cybersecurity
1012 Threads
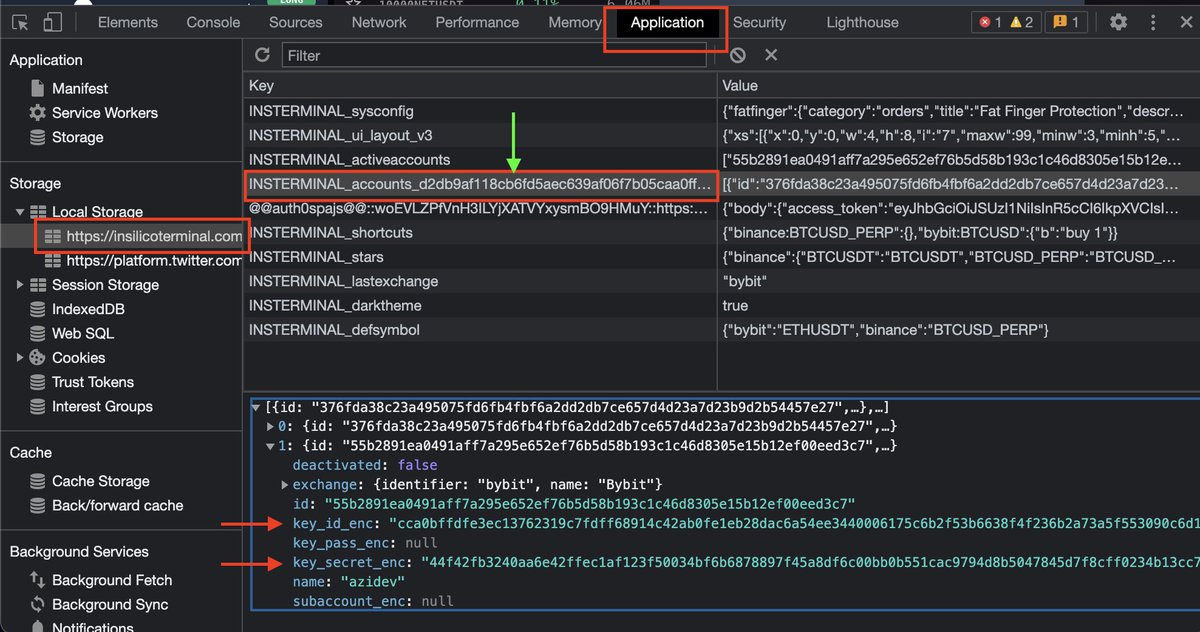
🔑 Some thoughts and comments about API keys in light of the 3commas incident. Seems to be some confusion over what happened there exactly so can't comment. This is the cringiest...
Day 1⃣4⃣/2⃣0⃣ -- [SSRF - Server Side Request Forgery] ➡️ SSRF - allows an attacker to induce the server-side application to make requests to an unintended location. ➡️ Below some o...
Starting salary in Cybersecurity is $60k-$110k/year All it takes get there from ZERO is: - 3 Months - 2 Certs ($700) - 1 Laptop ($300) But you're BROKE. There's still hope! Op...
Next generation cyber-attacks via AI models: (thread)
The 7 Steps of an Effective Offensive Penetration Test: 1. Planning and scoping 2. Information gathering 3. Threat modelling 4. Vulnerability assessment 5. Exploitation 6. Post-ex...
Day 1⃣2⃣/2⃣0⃣ -- [RCE - Remote Code Execution] ➡️ Every Bug Bounty Hunter/Hacker wants to hit an RCE. ➡️ Below some of the best Tips & References for RCE (Feel Free To Share)🧵🧵👇👇 🧵...
The most important things to do as a beginner are: Not trying to learn every single thing at the start. Start slow learn few bugs,work around them get perfect with them and try tho...

Fact Check: How to spot impostor Twitter accounts. Click here to read the full story: https://t.co/U9Qa1KycDu https://t.co/J4ngk06pBj
1) A $TON information thread, there is no judgement call, just facts I've collected this thread in webpage form: https://t.co/sV6TFfxhqC
Hey guys don't attack the power substations ok? Not cool. https://t.co/jJBa4BUJ3O
yeah sadistic psychopaths have never been extremely public people like politicians and celebrities, it's clearly causally linked to pseudonymity https://t.co/aYmewrDOHO
Wanna make a positive impact in cybersecurity? Don't just take or expect everything to be given to you for free, without even just saying thanks. Contribute to the field by being...
From ethical hacking to cybersecurity management, these 9 careers are perfect for you, the aspiring cyber-expert! (no bug bounty involved). 1. Cybersecurity Analyst 2. Penetration...
10 Google chrome extensions for so good you'll feel stupid not knowing them ( All 🆓 ) Not Only #SEO & Content Writing... ⏰Minute

1. At least 5 million people's data have been sold on the bot market to date, with around 50,000 of them being Malaysians, according to the world’s largest VPN service provider....
➡️CyberSecurity/BugBounty Update! ➡️Check thread below 🧵🧵👇👇 #BugBounty #CyberSecurity
List of OSINT tools that can aid your investigation if you come across a suspicious URL or IP address. 🧵👇 #osint #infosec #bugbounty #hacking #cybersecurity #pentest
If you want to get into smart contract hacking, a very lucrative business, you must be aware of the following vulnerabilities: 1. Reentrancy Attacks 2. Integer Overflow and Underf...
GraphQL flaws you, as a cybersecurity professional, must be aware of: 1. Improper validation & sanitization of input 2. Lack of access controls 3. Lack of authentication 4. Over/U...

My job is to find your contact info online. Here's how to delete your digital & real estate footprint so I can't 🧵:
Day 1⃣2⃣/2⃣0⃣ -- [Broken Access Control Vulnerabilities & Broken Authentication and Session Management] ➡️ Detecting & Exploiting IDOR, Privilege Escalation e.t.c ➡️ Below some of...
1/ We've all heard of the importance of keeping our digital assets safe. But what if you forget or lose your password or private key or god forbid a malicious actor gets ahold of y...

"https://t.co/I0aC5yrSTn: Top #security Tools" #cybersecurity #cybersecuritytips #bugbounty #bugbountytips #hacking #infosec #security #informationsecurity #pentesting #pentest #O...
5 PRO tips to use in your enumeration for Active Directory pentesting: (thread)















