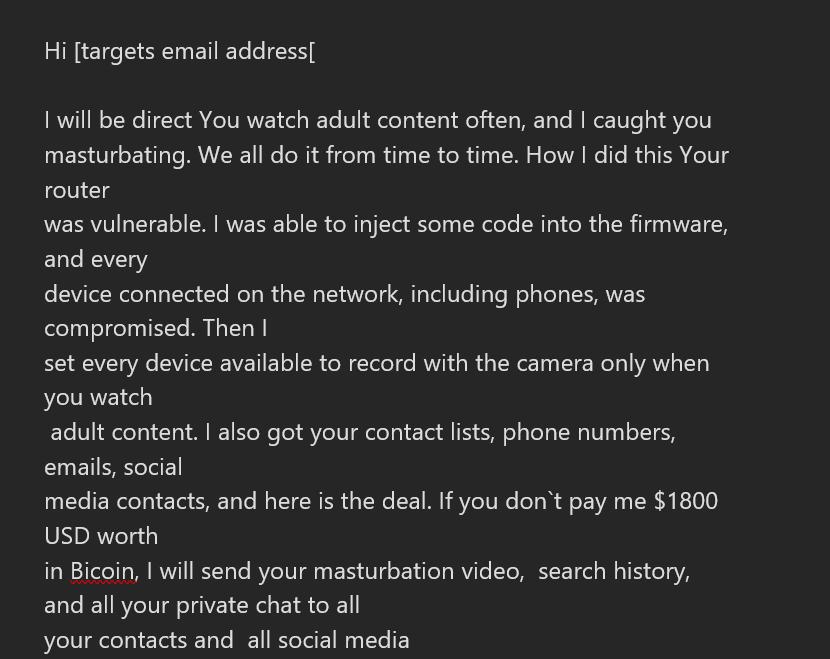
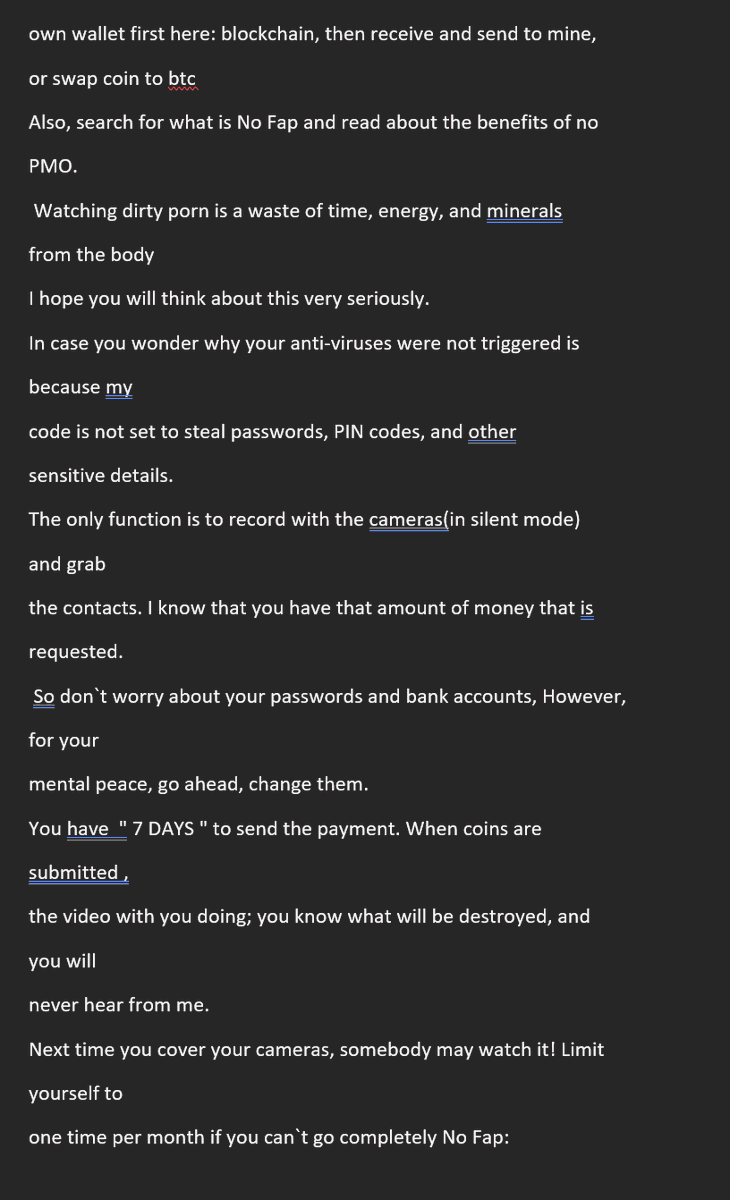
"I will be direct You watch adult content often, and I caught you
masturbating. We all do it from time to time. How I did this Your
router
was vulnerable. I was able to inject some code into the firmware,
and every
device connected on the network, including phones, was
compromised. Then I
set every device available to record with the camera only when
you watch
adult content. I also got your contact lists, phone numbers,
emails, social
media contacts, and here is the deal. If you don`t pay me $1800
USD worth
in Bicoin, I will send your masturbation video, search history,
and all your private chat to all
your contacts and all social media"
##############################
Let's start by looking at the email they sent:
For starers no one writes:
Hi email address (LULZ) if they have intimate knowledge of you.
