cybersecurity
1012 Threads

since most people don’t know (or don’t remember) the hacker group anonymous, here’s a thread because they’re a pretty big fucking deal 😭 https://t.co/llZEODLPcq
Burp Suite is a tool for testing the web applications security. It supports the analysis of an application's attack surface, finds the security vulnerabilities, and exploits the fi...
24/50 Russian military intelligence penetrated the Democratic National Committee in March 2016 as well as personal accounts of leading Democrats. Stolen emails were then used to...
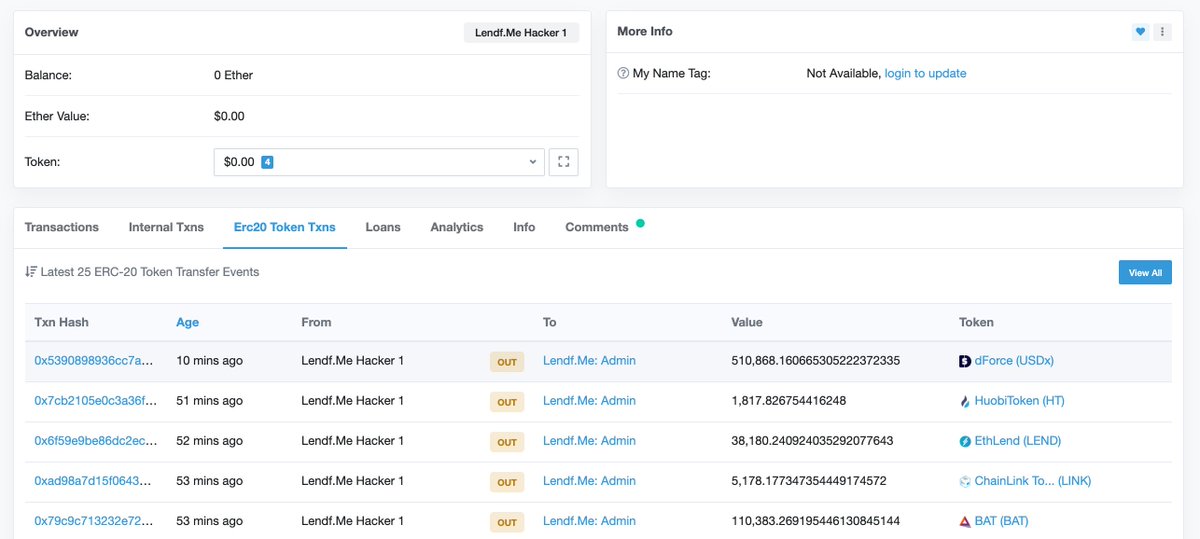
This is insane. The lendf/dForce hacker is in the process of returning all the hacked funds to the admin: $10M of ETH $6.6M of USDT $2.2M of HBTC $750K of USDC $381K of HUSD $137...
Transparency is fundamental to the work we do at Twitter. Today, we’re updating our archive of state-backed information operations with some recent account networks we’ve removed f...
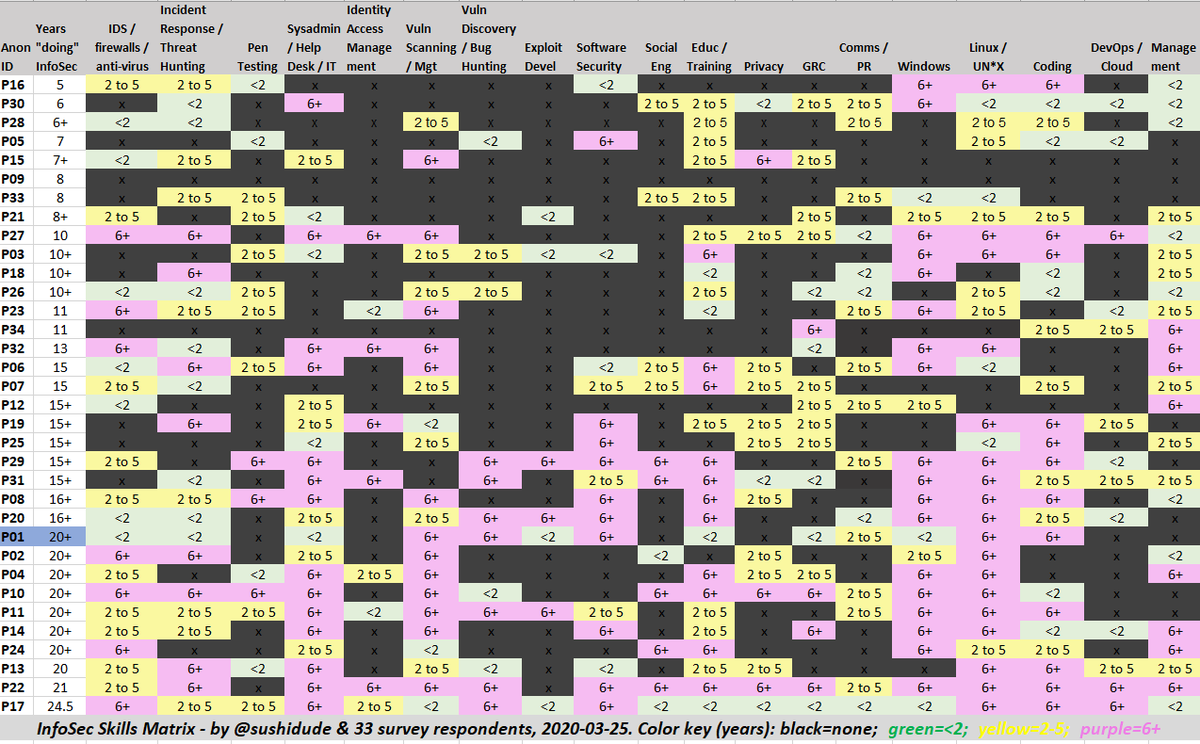
Hey InfoSec newbies and students: you don't have to know everything! Here's a matrix of 34 anonymized respondents with 5+ years' experience, across 19 skills (I'm P01). Black cells...

