cybersecurity
1012 Threads
Full infection flow, brought to you by OpwnAI, as affectionately dubbed by @_CPResearch_ (thread)
AI is NEVER going to replace your Cybersecurity job. In fact, IT CAN'T. Let me explain:
How to use gobuster in pentesting. I used #AI to summarize my video (results below). (thread)

Bug Bounty Reports in Thread 🧵 #bugbounty #infosec Bug Type : Reflected XSS Org : Shopify Bounty : $2000 Read For More 🧵:👇
If you are interested in any of these: Tech🧑💻 Jobs 💰 Cloud ☁️ Certifications 🏆 Linux🐧 DevOps 🛠️ Programming 🖥️ Full-Stack 💻 Security 🔐 Data 📊 ML / AI 🤖 Tools💡 Make sure to subsc...
Starting salary in Cybersecurity is $60k-$110k/year ABSOLUTELY NO ONE makes it without knowing LINUX But LINUX is a HUGE TOPIC Here's 3 FREE resources to give you EXACTLY what y...

🧵Announcing our Top 10 Blog Posts of 2022! See what blogs were the most viewed this year. 👀👇 https://t.co/Ye15LSDuUR
Crypto hackers have stolen $3+ billion in 2022. If you are not careful, you'll be next. This thread shares 9 security practices that everyone should know.
30 cybersecurity search engines for researchers: 1. Dehashed—View leaked credentials. 2. SecurityTrails—Extensive DNS data. 3. DorkSearch—Really fast Google dorking. 4. ExploitDB—...

5 tips on how I used Burp Pro in my 85+ pentests in 2022: (thread)
1.THREAD: Twitter Files Supplemental
what can @RealTryHackMe learn from @hackthebox_eu? I asked #chatgpt. And here's what I got. (thread)
Ready to level up your DeFi game? 🤔 These simple but effective tips will help you become a smarter🧠 and more successful player👨💻 in the DeFi space. 🧵🧵 https://t.co/9kUe4ZIEra
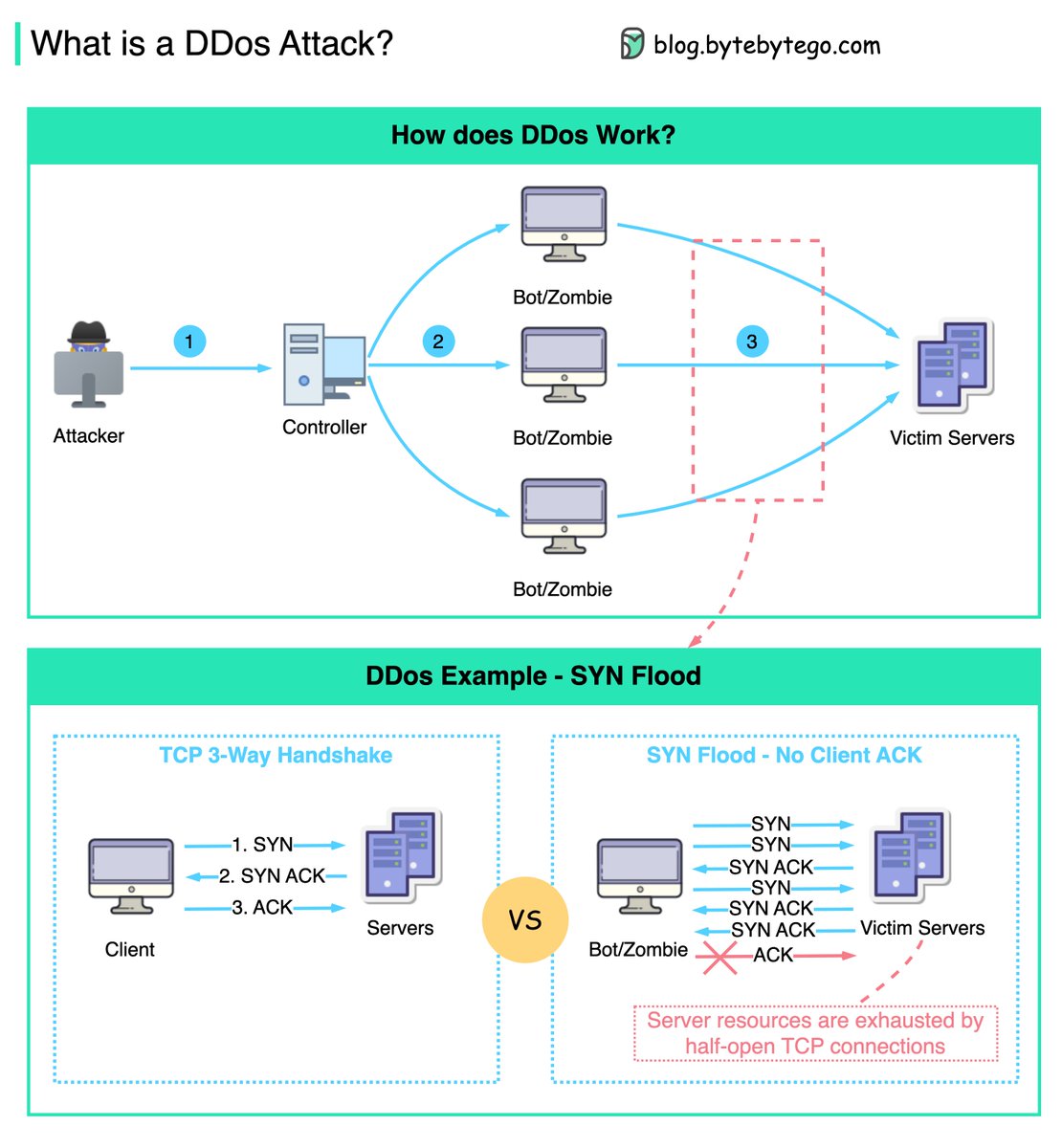
/1 What is a DDos (Distributed Denial-of-Service) Attack? Why is it hazardous to the services? Here is an example of how DDoS works. https://t.co/Mxwx6pYsac
My top 5 favorite #bugbounty platforms: (thread)

