1/ An investigation into the alleged $11.1M @PrismaFi exploiter 0x77 (Trung) and the multiple other exploits they are connected to.
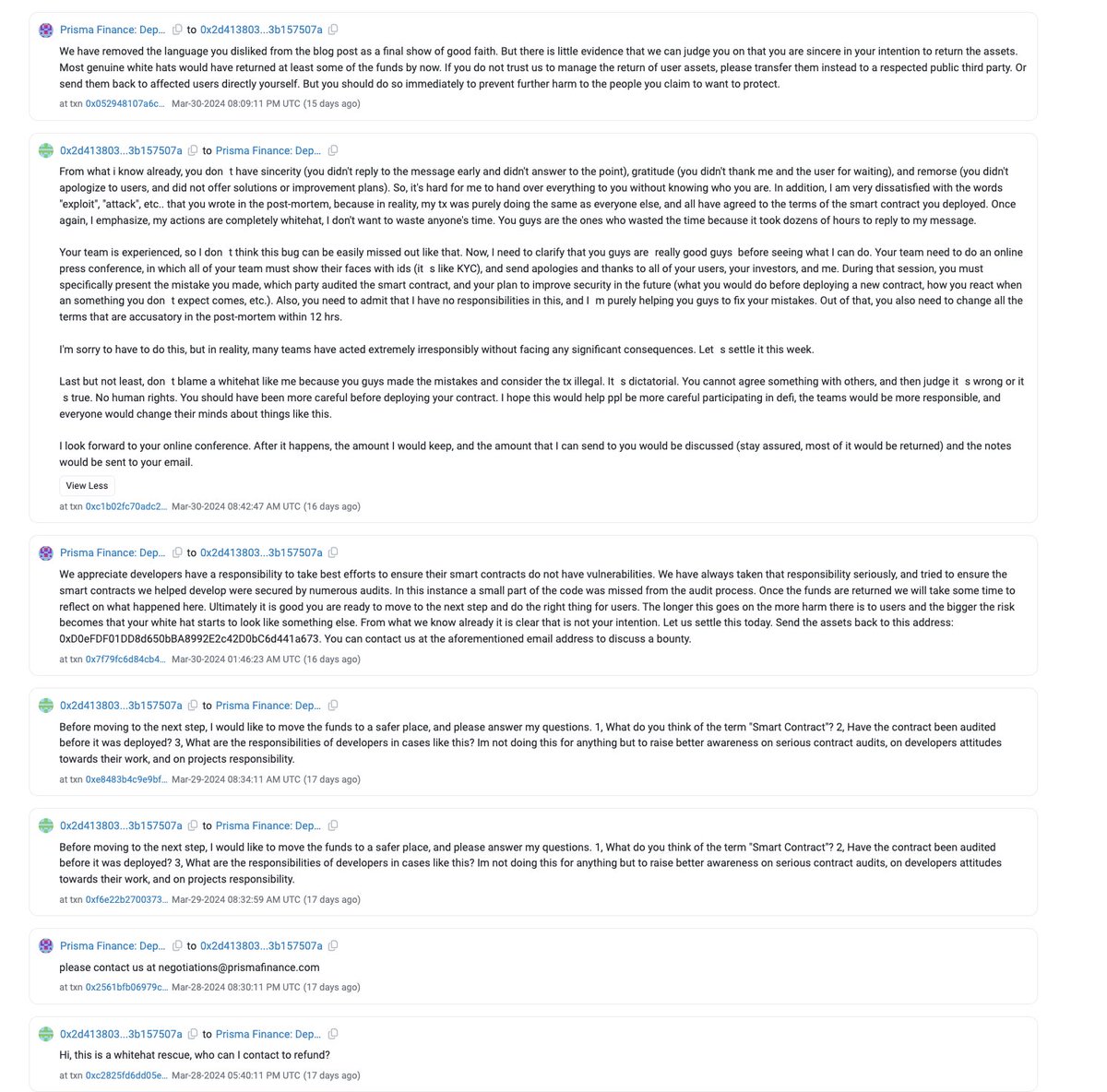
3/ At first the attacker communicated with the Prisma deployer the attack was whitehat.
