Again, only a little information to go off of, but a lack of information can also work in our favor regarding search queries.
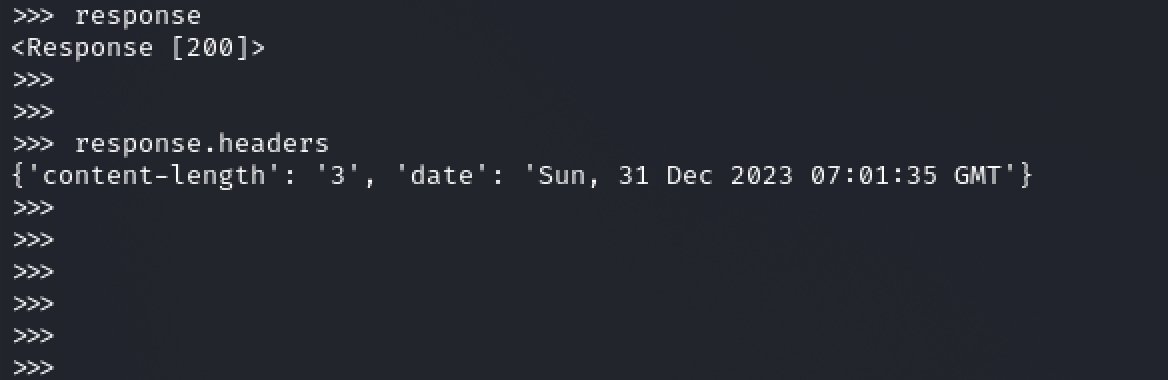
There is no header for the Server, Content-Type, etc.
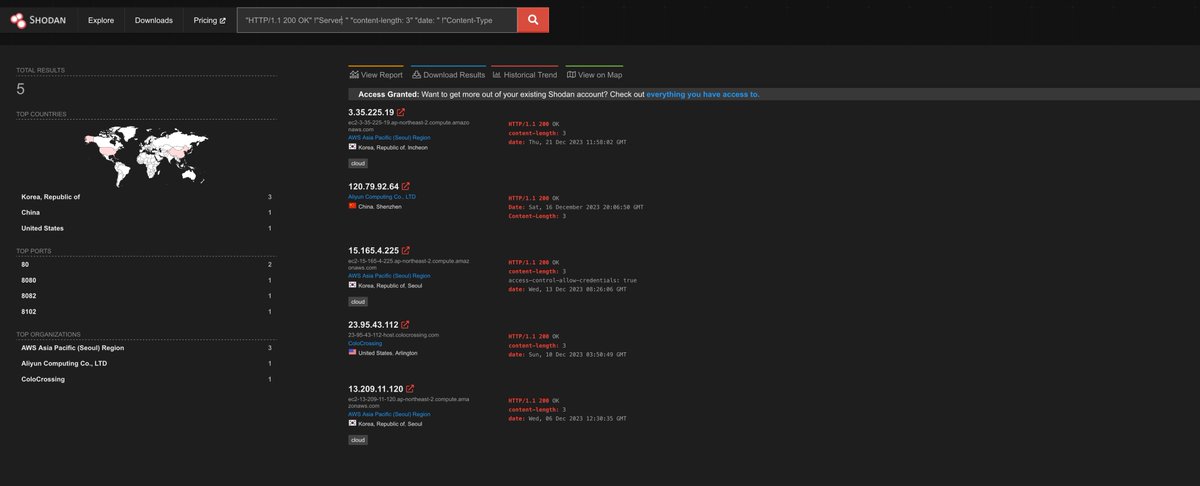
We now have a rough query for an HTTP 200 response with two lowercase headers.
There is no header for the Server, Content-Type, etc.
We now have a rough query for an HTTP 200 response with two lowercase headers.
