cybersecurity
1012 Threads

My team recently converted our entire detection library to #SIGMA and created a wiki around it! We are an MSSP & platform agnostic, meaning we have a version of a rule for pretty...
Cybersecurity Certifications to get in 2023 (For FREE)
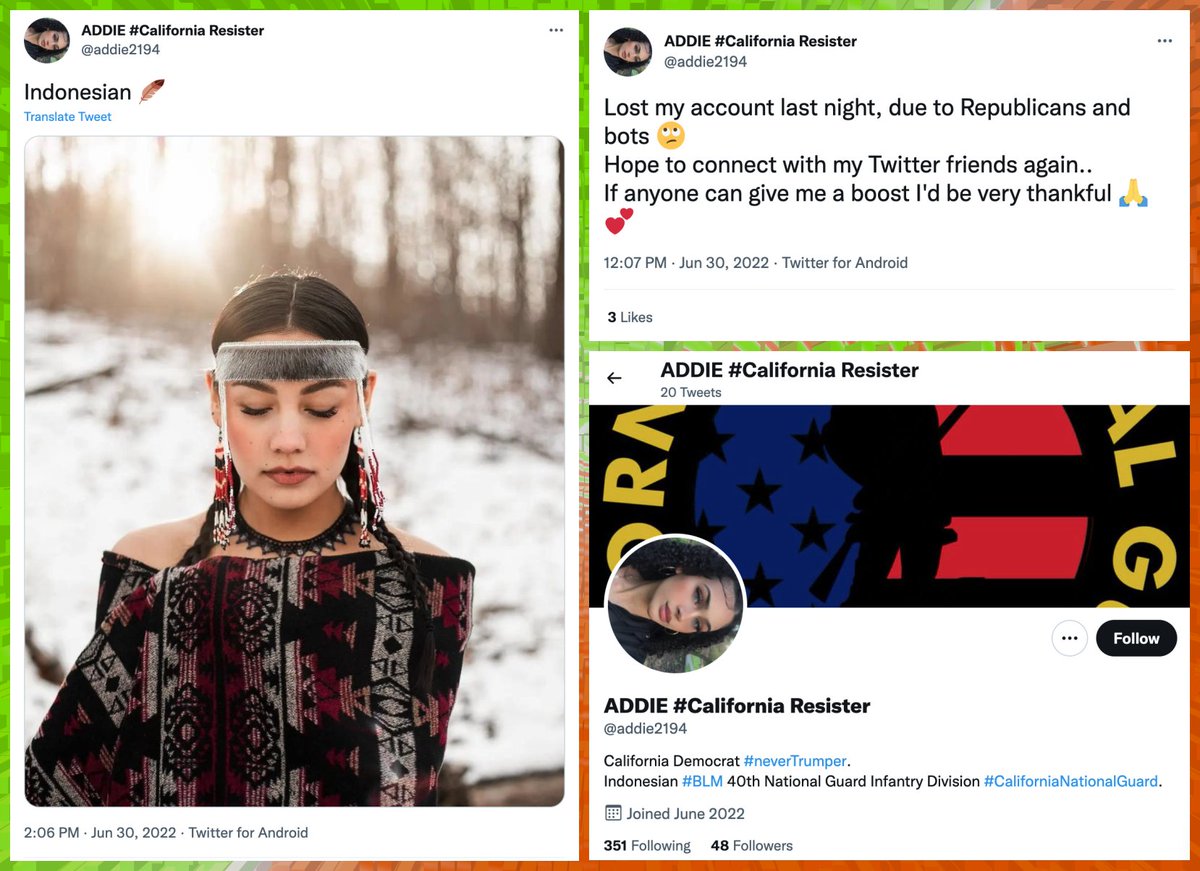
Meet @SophiaM98566027 (permanent ID 1602043736195751937), a Twitter account created in December 2022 with a stolen profile photo that claims to be a Democrat and 12-year military v...
Platforms to Learn Cybersecurity in 2023 (FREE)
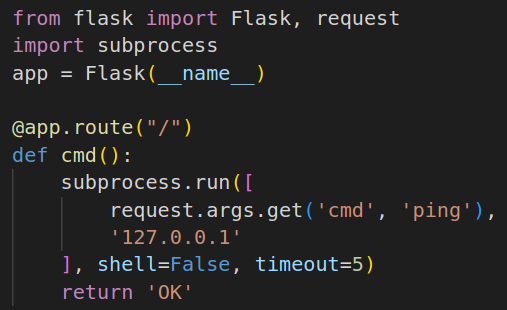
A puzzle for anyone interested. Assuming you have no other access to the server this Flask app runs on, is it possible to get full command execution (e.g. a reverse shell)? #Cyber...