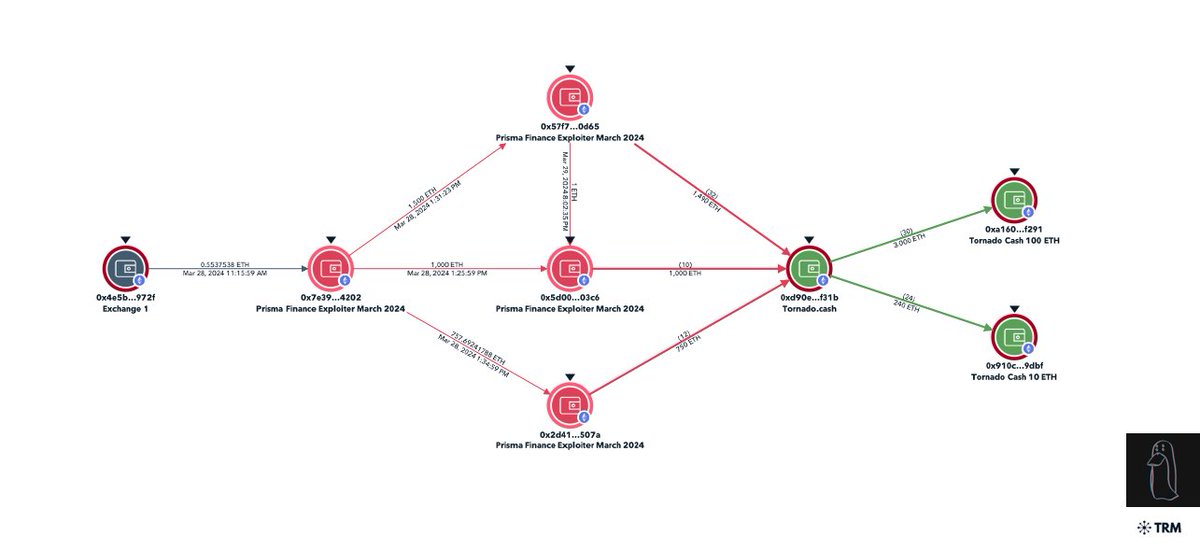
Later that day all of the funds were deposited to Tornado Cash contradicting that statement.
The exploiter began making outrageous demands and asked for a $3.8M (34%) whitehat bounty
This amount is significantly higher than the industry standard 10% essentially extorting the team as the treasury does not have sufficient assets to reimburse users.
Later that day all of the funds were deposited to Tornado Cash contradicting that statement.
The exploiter began making outrageous demands and asked for a $3.8M (34%) whitehat bounty