⚠️ WARNING! All versions of #Microsoft Windows (7, 8.1, 10, Server 2008, 2012, 2016, 2019) operating systems contain 2 new font parsing library RCE vulnerabilities that are: —CRI...

1/ Nth Room refers to a mass digital sex abuse that's happening in South Korea using a messenger app, Telegram. Telegram is known for its cyber security and encoding all contents o...
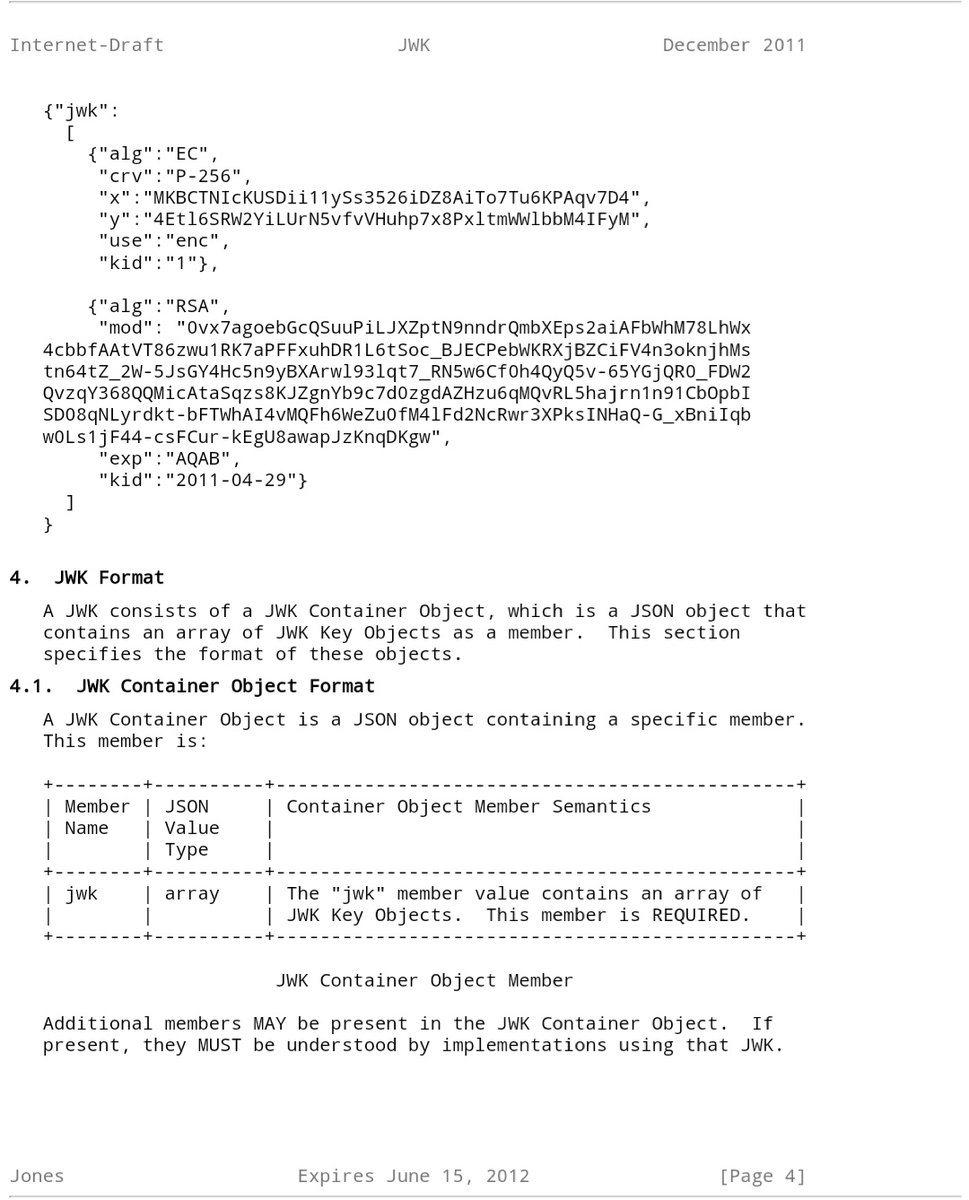
#Encryption is the process of transformation data in plain text and making it unreadable to all except those who are meant to read the data, with the goal of confidentiality. Singi...