damn, the level of sophistication that attacks can reach. I didn't know this, thanks @RealTryHackMe (thread) https://t.co/KzXGpApoQY
Improper Generic Authentication Bug Reports ➡️ Username restriction bypass with SSL client authentication https://t.co/7csCS9sGLJ ➡️ Unauthenticated access {Shopify} : https://t....
Day 1⃣6⃣/2⃣0⃣ -- [CSRF - Cross Site Request Forgery] ➡️ CSRF - forces authenticated users to submit a request to an application in which they are currently authenticated. ➡️ Below...
2. Source Code Analysis/Review Be it a mobile or web app, it’s never a bad idea to look into the code, in addition to all the dynamic testing. I often find a lot of insecurities...
In a world overloaded with information, "how to" is not so valuable anymore. "how I" is the new valuable approach. Here are 5 reasons: (thread)
When I got doxxed I had schizos calling my family & posting my address & pictures of my kids on Twitter - they weren't even forced to delete the tweets, let alone banned from the p...
Day 1⃣5⃣/2⃣0⃣ -- [XSS - Cross Site Scripting] ➡️ XSS - allows attackers to inject malicious executable scripts into the code of a trusted application or website. ➡️ Below some of t...
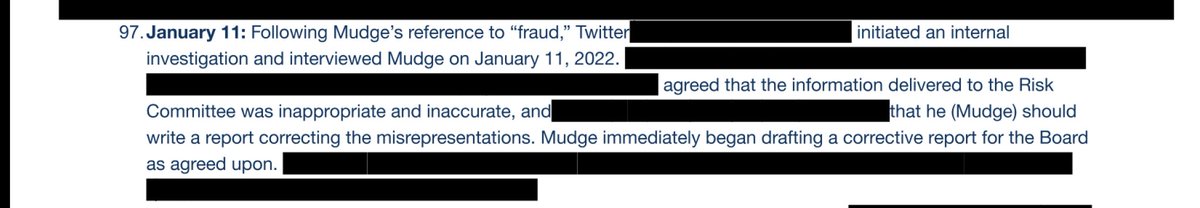
The stuff uncovered in the Twitter whistleblower report is much crazier than anything in the "Twitter files" but it's much less politically/tribally salient so it got no attention....
6 under-the-radar resources to master authentication vulnerabilities: 1. OWASP Auth Cheat Sheet 2. SANS ISC 3. NIST Special Publication 800-63B 4. CERT Vulnerability Note Database...