This amount is significantly higher than the industry standard 10% essentially extorting the team as the treasury does not have sufficient assets to reimburse users.
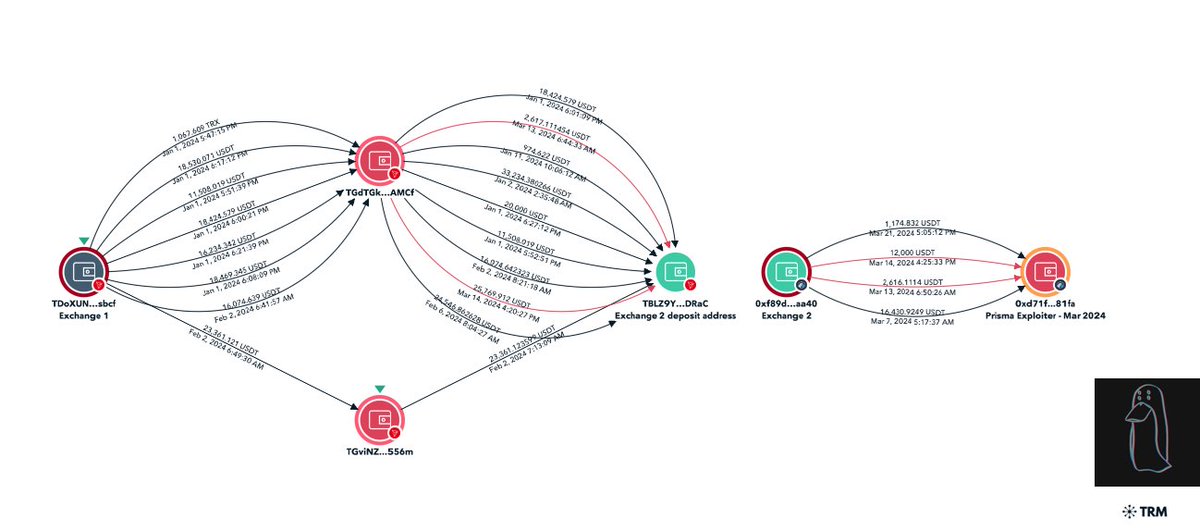
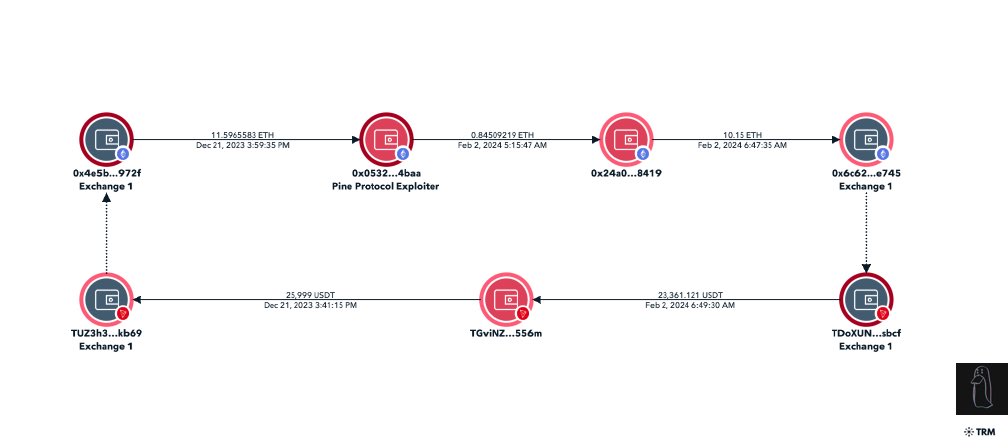
4/ On-chain the exploiters address was funded via FixedFloat.
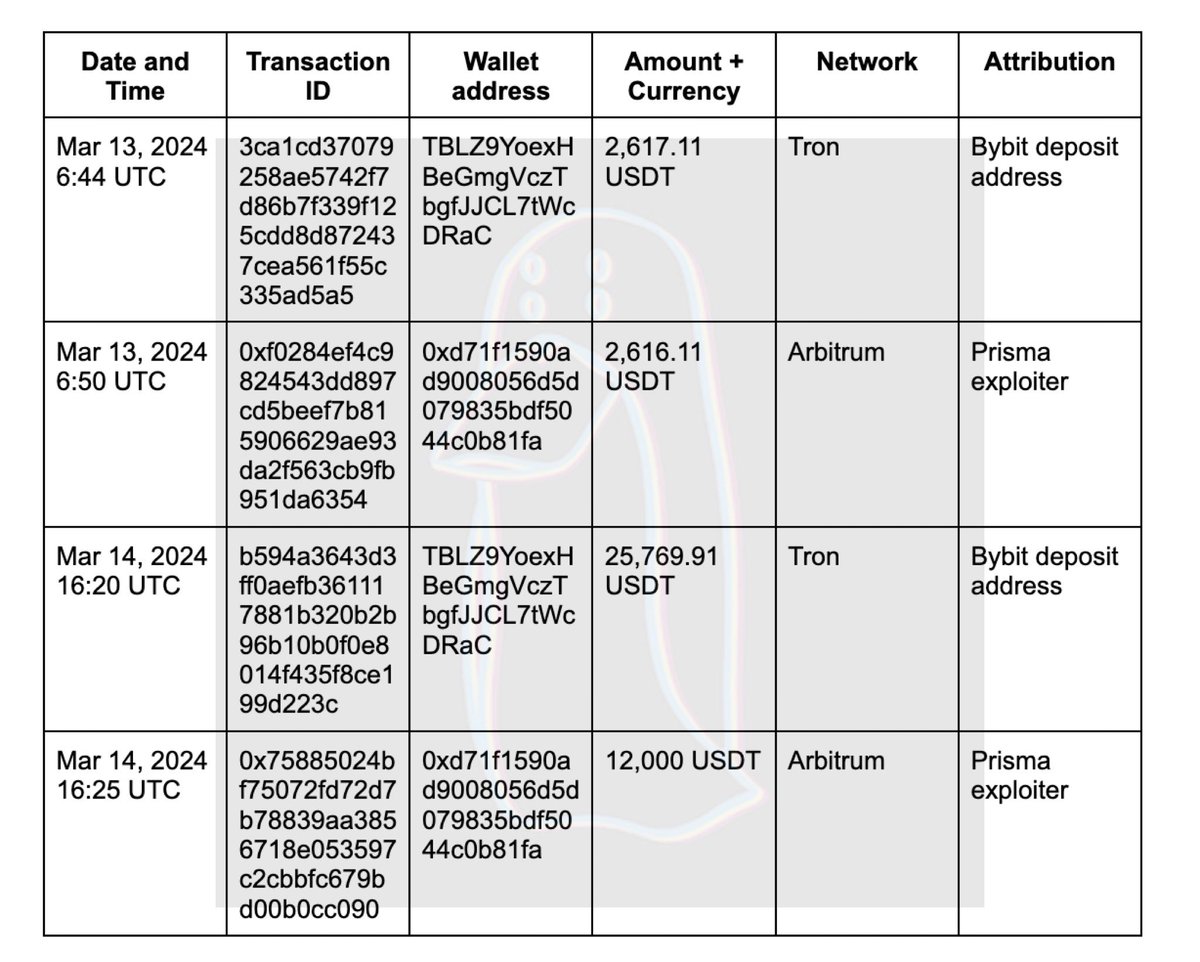
Using timing analysis the source address was then located on Arbitrum.
0xd71f1590ad9008056d5d079835bdf5044c0b81fa
2000 USDT source transaction at 11:13 am UTC
0x93b047e530249592e50bde889c31f5346096ad2ae59073dec15abd39d05e3b20
0.553 ETH ($1.95K) received by Prisma exploiter at 11:15 am UTC