##############################
"I will be direct You watch adult content often, and I caught you
masturbating. We all do it from time to time. How I did this Your
router
was vulnerable. I was able to inject some code into the firmware,
and every
device connected on the network, including phones, was
compromised. Then I
set every device available to record with the camera only when
you watch
adult content. I also got your contact lists, phone numbers,
emails, social
media contacts, and here is the deal. If you don`t pay me $1800
USD worth
in Bicoin, I will send your masturbation video, search history,
and all your private chat to all
your contacts and all social media"
##############################
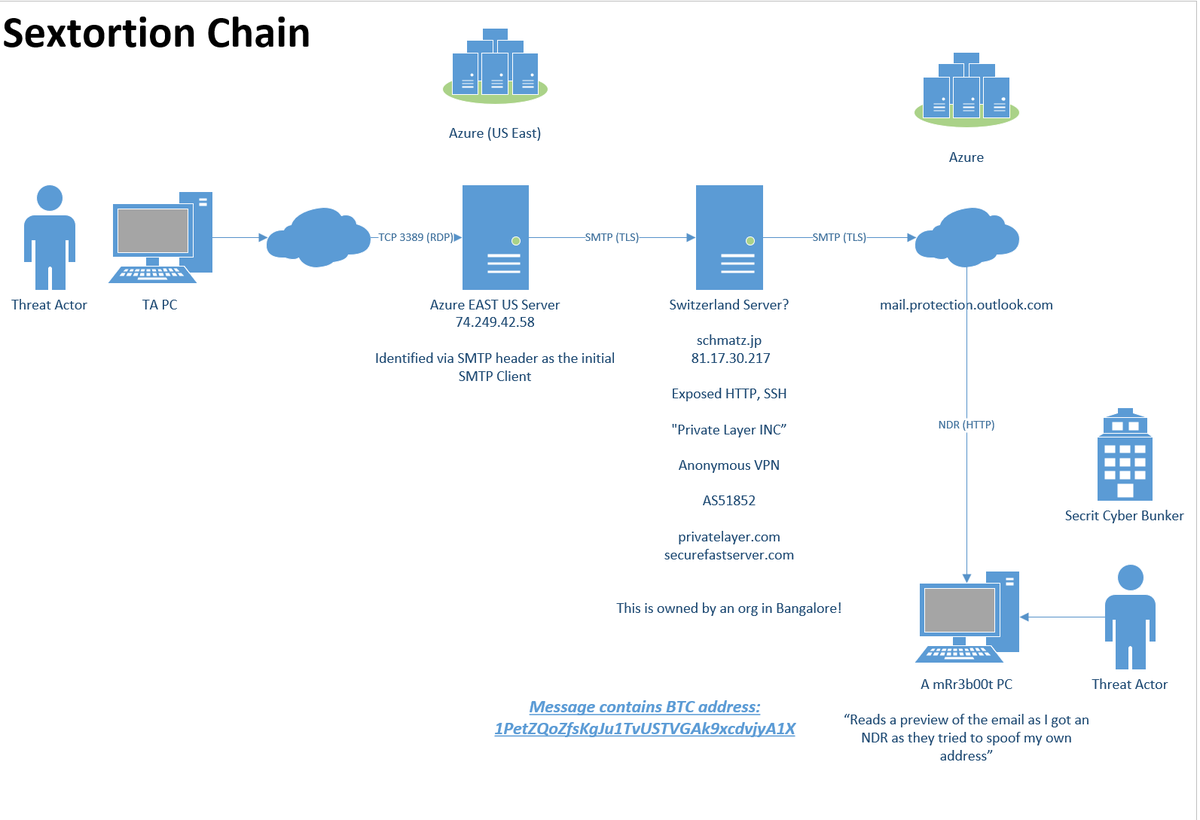
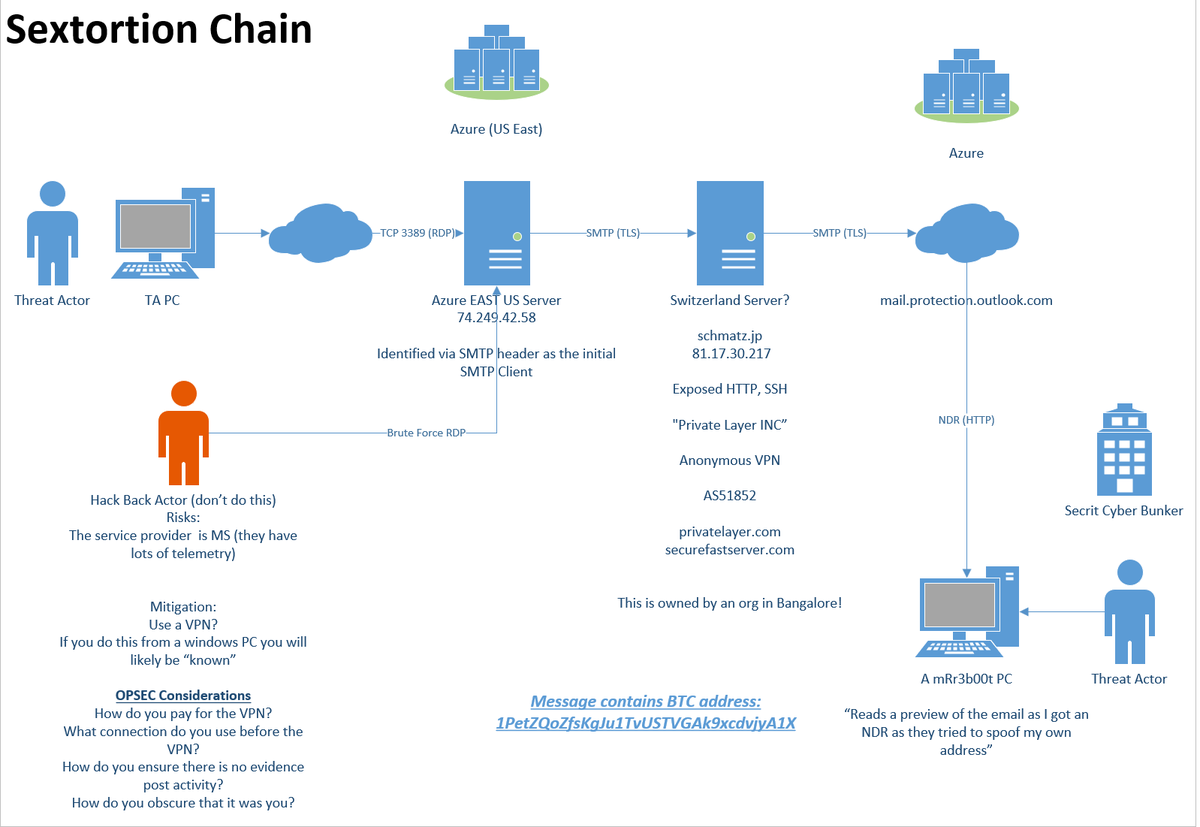
ok gang who wants to see an attempted #Sextortion scam kill chain?