NEW: Facebook has removed more than 1,700 assets linked to two Egyptian digital marketing firms targeting audiences in Middle East and North Africa. Here's our EXCLUSIVE look at th...

Your WhatsApp groups may not be as secure as you think they are. The "Invite to Group via Link" feature allows groups to be indexed by Google and they are generally available acro...
So bZx just got flash attacked *again*, just after they announced the postmortem on the previous one. Unlike that attack, this one was pure oracle manipulation—didn't even require...

1/ We are pushing hard to meet the three criteria for the #Elrondmainnet launch. Most important focus has been on getting things ready for an in-depth security and economics aud...
Here’s how you get panic-full logs: Download the exploit project on your mac: https://t.co/hIvIC7ejXs 1)Open the downloded project in xcode 2)Go to parameters.c and change line...
1/ A thread on vehicle hacking The field really started in 2010 by @supersat, @stevecheckoway et al when they practically demonstrated CAN message injection and ECU firmware refla...
@jp_koning @GenMeasures There are three ways of approaching this. 1) Whoever filled the hacker's order on Bitfinex, they are now in possession of stolen BTC. Even if when they wit...

Web Cache Deception attacks still impact websites with 'substantial user populations' - academics tested 340 of the Alexa Top 5k sites - found that 25 websites are still vulnerabl...

Vamos a usar este tweet para publicar #Dorks de todo tipo, empecemos con este: inurl:wp-config.php intext:DB_PASSWORD -stackoverflow -wpbeginner -foro -forum -topic -blog -about...
alert(123); alert("XSS"); alert(123) alert("hellox worldss"); alert(“XSS”) alert(“XSS”); alert(‘XSS’) “>alert(“XSS”)
![[PoC List] Zero-Day Usage By Country
#Fireeye
1. CVE-2012-4681
https://t.co/q8RzawOJXg
2. CVE-201...](https://pbs.twimg.com/media/EKv7LNCVUAM2OsH.jpg)
[PoC List] Zero-Day Usage By Country #Fireeye 1. CVE-2012-4681 https://t.co/q8RzawOJXg 2. CVE-2012-4792 https://t.co/IdAkgMf45l 3. CVE-2013-0422 https://t.co/Nbn034eY0K https:/...
Academic definitions - Terrorism is : An attempt to communicate messages through the use of orchestrated violence.
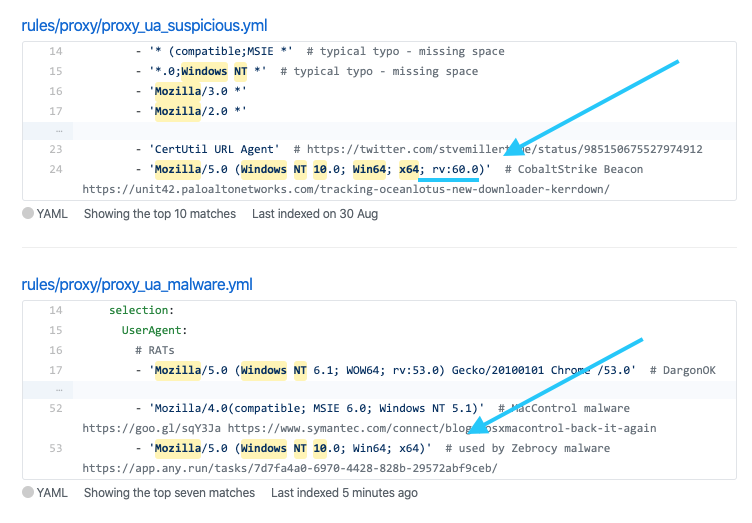
Yes, an old #Sigma rule that detect Office programs spawning processes in user folders would have detected #APT28's recent campaign agains Kazakhstan Tweet by @MeltX0R https://t.c...

(1/6) Email Search Thread 1. https://t.co/milcUI45cJ — check in leaked databases 2. https://t.co/NAzZ2PH9ko — find websites where account has been registered by email 3. https://t....
The Linux Forensics workshop (labs, slides, forensic images "E01")+talk done at #OSDFCon 2019, is now available here: https://t.co/7aeHMNaVQI #DFIR #Linux #Forensics