0xe55bd15d2bd17c0a97356f612480887df91bc483f6affae8edd06a6d08b60f53
Using timing analysis the source address was then located on Arbitrum.
0xd71f1590ad9008056d5d079835bdf5044c0b81fa
2000 USDT source transaction at 11:13 am UTC
0x93b047e530249592e50bde889c31f5346096ad2ae59073dec15abd39d05e3b20
0.553 ETH ($1.95K) received by Prisma exploiter at 11:15 am UTC
0xe55bd15d2bd17c0a97356f612480887df91bc483f6affae8edd06a6d08b60f53
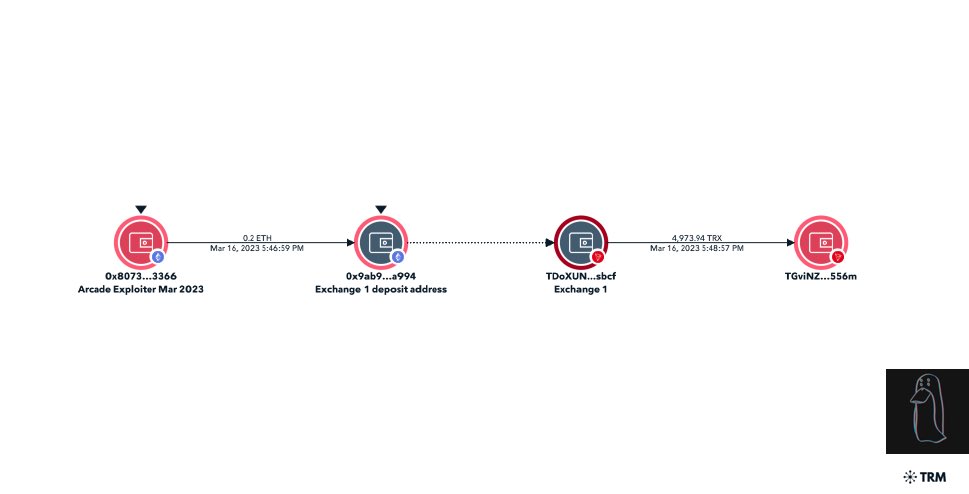
6/ I found TGviNZ funded by the Arcade_xyz exploit from March 2023 where the exploiter requested additional funds from the protocol.