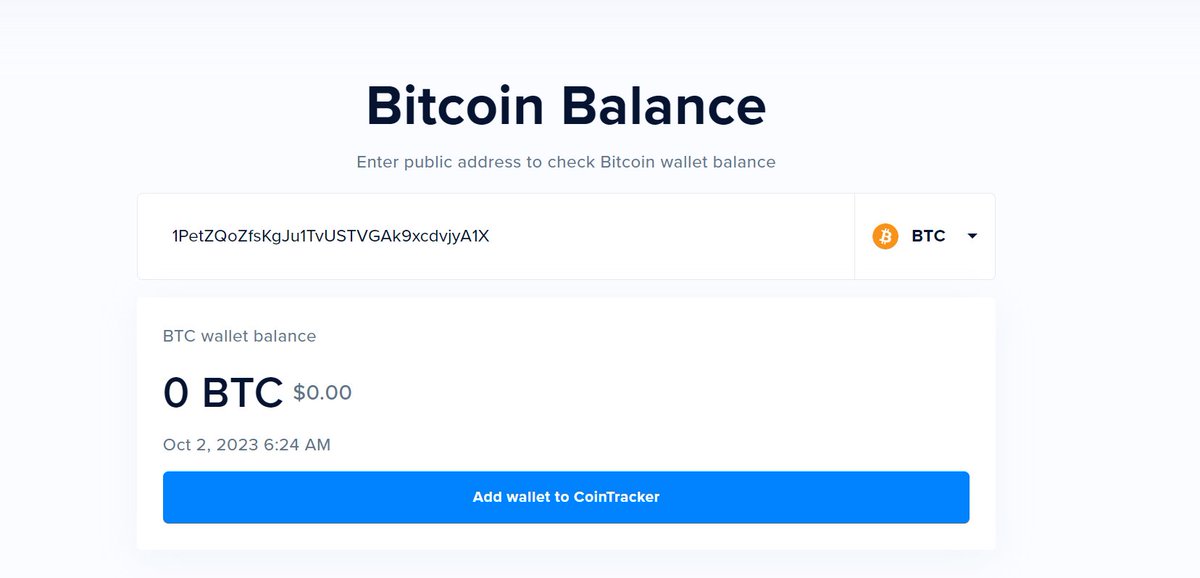
Here we see a threat actor use @Azure a VPN provider to try and "attack" me with a really badly worded email, trying to spoof my own address (LOL) and using a BTC wallet that so far as 0 Dollars in it!
Here we see a threat actor use @Azure a VPN provider to try and "attack" me with a really badly worded email, trying to spoof my own address (LOL) and using a BTC wallet that so far as 0 Dollars in it!
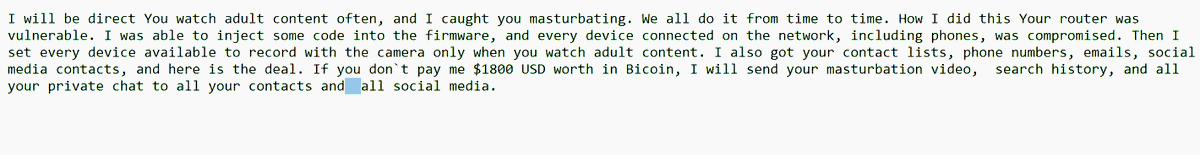
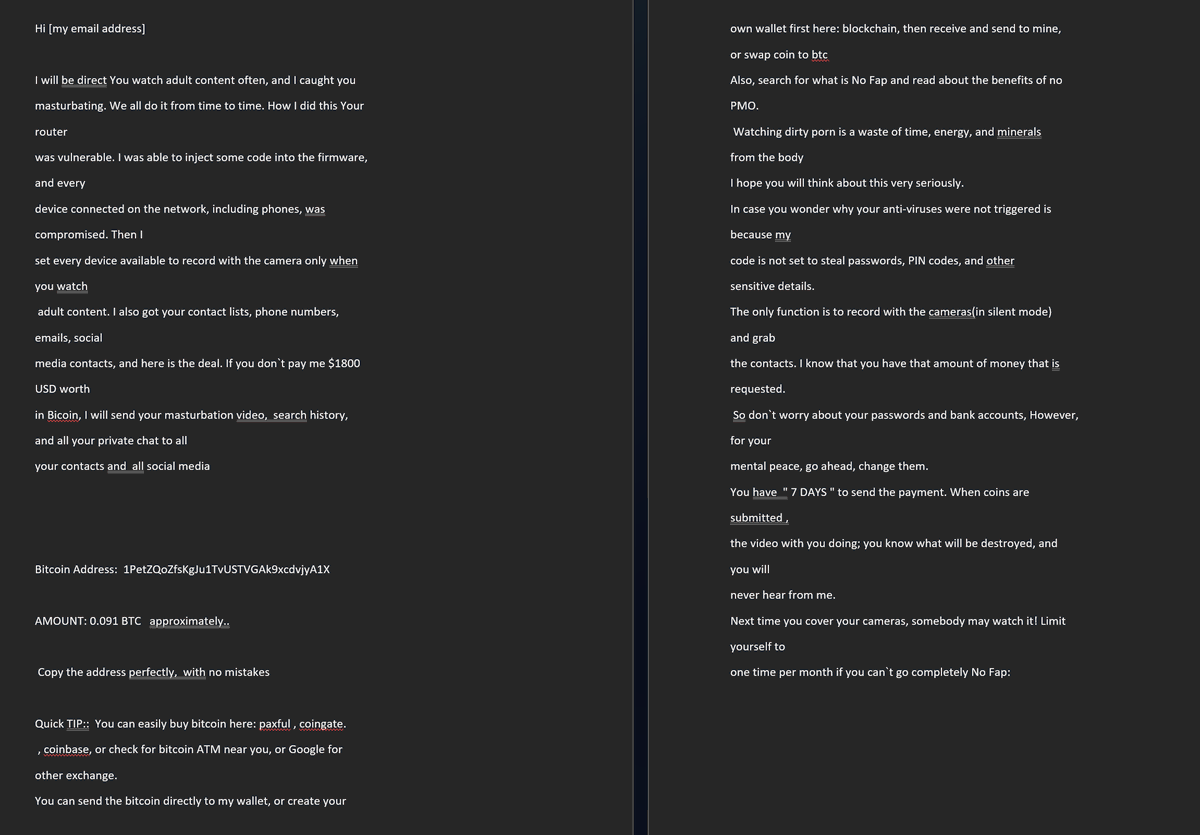
and here is the FULL text from the EMAIL body!
the language is terrible. The format is shockingly bad!
"Analyst suspects the writer is a non native English speaker." #lol
#Cybercrime #Sextortion #Crime #Microsoft #Azure
the language is terrible. The format is shockingly bad!
"Analyst suspects the writer is a non native English speaker." #lol
#Cybercrime #Sextortion #Crime #Microsoft #Azure
so what does this show us?
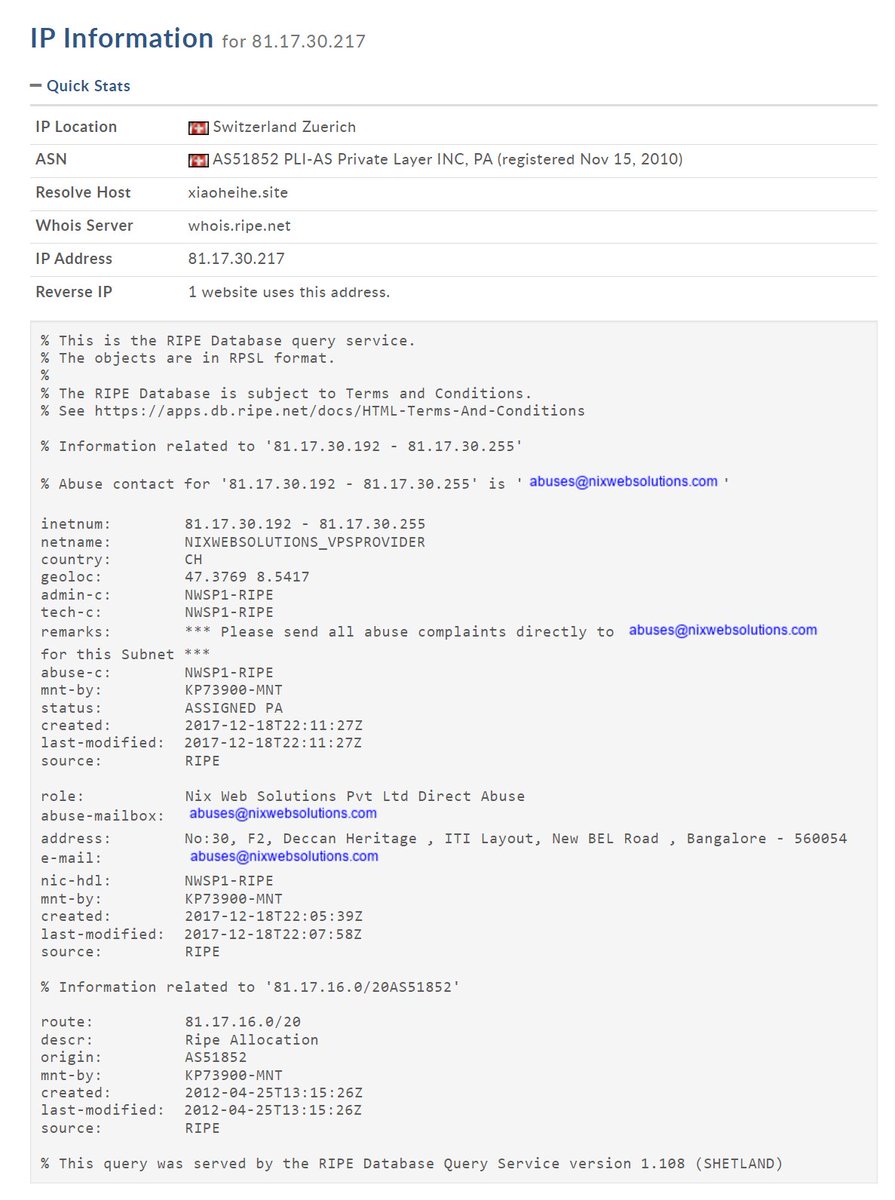
Well for starts the fact they used a VPN from azure did NOT hide their source IP! (at least up to the Azure point: @MsftSecIntel then would need to chase it back further)