My favorite Google dorks - Part 3: OR - Include both queries & - Require both queries intext: - Appears in the page Example: (site:site:tesla. com | teslamotors. com) & intext:"c...
5 sources to learn smart contract hacking by example. (thread)

1. The Communications and Digital Ministry is investigating the alleged leak of customer data on a website, involving Maybank, Astro, and the Election Commission. Its initial prob...
How twitter scams drain your wallet and NFTs 1. Popular post in appearance post with free airdrop 2. Connect wallet to claim 3. Provide permissions Most wallets won t make it cle...
5 methods to bypass authentication. via @AnonY0gi (thread)

Are you interested in learning reverse engineering in 2023? I've spent the this year studying RE, and I want to share all the resources that helped me along the way in the followin...
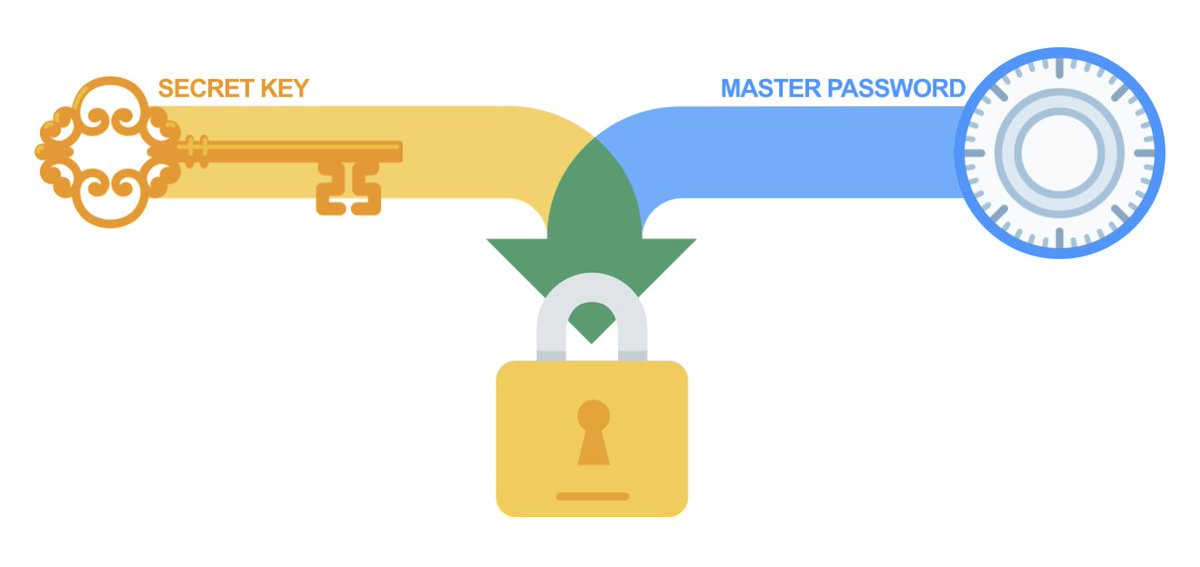
With the breach of LastPass and everyone wondering if their vaults will be impervious to attacks. I thought it might be good time to refresh our understanding on two type of encryp...
Browser wallets protect your private key by encrypting them with a password So even if you download malicious software to your computer, if your wallet is locked - the hacker can...

Day 7️⃣6️⃣ Learn to spot red flags in cybersecurity job descriptions and save yourself a lot of trouble:
Lots of discussion on the LastPass breach. A lot of folks against cloud-centric providers which - if you want assured security, no question.. localized password vaults are the safe...
@LastPass is no longer safe, here's why you must not use it and switch to native password manager from @Google and @Apple.
1/ LASTPASS USERS READ THIS ‼️ Twitter is full of misinformation and bad advice. If you use LastPass, attackers probably have a copy of your vault. CHANGING YOUR MASTER PASSWORD...

Hybrid War: High-tech, Information, and Cyber Conflicts 🧵🧵🧵🧵🧵🧵🧵🧵🧵 Analyses of geopolitical and geostrategic environments have hinted at a reformulation of both the philosophy and...
How I do subdomain enumeration by aggregating multiple tools in a bash script. The script contains the following tools: (thread)
So... The LastPass hack included user's encrypted password vaults. That is pretty horrific. Or at least it sounds horrific. But how bad is it really? If you are using LastPass or...

Paid to Hack! How much money can you make in cybersecurity? (thread)
This single line of bash code will crash your system: :(){ : | : &};: It is a so-called fork bomb, duplicating itself with each call, eventually draining system resources dry. H...
Best 5 repositories for bug hunters and penetration tester | Thread #bugbounty #bugbountytips #infosec
Day 2⃣0⃣/2⃣0⃣ -- [Closing/Summary Of The 20-Day BootCamp] ➡️ The 20-Day BootCamp - Understanding, Detecting, Exploiting & Preventing Different Vulnerabilities. ➡️ Below are the Da...




