Arcade exploiter
0x807350917efa87fb15ed7eb0952635cdf1c13366
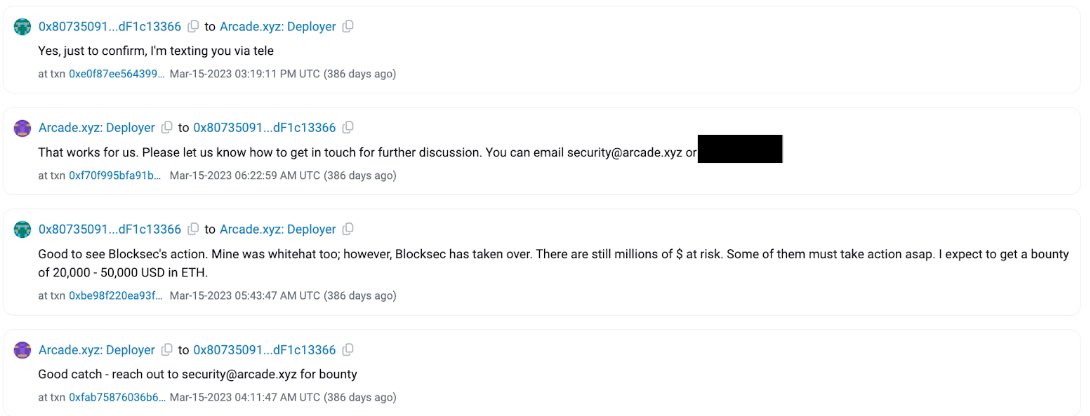
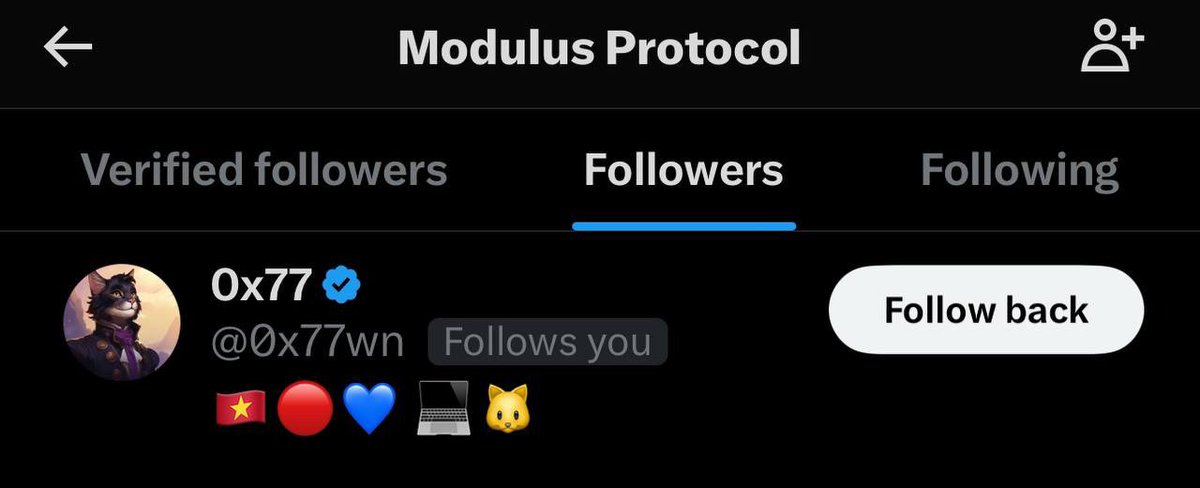
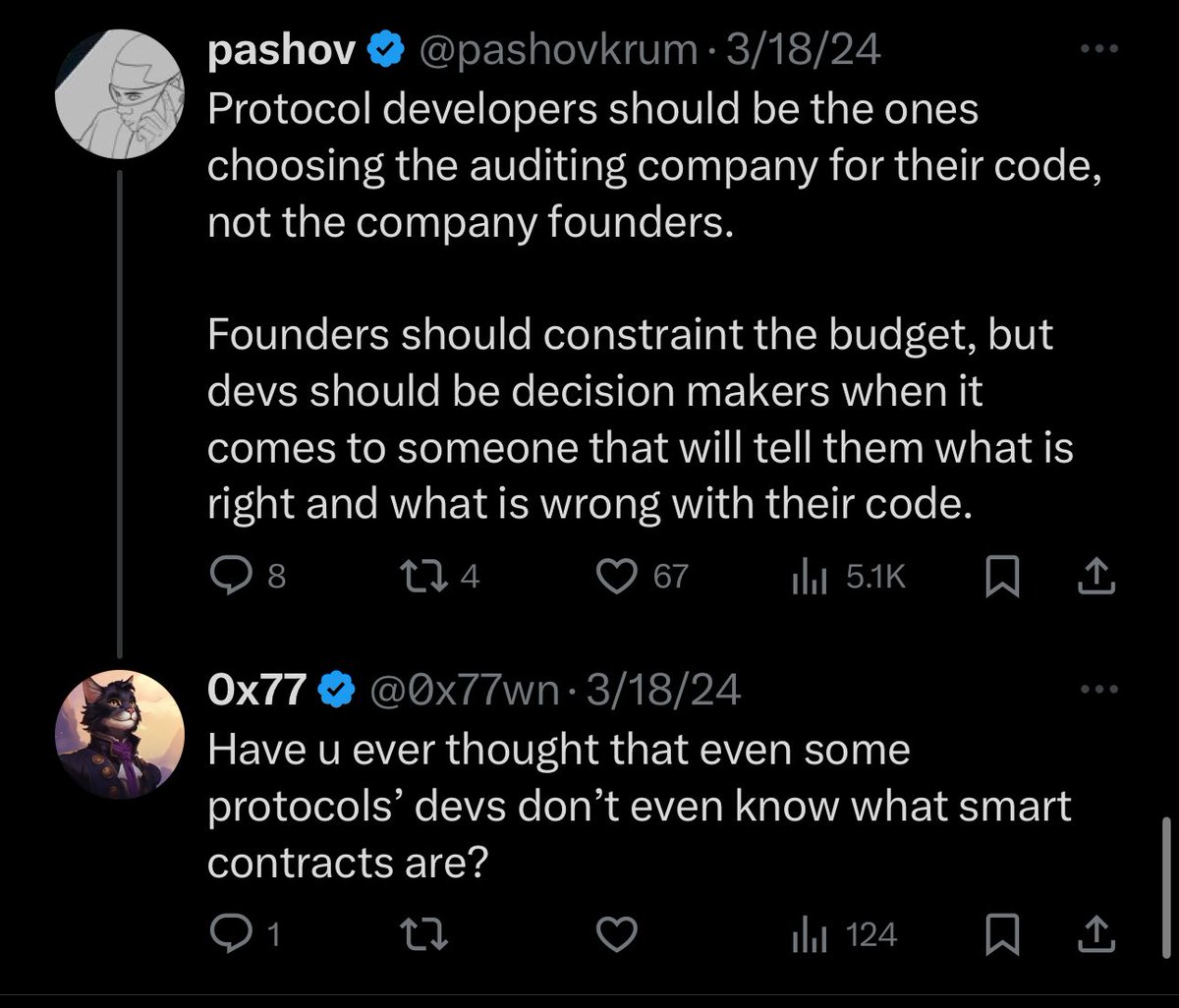
Further investigation revealed the team had been in contact with the exploiter who was using the alias ‘0x77’ on Telegram with the account still active.
Arcade exploiter
0x807350917efa87fb15ed7eb0952635cdf1c13366
Further investigation revealed the team had been in contact with the exploiter who was using the alias ‘0x77’ on Telegram with the account still active.