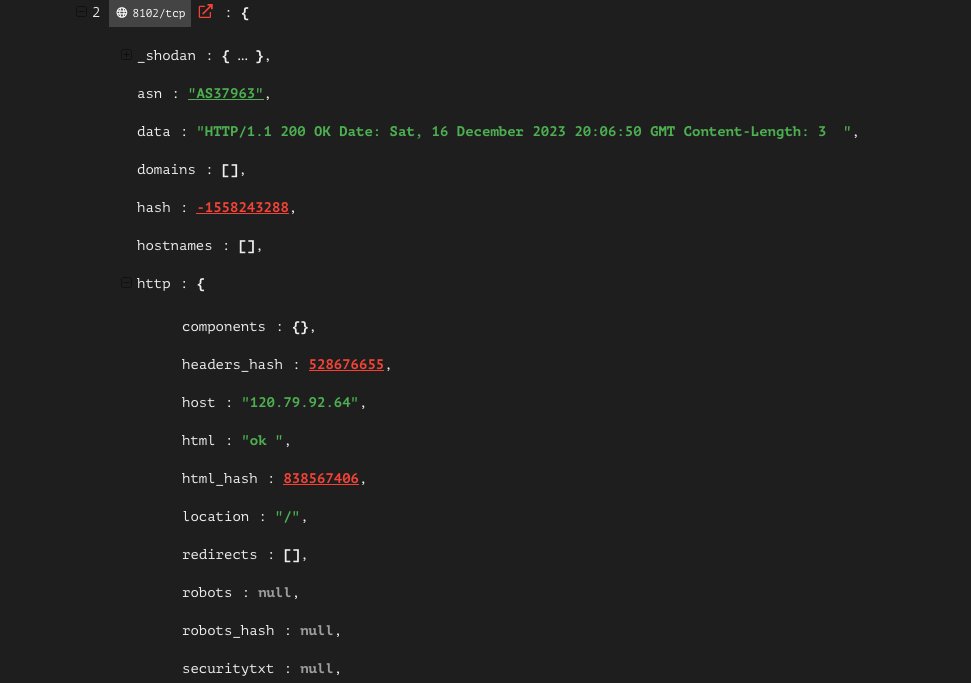
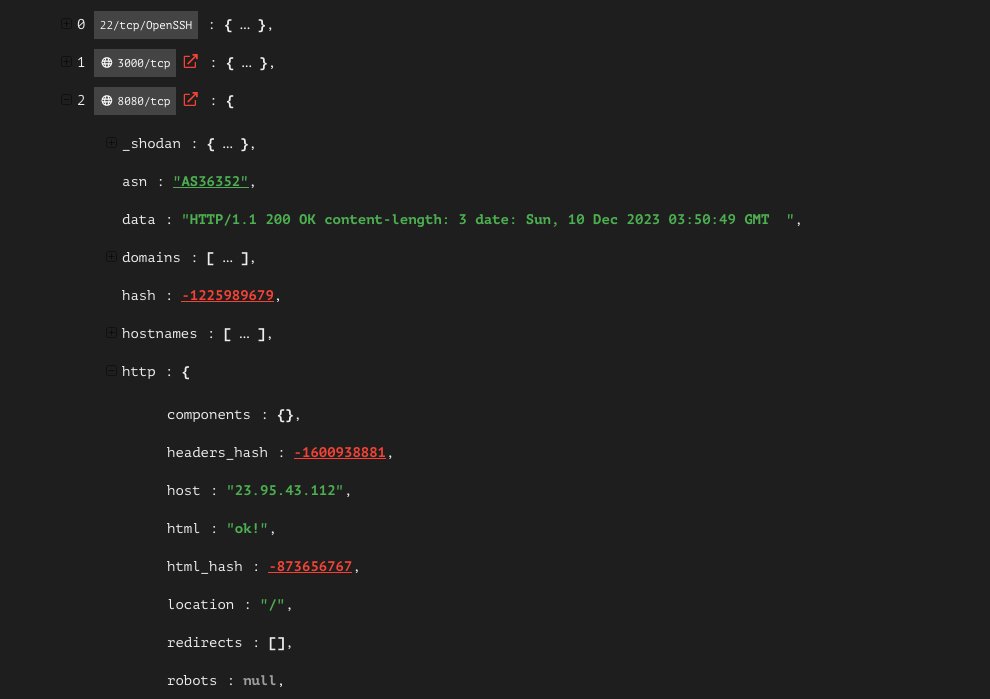
Additional analysis is needed to confirm these are link servers, but I can say with moderate confidence what we are looking at is part of link's framework.
Next time, I'll cover something a bit more advanced, maybe a Python script to emulate communication with a C2 framework to assist in identifying new hosts.
Shout out to @embee_research for the tips and motivation to start sharing more.
Shout out to @embee_research for the tips and motivation to start sharing more.
Loading suggestions...