It show's us this is primarly aimed at "personal" targets!
How do I conclude this?
The spoofing of the name part, doesn't work very well against business mail configurations!
Well for starts the fact they used a VPN from azure did NOT hide their source IP! (at least up to the Azure point: @MsftSecIntel then would need to chase it back further)
It show's us this is primarly aimed at "personal" targets!
How do I conclude this?
The spoofing of the name part, doesn't work very well against business mail configurations!
So tweeps what do we do?
we need to report it to @Azure @MsftSecIntel
to do this we can use this API or web form:
msrc.microsoft.com
(May I suggest there are additional catagories? this doesn't fit under Spam, this isn't phishing)
we need to report it to @Azure @MsftSecIntel
to do this we can use this API or web form:
msrc.microsoft.com
(May I suggest there are additional catagories? this doesn't fit under Spam, this isn't phishing)
Now theory time:
what if someone wanted to "HACK BACK!" what could someone do?
The first thing I'd say: what's the bloody point. You can spaf loads of packets at a server. You might not get in. The target is in Azure, they will get lots of data about that. The TA if they look at logs will see.
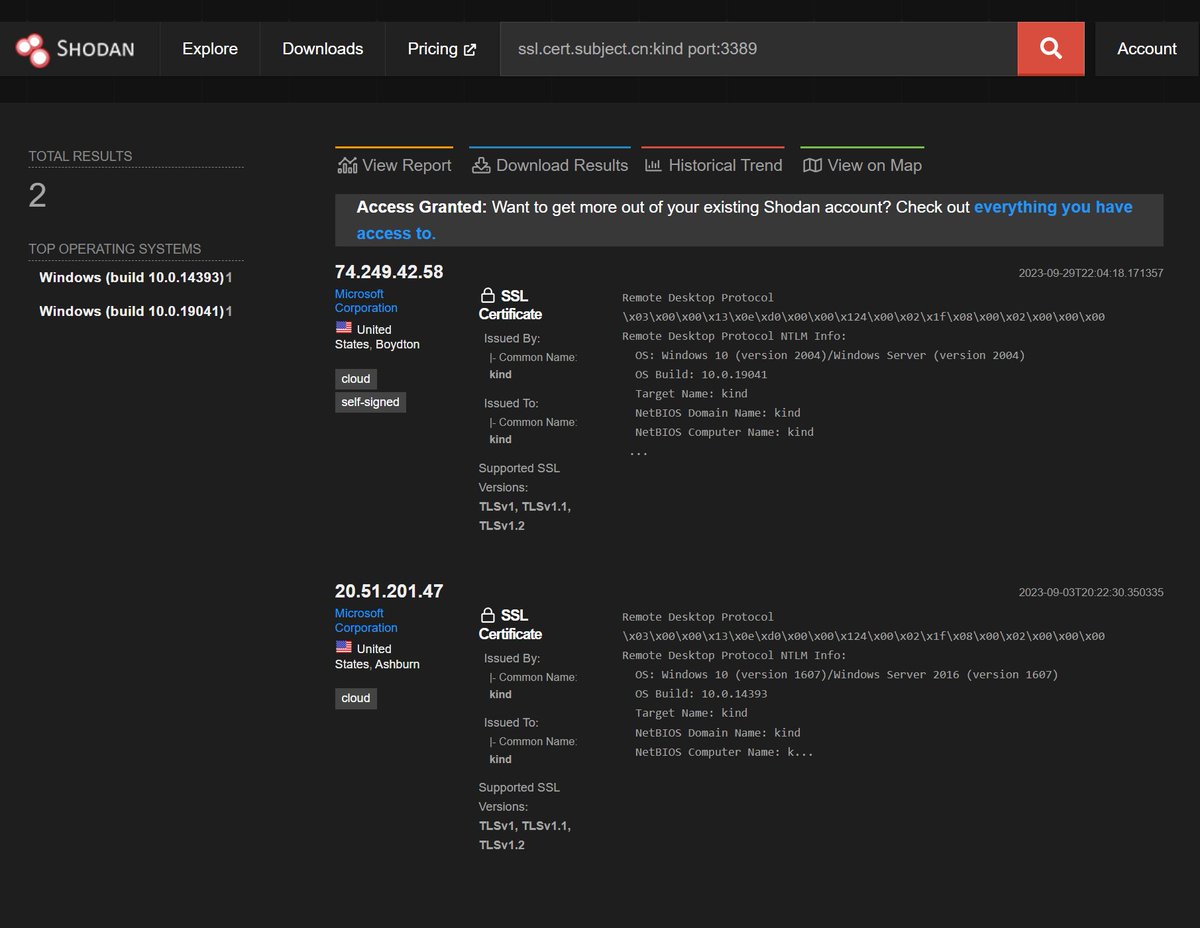
But anyway the theory would be likely to attack RDP. We have no real other vectors against the target.
Anyway that's a bit of theory. I am not taking this route. I am going to make a tea. the MS team should be knocking that server offline :) (taking down the TA is MUCH harder...)
what if someone wanted to "HACK BACK!" what could someone do?
The first thing I'd say: what's the bloody point. You can spaf loads of packets at a server. You might not get in. The target is in Azure, they will get lots of data about that. The TA if they look at logs will see.
But anyway the theory would be likely to attack RDP. We have no real other vectors against the target.
Anyway that's a bit of theory. I am not taking this route. I am going to make a tea. the MS team should be knocking that server offline :) (taking down the TA is MUCH harder...)