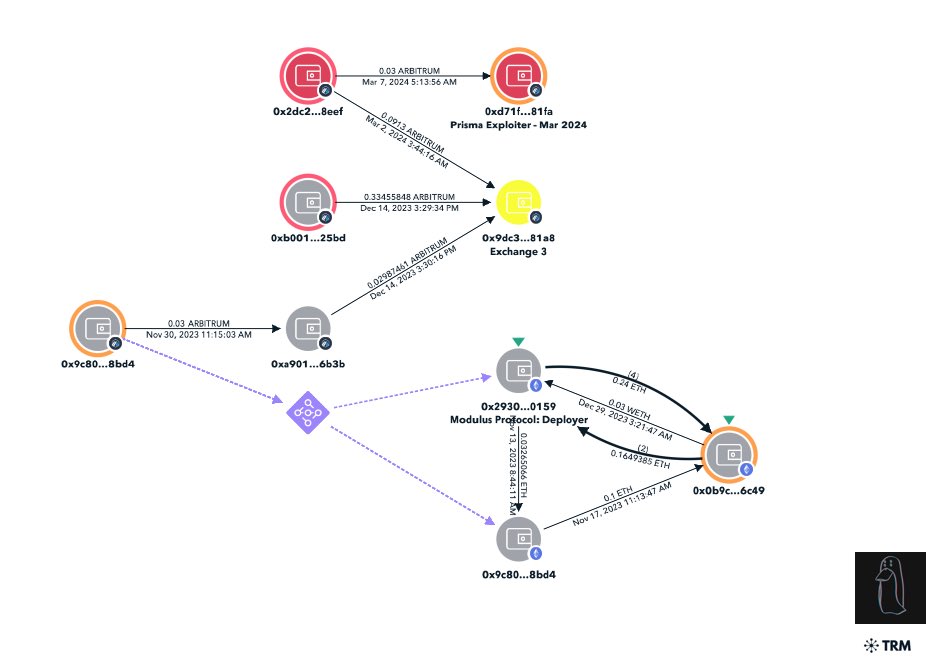
8/ I then discovered the exploiter’s address connected to the deployer of @modulusprotocol
0x77 was one of the few followers of the project strengthening the connection between each incident.
Deployer address
0x29300e694a77d913248d1761d7e4f2d81c350159
0x77 was one of the few followers of the project strengthening the connection between each incident.
Deployer address
0x29300e694a77d913248d1761d7e4f2d81c350159
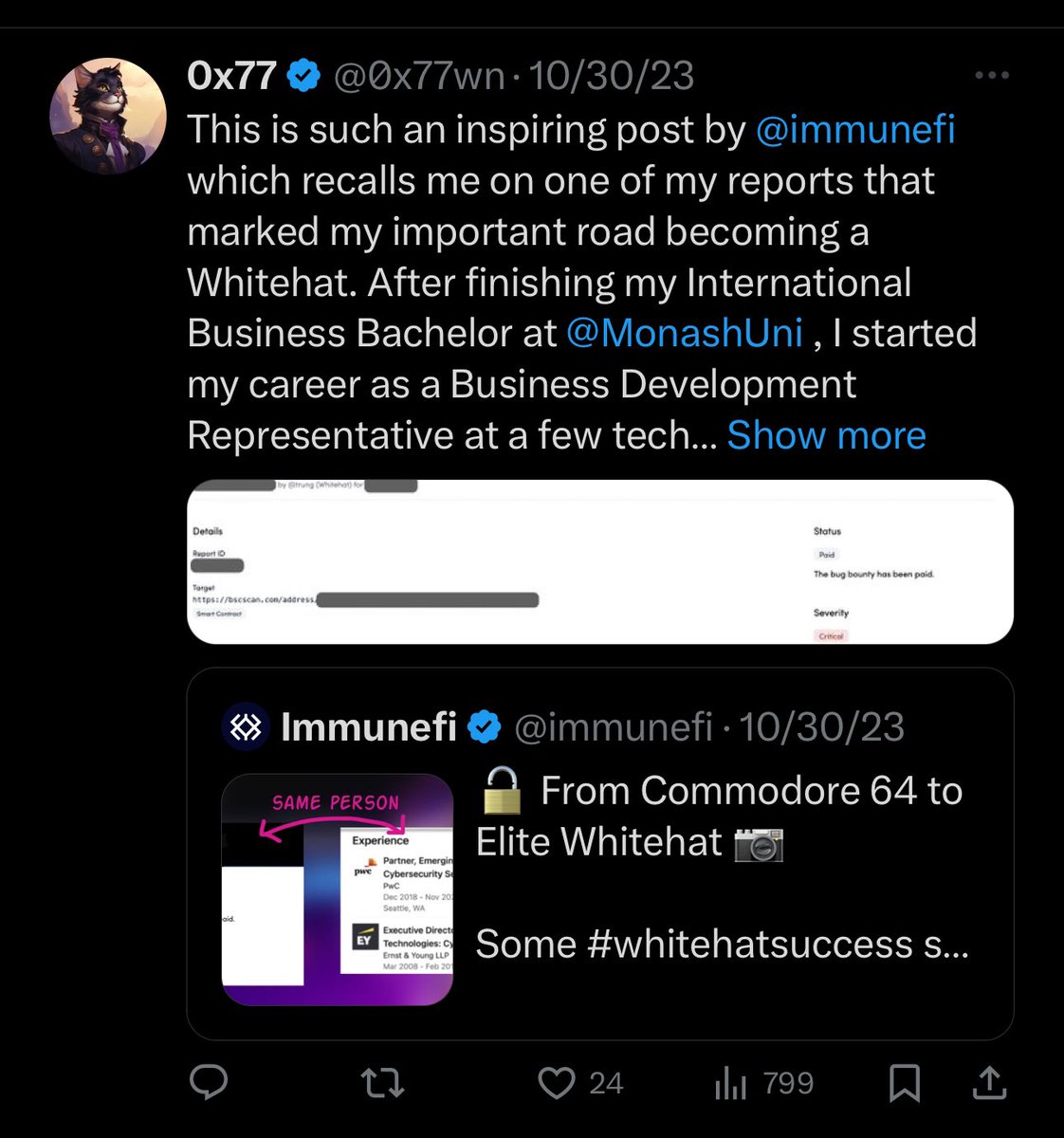
9/ Further analysis was conducted with the phone number, emails, and other details of the alleged exploiter.
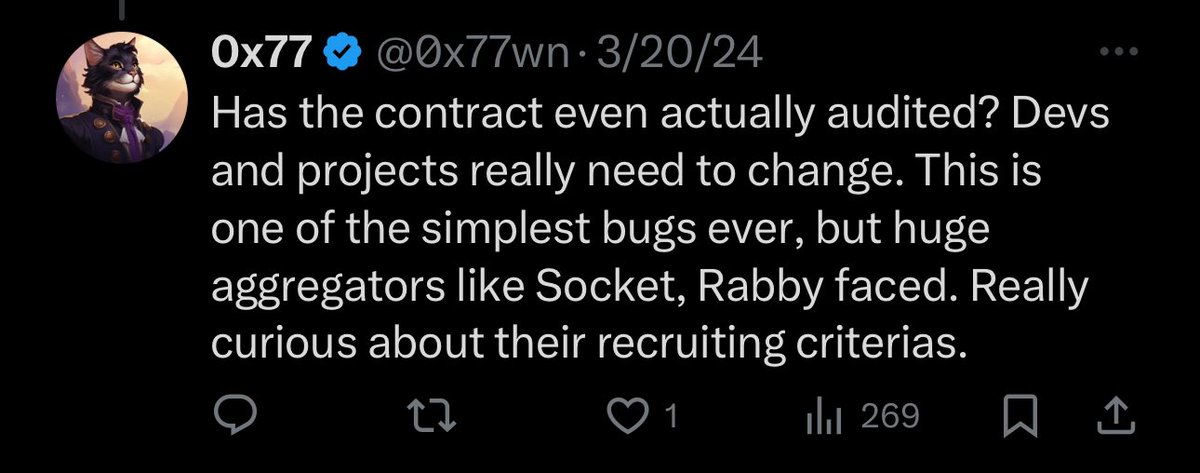
From their posts on X it is clear they have a strong technical background.
As of now all personal details have been compiled and the Prisma team is pursuing every possible legal avenue in Vietnam and Australia.
I urge the exploiter to return the funds and save everyone time before this gets much worse for them.
From their posts on X it is clear they have a strong technical background.
As of now all personal details have been compiled and the Prisma team is pursuing every possible legal avenue in Vietnam and Australia.
I urge the exploiter to return the funds and save everyone time before this gets much worse for them.
Loading suggestions...