Hopefully that was educational and fun for people!
These scammers are wankers. Sometimes this stuff works.
Be safe, be legal. Use the @MsftSecIntel abuse API / Forms. Also use the @NCSC reporting services!
🫡🤙🇬🇧❤️ #DefendAsOne
These scammers are wankers. Sometimes this stuff works.
Be safe, be legal. Use the @MsftSecIntel abuse API / Forms. Also use the @NCSC reporting services!
🫡🤙🇬🇧❤️ #DefendAsOne
@MsftSecIntel @NCSC And here is a dose of cyber reality:
Abuse report rejected. No action taken.
@MsftSecIntel 😭😭😭😭😭😭😭
@therealshodan booo!
Abuse report rejected. No action taken.
@MsftSecIntel 😭😭😭😭😭😭😭
@therealshodan booo!
@MsftSecIntel @NCSC @therealshodan The reality of this stuff is:
Corporate cyber defence:
Identify
Protect
Detect
Respond is easier (not easy) than
Prevent and Pursue (cyber crime fighting)
The webs are vast,
Cross border and difficult methinks
Corporate cyber defence:
Identify
Protect
Detect
Respond is easier (not easy) than
Prevent and Pursue (cyber crime fighting)
The webs are vast,
Cross border and difficult methinks
Loading suggestions...